Microsoft Intune method of Secure Boot for Windows devices with IT-managed updates
Applies To
Original Published Date: December 4, 2025
KB ID: 5073196
This article has guidance for:
-
Organizations that have their own IT department managing Windows devices and updates.
Note: If you are an individual who owns a personal Windows device, please see the article Windows devices for home users, businesses, and schools with Microsoft-managed updates.
Availability of this support
-
November 11, 2025: For versions of Windows 11 and Windows 10 still in support.
In this Article:
Introduction
This document describes the support for deploying, managing, and monitoring the Secure Boot certificate updates using the Microsoft Intune. The settings consist of:
-
The ability to trigger deployment on a device
-
A setting to opt in/opt out of high-confidence buckets
-
A setting to opt in/opt out of Microsoft managing updates
Microsoft Intune configuration method
This method offers Secure Boot setting using Microsoft Intune that domain administrators can set to deploy Secure Boot updates to all domain-joined Windows clients. In addition, two Secure Boot assists can be managed with opt in/opt out settings.
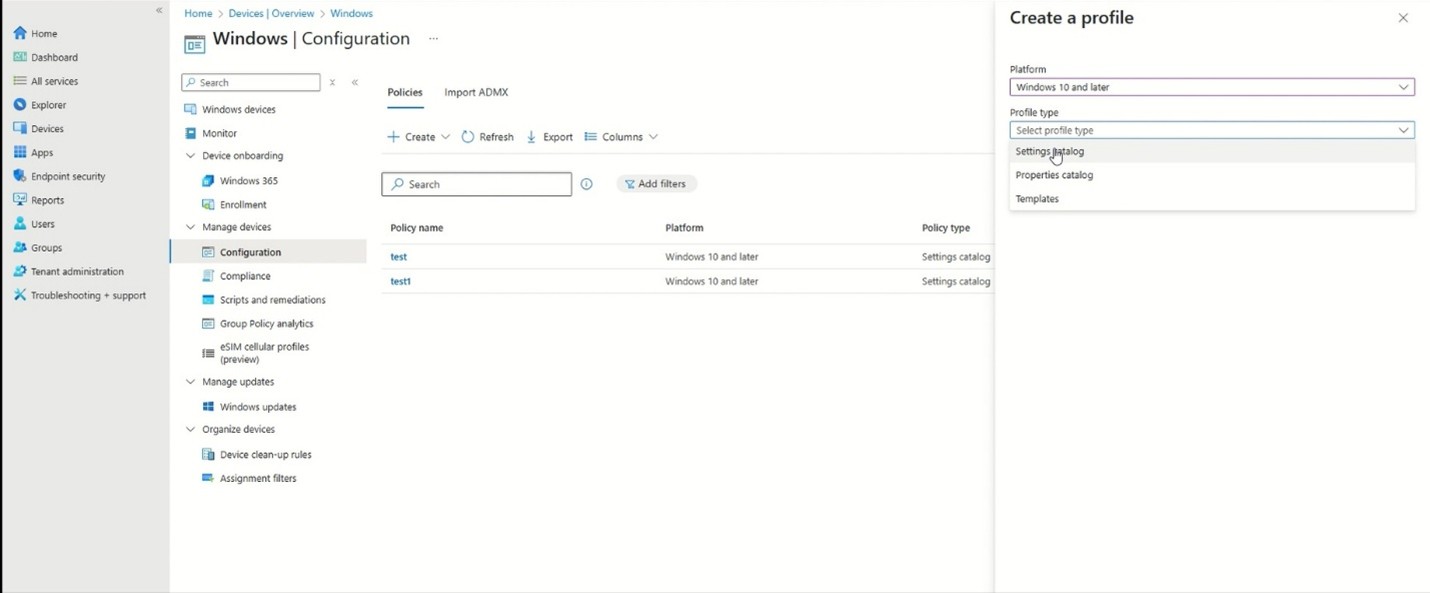
In Microsoft Intune,
-
Under Devices > Manage devices, select Configuration.
-
Select Create and select New Policy.
-
Go to Create a profile in the right-hand pane.
-
Fill in Platform with Windows 10 and later.
-
-
Select the Settings Catalog under the Profile Type.
-
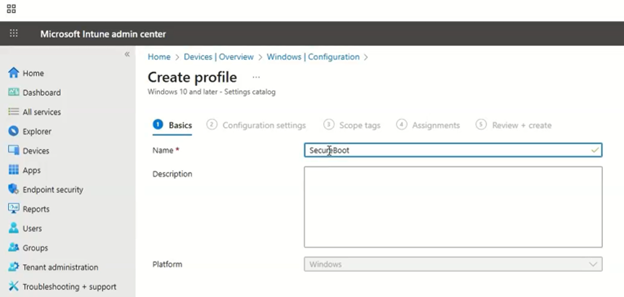
Begin creating a profile by giving the profile a name. In this example, we are using “Secure Boot” as the name. Press Next.
-
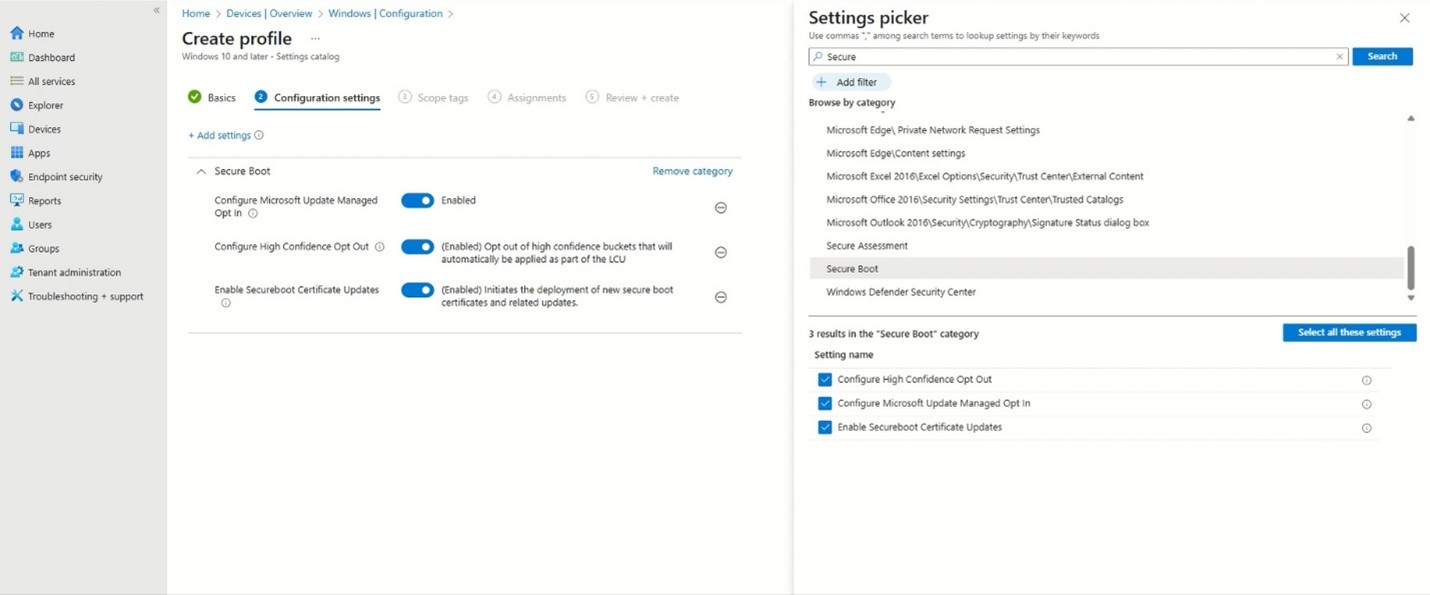
Under Configuration settings, select Add settings and use the Settings picker to find the Secure Boot settings by searching for Secure Boot. You should see three settings in the Secure Boot category. These are the same settings described in the Registry key updates for Secure Boot: Windows devices with IT-managed updates and the Group Policy Objects (GPO) method of Secure Boot for Windows devices with IT-managed updates documents.
-
Enable Secureboot Certificate Updates is selected by default and enabled.
-
The opt in and opt out settings described below can be configured to suite your environment and deployment needs.
-
-
Finish the profile for the devices that will use these settings.
Setting Description
Configure Microsoft Update Managed Opt In
Microsoft Intune Setting Name: Configure Microsoft Update Managed Opt In
Description: This policy allows enterprises to participate in a Controlled Feature rollout of Secure Boot certificate update managed by Microsoft.
-
Enabled: Microsoft assists with deploying certificates to devices enrolled in the rollout.
-
Disabled (default): No participation in controlled rollout.
Requirements:
-
Device must send required diagnostic data to Microsoft. For details, see Configure Windows diagnostic data in your organization - Windows Privacy | Microsoft Learn.
-
Corresponds to the registry key MicrosoftUpdateManagedOptIn.
Configure High Confidence Opt-Out
Microsoft Intune Setting Name: Configure High Confidence Opt-Out
Description: This policy controls whether Secure Boot certificate updates are applied automatically through Windows monthly security and non-security updates. Devices that Microsoft has validated as capable of processing Secure Boot variable updates will receive these updates as part of cumulative monthly updates and apply them automatically. Because not all hardware and firmware combinations can be exhaustively validated, Microsoft relies on targeted testing and diagnostic data to determine device readiness. Only devices with sufficient diagnostic data can be considered with high confidence; if diagnostic data is unavailable for a given device, it cannot be classified with high confidence.
-
Enabled: Automatic deployment through monthly updates is blocked.
-
Disabled (default): Devices that have validated their update results will automatically get certificate updates as part of the monthly updates.
Notes:
-
Intended devices are confirmed to process updates successfully.
-
Configure this policy to manage automatic deployment through monthly updates.
-
Corresponds to the registry key HighConfidenceOptOut.
Enable Secureboot Certificate Updates
Microsoft Intune Setting Name: Enable Secureboot Certificate Updates
Description: This policy controls whether Windows initiates the Secure Boot certificate deployment process on devices.
-
Enabled: Windows automatically begins deploying updated Secure Boot certificates.
-
Disabled (default): Windows does not deploy certificates automatically.
Notes:
-
The task that processes this setting runs every 12 hours. Some updates may require a restart to complete safely.
-
Once certificates are applied to firmware, they cannot be removed from Windows. Clearing certificates must be done through the firmware interface.
-
Corresponds to the registry key AvailableUpdates.
Resources
See also Registry key updates for Secure Boot: Windows devices with IT-managed updates for details on the UEFICA2023Status and UEFICA2023Error registry keys for monitoring device results.
See Secure Boot DB and DBX variable update events for events useful in understanding the status of devices, device attributes, and device bucket IDs. Pay special attention to events 1801 and 1808 described on the events page.