Summary
Microsoft is aware of PetitPotam which can potentially be used to attack Windows domain controllers or other Windows servers. PetitPotam is a classic NTLM Relay Attack, and such attacks have been previously documented by Microsoft along with numerous mitigation options to protect customers. For example: Microsoft Security Advisory 974926.
To prevent NTLM Relay Attacks on networks with NTLM enabled, domain administrators must ensure that services that permit NTLM authentication make use of protections such as Extended Protection for Authentication (EPA) or signing features such as SMB signing. PetitPotam takes advantage of servers where Active Directory Certificate Services (AD CS) is not configured with protections for NTLM Relay Attacks. The mitigations below outline to customers how to protect their AD CS servers from such attacks.
You are potentially vulnerable to this attack if you are using Active Directory Certificate Services (AD CS) with any of the following services:
-
Certificate Authority Web Enrollment
-
Certificate Enrollment Web Service
Mitigation
If your environment is potentially affected, we recommend the following mitigations:
Primary mitigation
We recommend enabling EPA and disabling HTTP on AD CS servers. Open the Internet Information Services (IIS) Manager and do the following:
-
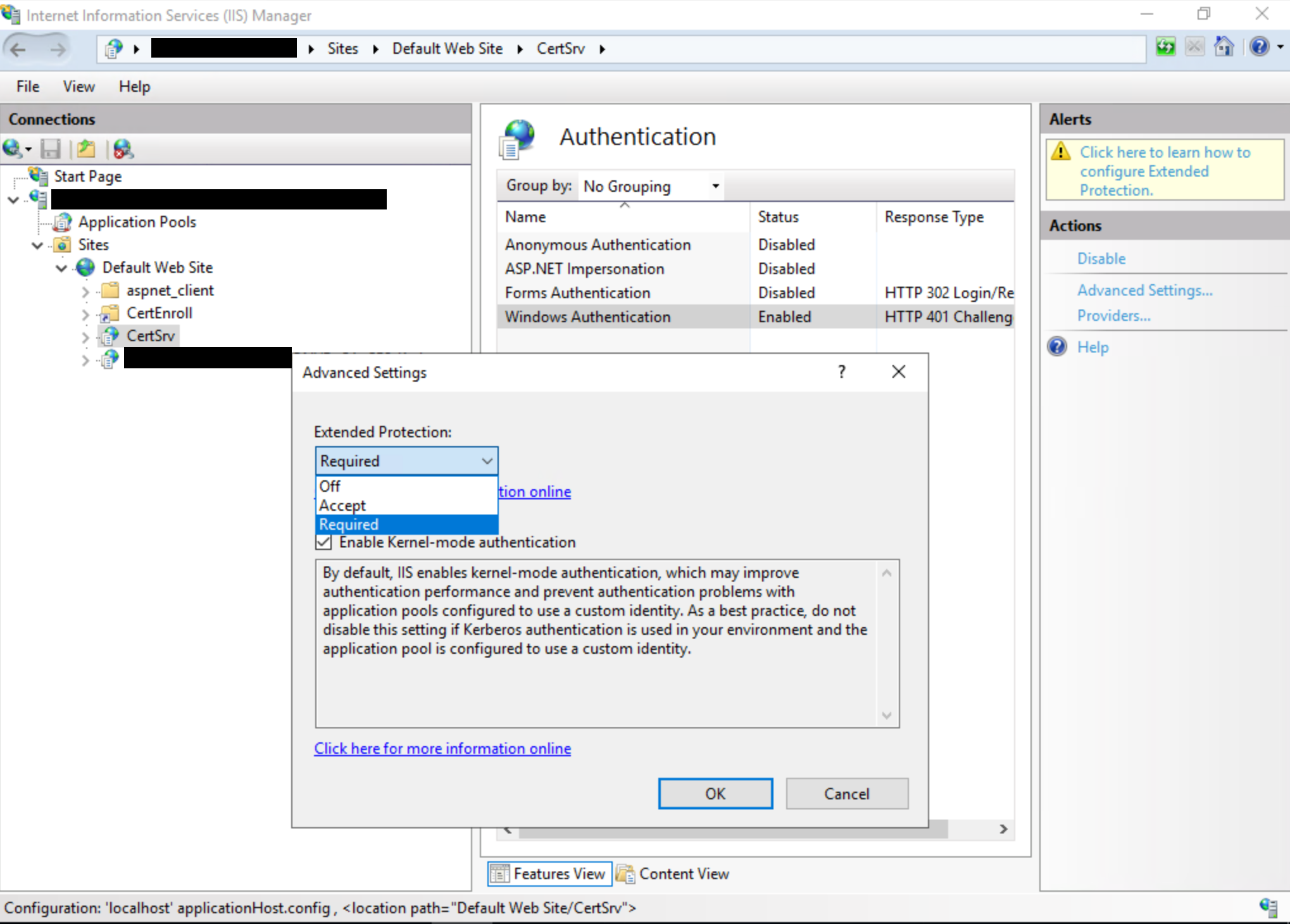
Enable EPA for Certificate Authority Web Enrollment, Required being the more secure and recommended option:
-
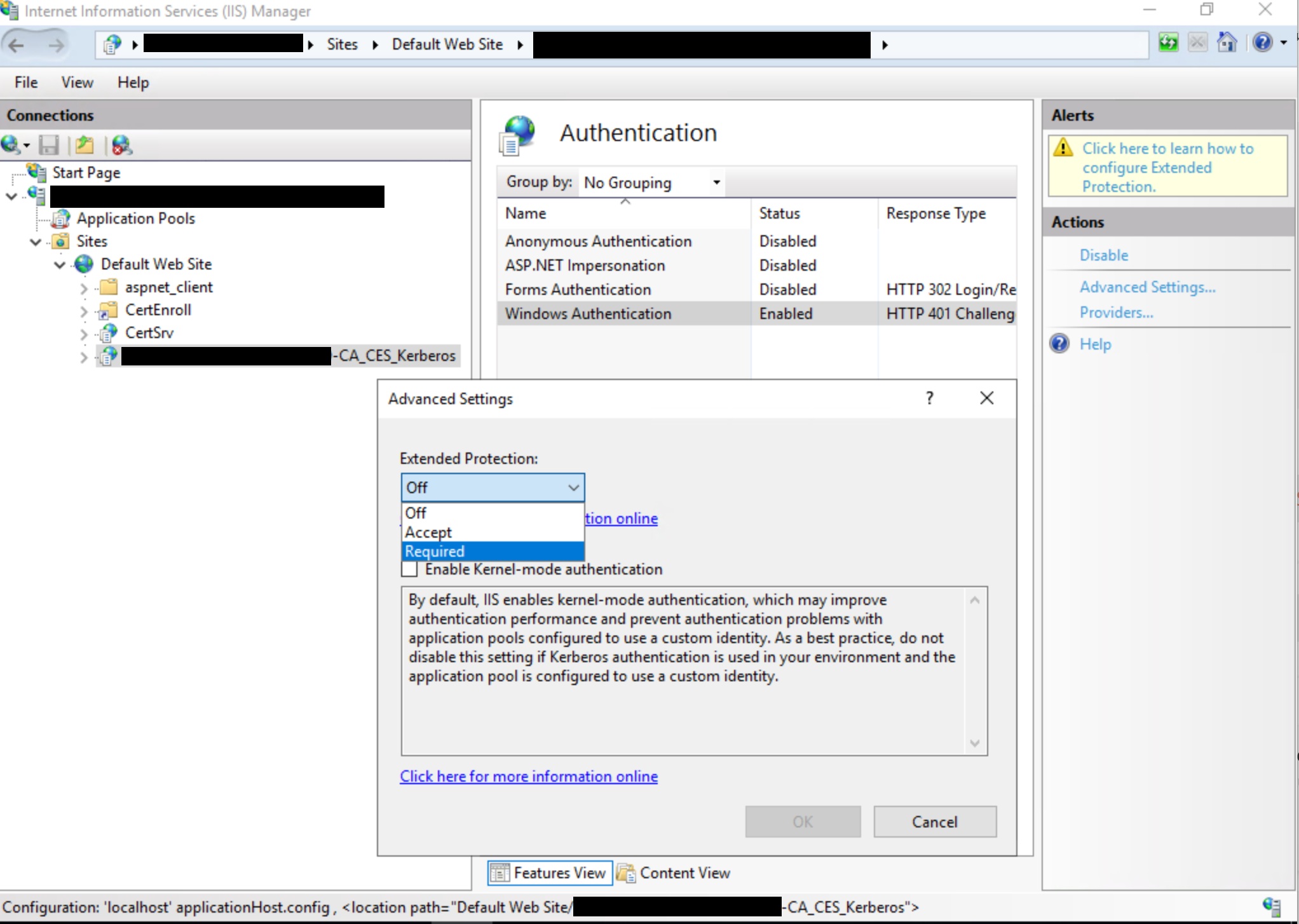
Enable EPA for Certificate Enrollment Web Service, Required being the more secure and recommended option:
Note: The Always setting is used when the UI is set to Required, which is the recommended and most secure option.
For more information on the options available for extendedProtectionPolicy, see <transport> of <basicHttpBinding>. The most likely used settings are as follows:
<binding name="TransportWithHeaderClientAuth"> <security mode="Transport"> <transport clientCredentialType="Windows"> <extendedProtectionPolicy policyEnforcement="Always" /> </transport> <message clientCredentialType="None" establishSecurityContext="false" negotiateServiceCredential="false" /> </security> <readerQuotas maxStringContentLength="131072" /> </binding> -
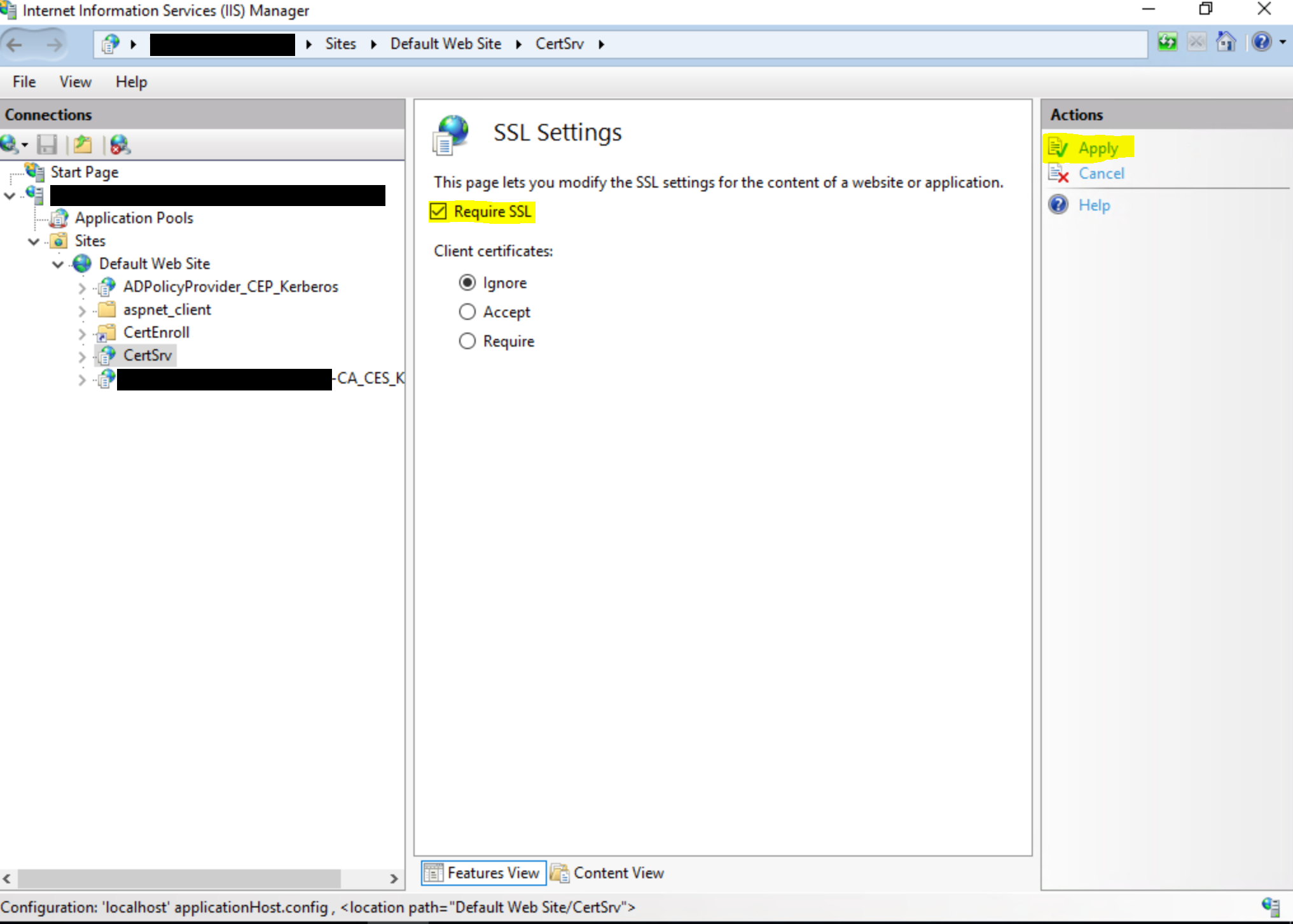
Enable Require SSL, which will enable only HTTPS connections.
Important: After completing the above steps, you will need to restart IIS to load the changes. To restart IIS, open an elevated Command Prompt window, type the following command, and then press ENTER:iisreset /restart Note This command stops all IIS services that are running and then restarts them.
Additional mitigation
In addition to the primary mitigations, we recommend you disable NTLM authentication where possible. The following mitigations are listed in order from more secure to less secure:
-
Disable NTLM Authentication on your Windows domain controller. This can be accomplished by following the documentation in Network security: Restrict NTLM: NTLM authentication in this domain.
-
Disable NTLM on any AD CS Servers in your domain using the group policy Network security: Restrict NTLM: Incoming NTLM traffic. To configure this GPO, open Group Policy and go to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options and set Network security: Restrict NTLM: Incoming NTLM traffic to Deny All Accounts or Deny All domain accounts. If needed, you can add exceptions as necessary using the setting Network security: Restrict NTLM: Add server exceptions in this domain.
-
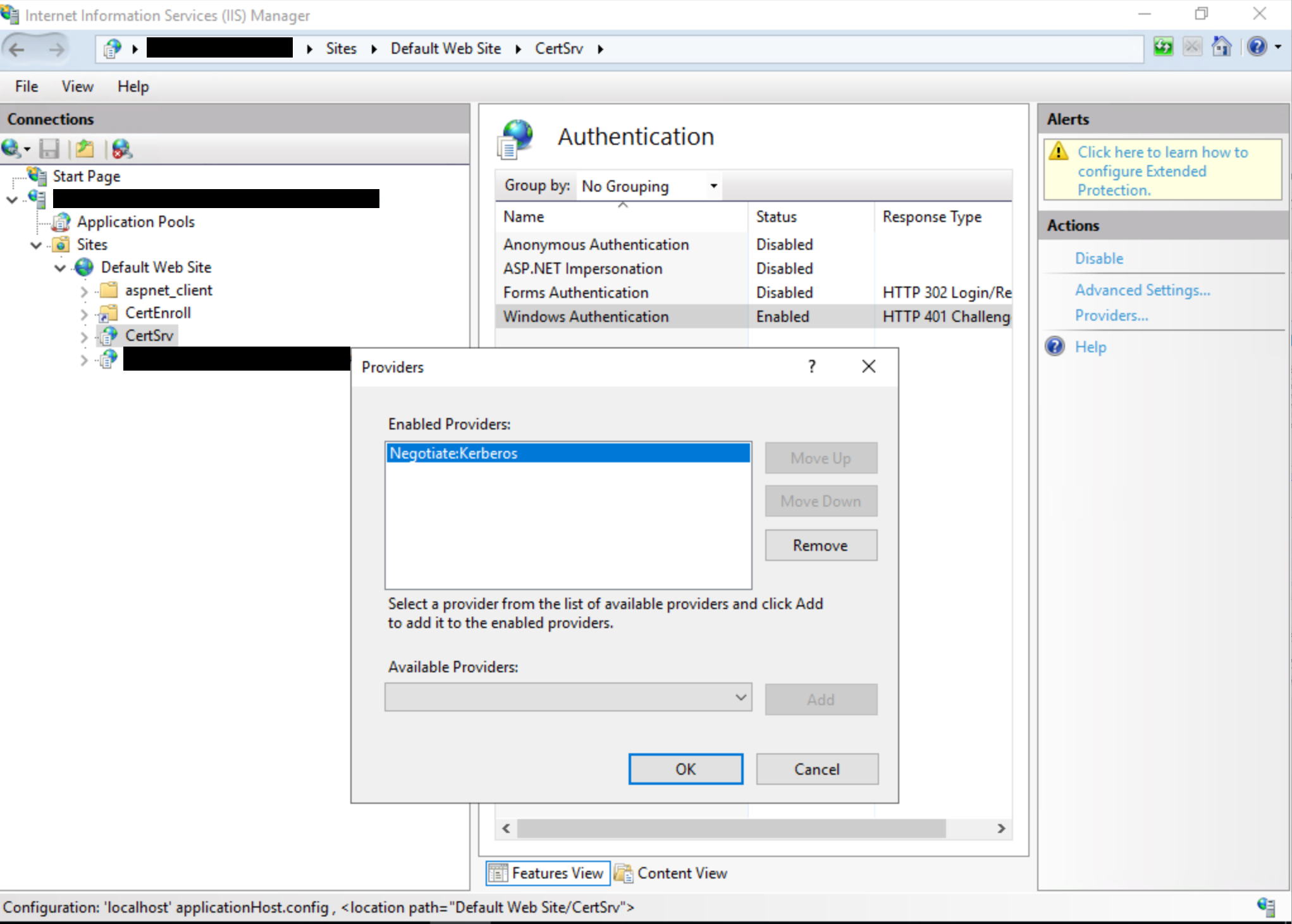
Disable NTLM for Internet Information Services (IIS) on AD CS Servers in your domain running the "Certificate Authority Web Enrollment" or "Certificate Enrollment Web Service" services.
To do so open IIS Manager UI, set Windows authentication to Negotiate:Kerberos:
Important: After completing the above steps, you will need to restart IIS to load the changes. To restart IIS, open an elevated Command Prompt window, type the following command, and then press ENTER:iisreset /restart Note This command stops all IIS services that are running and then restarts them.
For more information, please see Microsoft Security Advisory ADV210003