Summary
This article helps identify and remedy problems in devices that are affected by the vulnerability that is described in Microsoft Security Advisory ADV170012.
This process focuses on the following Windows Hello for Business (WHFB) and Azure AD (AAD) usage scenarios offered by Microsoft:
-
Azure AD join
-
Hybrid Azure AD join
-
Azure AD registered
More Information
Identify your AAD usage scenario
-
Open a Command Prompt window.
-
Get the device state by running the following command:dsregcmd.exe /status
-
In the command output, examine the values of the properties that are listed in the following table to determine your AAD usage scenario.
Property
Description
AzureAdJoined
Indicates whether the device is joined to Azure AD.
EnterpriseJoined
Indicates whether the device is joined to AD FS. This is part of an on-premises-only customer scenario where Windows Hello for Business is deployed and managed on-premises.
DomainJoined
Indicates whether the device is joined to a traditional Active Directory Domain.
WorkplaceJoined
Indicate whether the current user has added a work or school account to their current profile. This is known as Azure AD registered. This setting is ignored by the system if the device is AzureAdJoined.
Hybrid Azure AD joined
If DomainJoined and AzureAdJoined are yes, the device is Hybrid Azure AD joined. Therefore, the device is joined to an Azure Active Directory and a traditional Active Directory Domain.
Workflow
Deployments and implementations may vary across organizations. We designed the following workflow to provide the tools that you need to develop your own internal plan to mitigate any affected devices. The workflow has the following steps:
-
Identify affected devices. Search your environment for affected trusted platform modules (TPMs), keys, and devices.
-
Patch the affected devices. Remedy effects on identified devices by following the scenario-specific steps that are listed in this article.
Note on clearing TPMs
Because trusted platform modules are used to store secrets that are used by various services and applications, clearing the TPM can have unforeseen or negative business impacts. Before clearing any TPM, be sure to investigate and validate that all services and applications that use TPM-backed secrets have been properly identified and prepared for secret deletion and recreation.
How to identify affected devices
To identify affected TPMs, refer to Microsoft Security Advisory ADV170012.
How to patch affected devices
Use the following steps on the affected devices according to your AAD usage scenario.
-
Make sure that a valid local admin account exists on the device or create a local admin account.
Note: It is a recommended practice to verify that the account is working by signing in to the device by using the new local admin account and confirm correct permissions by opening an elevated command prompt.
-
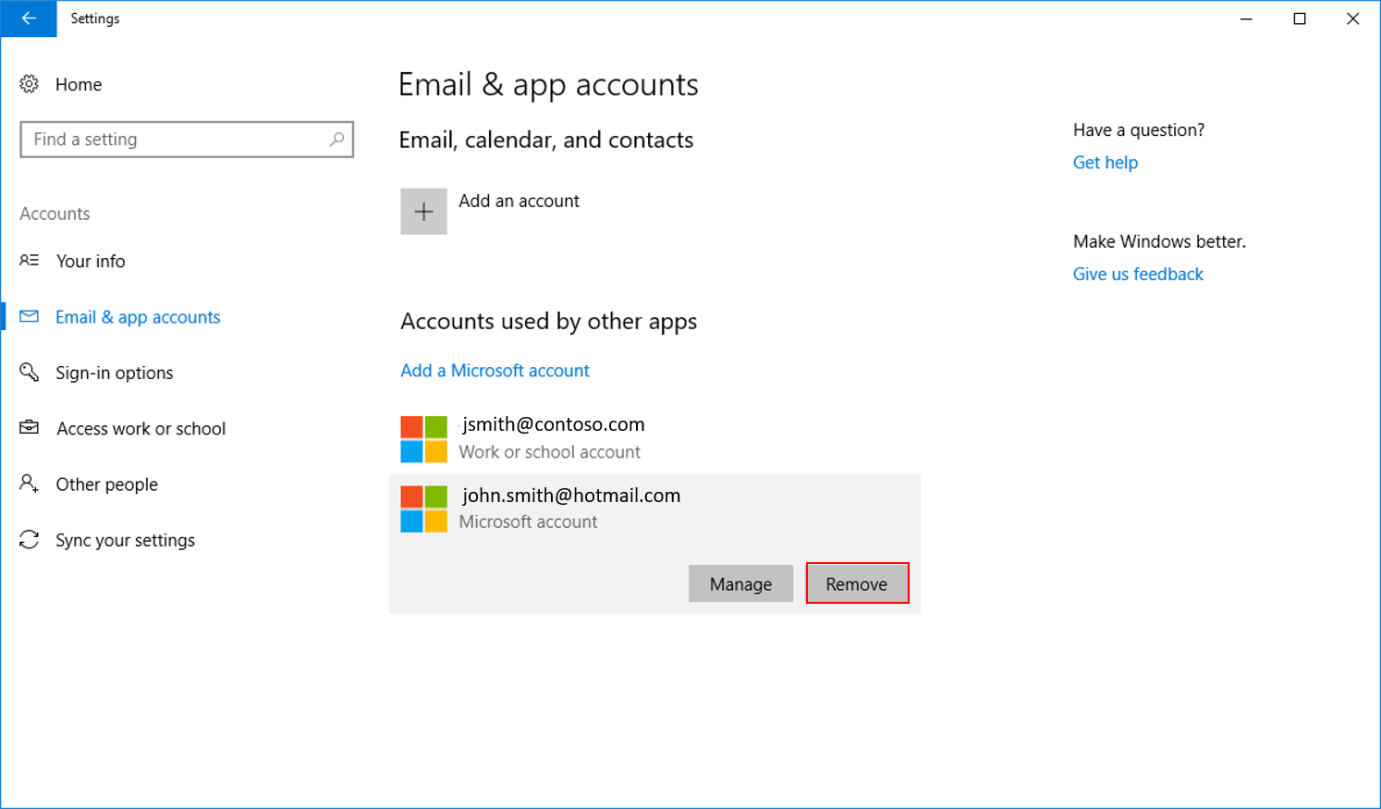
If you have signed in with a Microsoft account on the device, go to Settings > Accounts > Email & app accounts and remove the connected account.
-
Install a firmware update for the device.
Note: Follow your OEM’s guidance for applying the TPM firmware update. See step 4: "Apply applicable firmware updates," in Microsoft Security Advisory ADV170012 for information about how to obtain the TPM update from your OEM.
-
Unjoin the device from Azure AD.
Note: Make sure that your BitLocker key is securely backed up somewhere other than the local computer before you continue.
-
Go to Settings > System > About, and then click Manage or disconnect from work or school.
-
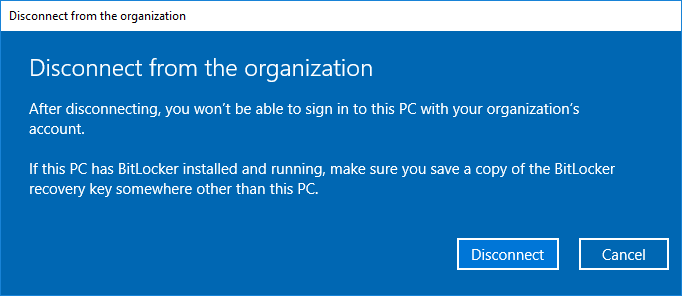
Click Connected to <AzureAD>and click Disconnect.
-
Click Yes when you are prompted for acknowledgment.
-
Click Disconnect when you are prompted to "Disconnect from the organization."
-
Enter the local admin account information for the device.
-
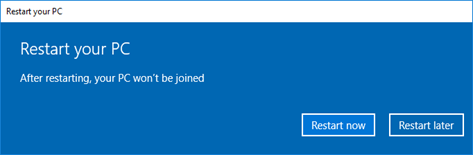
Click Restart Later.
-
-
Clear the TPM.
Notes:
-
Clearing the TPM will remove all keys and secrets that are stored on your device. Make sure that other services that are utilizing the TPM are suspended or validated prior to proceeding.
-
Windows 8 or later: BitLocker is automatically suspended if you use either of the two recommended methods for clearing your TPM, below.
-
Windows 7: Manual suspension of BitLocker is needed before proceeding. (See more information about suspending BitLocker.)
-
To clear the TPM, use one of the following methods:
-
Use the Microsoft Management Console.
-
Press Win + R, type tpm.msc and click OK.
-
Click Clear TPM.
-
-
Run the Clear-Tpm cmdlet.
-
-
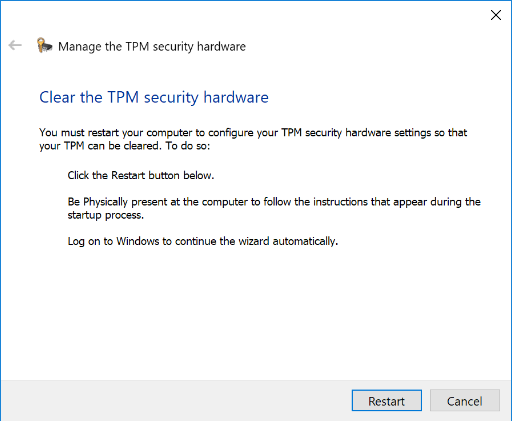
Click Restart.
-
-
After the device restarts, sign in to the device by using the local admin account.
-
Rejoin the device to Azure AD. You may be prompted to set up a new PIN at the next sign-in.
-
If you signed in by using a Microsoft account on your device, go to Settings > Accounts > Email & app accounts and remove the connected account.
-
From an elevated command prompt, run the following command:dsregcmd.exe /leave /debug
Note: Command output should indicate AzureADJoined: No.
-
Install a firmware update for the device.
Note: Note Follow your OEM’s guidance for applying the TPM firmware update. See step 4: "Apply applicable firmware updates," in Microsoft Security Advisory ADV170012 for information about how to obtain the TPM update from your OEM.
-
Clear the TPM.
Notes:
-
Clearing the TPM will remove all keys and secrets that are stored on your device. Make sure that other services that are utilizing the TPM are suspended or validated prior to proceeding.
-
Windows 8 or later: BitLocker is automatically suspended if you use either of the two recommended methods for clearing your TPM, below.
-
Windows 7: Manual suspension of BitLocker is needed before proceeding. (See more information about suspending BitLocker.)
-
To clear the TPM, use one of the following methods:
-
Use the Microsoft Management Console.
-
Press Win + R, type tpm.msc and click OK.
-
Click Clear TPM.
-
-
Run the Clear-Tpm cmdlet.
-
-
Click Restart.Note You may be prompted to clear the TPM at startup.
-
When the device starts, Windows generates new keys and automatically rejoins the device to Azure AD. During this time, you may continue to use the device. However, access to resources such as Microsoft Outlook, OneDrive, and other applications that require SSO or Conditional Access policies may be limited.
Note If you use a Microsoft account, you must know the password.
-
Install a firmware update for the device.
Note: Follow your OEM’s guidance for applying the TPM firmware update. See step 4: "Apply applicable firmware updates," in Microsoft Security Advisory ADV170012 for information about how to obtain the TPM update from your OEM.
-
Remove the Azure AD work account.
-
Go to Settings > Accounts > Access work or school, click your work or school account, and then click Disconnect.
-
Click Yes in the prompt to confirm the disconnection.
-
-
Clear the TPM.
Notes:
-
Clearing the TPM will remove all keys and secrets that are stored on your device. Make sure that other services that are utilizing the TPM are suspended or validated prior to proceeding.
-
Windows 8 or later: BitLocker is automatically suspended if you use either of the two recommended methods for clearing your TPM, below.
-
Windows 7: Manual suspension of BitLocker is needed before proceeding. (See more information about suspending BitLocker.)
-
To clear the TPM, use one of the following methods:
-
Use the Microsoft Management Console.
-
Press Win + R, type tpm.msc and click OK.
-
Click Clear TPM.
-
-
Run the Clear-Tpm cmdlet.
-
-
Click Restart.Note You may be prompted to clear your TPM at startup.
-
If you used a Microsoft account that has a PIN, you have to sign in to the device by using the password.
-
Add the work account back to the device.
-
Go to Settings > Accounts > Access work or school and click Connect.
-
Enter your work account, and then click Next.
-
Enter your work account and password, and then click Sign in.
-
If your organization has configured Azure Multi-Factor Authentication for joining devices to Azure AD, provide the second factor before you continue.
-
Validate that the information displayed is correct, and then click Join. You should see the following message:You’re all set! We’ve added your account successfully You now have access to your organizations apps and services.
-
-