Azure Stack
Build and run hybrid apps across datacenters, edge locations, remote offices, and the cloud.

Azure Stack solutions
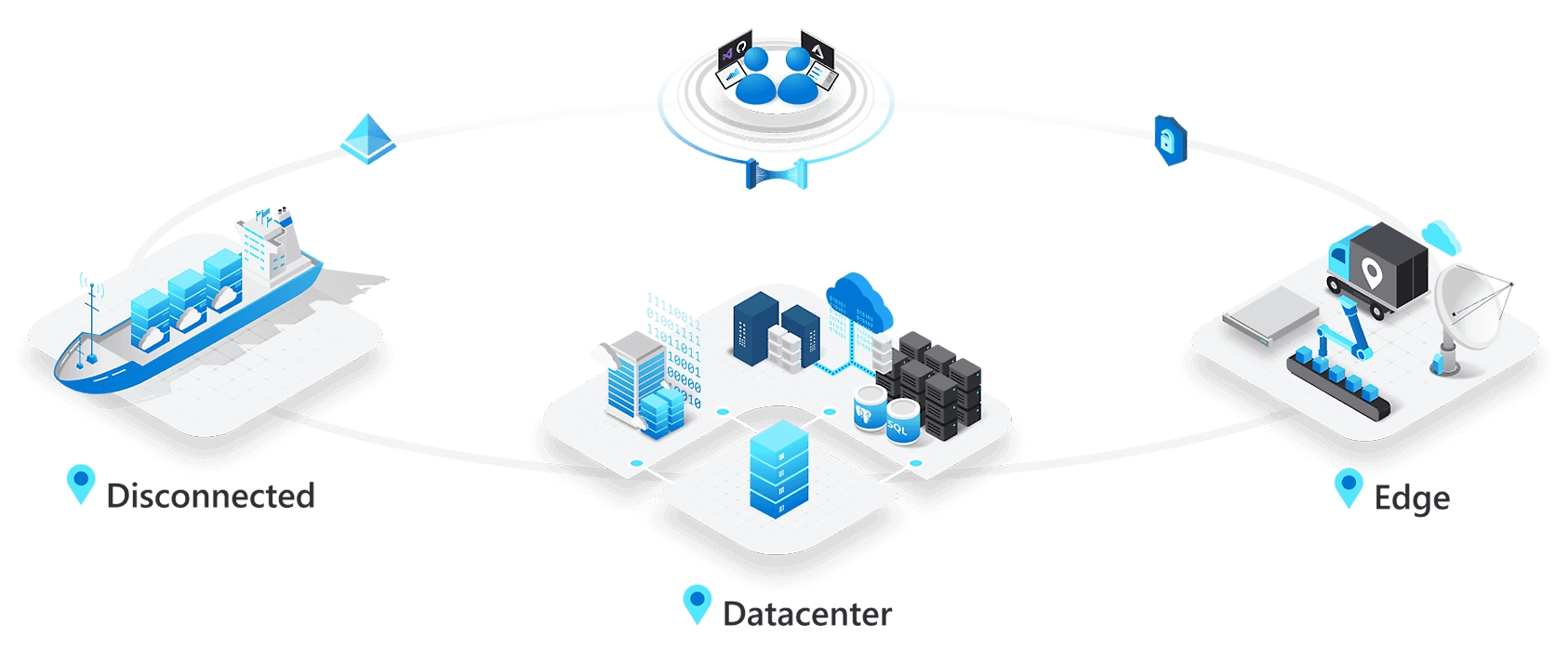
Extend Azure services and capabilities to your environment of choice—from the datacenter to edge locations and remote offices—with Azure Stack. Build, deploy, and run hybrid and edge computing apps consistently across your IT ecosystem, with flexibility for diverse workloads.
Azure Stack Edge
-
Run edge-computing workloads
Get rapid insights with an Azure managed appliance using compute and hardware-accelerated machine learning at edge locations for your Internet of Things (IoT) and AI workloads.
Use Azure Stack Edge for:
-
Machine learning at the edge
-
Edge and IoT solutions
-
Network data transfer from edge to cloud

Azure Stack HCI
-
Modernize your datacenter
Refresh your virtualization host using a hybrid and hyperconverged solution integrated with Azure.
Use Azure Stack HCI for:
-
Scalable virtualization and storage
-
Modernizing on-premises architecture
-
Remote branch offices
-
High-performance workloads

Azure Stack Hub
-
Use cloud services on-premises
Run your own private, autonomous cloud—connected or disconnected with cloud-native apps using consistent Azure services on-premises.
Use Azure Stack Hub for:
-
Connected and disconnected scenarios
-
App modernization

See what ‘the art of the possible’ means to your business
Azure Stack is a portfolio of products that extend Azure services and capabilities to your environment of choice—from the datacenter to edge locations and remote offices. Build and deploy hybrid and edge computing applications and run them consistently across location boundaries. See how Azure Stack gives you the flexibility to address your diverse workloads.

Azure Stack for industries
Accelerate innovation and help protect customer data
Reduce unused capital expenses, access on-demand capacity, and extend your geographic reach with a hybrid cloud strategy on Azure Stack.
-
Meet regulatory and data sovereignty requirements
Streamline compliance with industry, government, and company regulations by running cloud apps on-premises—and help keep your data, apps, and identities secure.
-
Modernize financial apps
Boost the efficiency of your mission-critical apps, help mitigate risks, make better business decisions, and personalize customer experiences with Azure services, containers, serverless, and microservices.
-
Speed up cloud migration
Simplify your transition to the cloud and run cloud apps in an on-premises environment with Azure migration tools, resources, programs, and training.
Improve citizen services and meet privacy requirements
Efficiently provide outstanding citizen services by innovating faster and meeting your data privacy requirements.
-
Update and extend legacy apps
Take advantage of enhanced security, scalability, and flexibility by extending legacy apps to the cloud—and improve the performance of on-premises apps that aren't yet ready for the cloud.
-
Improve citizen services
Provide practical, predictive, and efficient services for citizens by enhancing your on-premises app and database performance.
-
Meet compliance regulations
Adhere to specific data compliance, regulatory, and policy requirements by using a common set of tools for building and managing data and apps.
Build, deploy, and run intelligent apps anywhere
Consistently run diverse workloads and extend Azure capabilities almost anywhere—including datacenter, edge, and remote office locations.
-
Bring the cloud to your factory floor
Streamline your operations and increase your efficiency by running Azure services at the edge from the factory floor, in the cloud, or in on-premises environments—without needing to connect to the internet.
-
Get immediate intelligence
Help ensure quality control and prevent product damage by monitoring for defects in real time directly on the production line with the intelligence, security, scale, and performance of Azure.
-
Reduce manufacturing app costs
Lower the costs of intelligent manufacturing app development and moving massive industrial data volumes to the cloud. Also, alleviate network traffic by processing data right on the factory floor.
Accelerate in-store and online retail innovation
Reimagine retail by maximizing on-shelf availability and reducing shrinkage by extending Azure capabilities to the environment of your choice.
-
Create unforgettable experiences
Streamline your operations and increase your efficiency by running Azure services at the edge from the factory floor, in the cloud, or in on-premises environments—without needing to connect to the internet.
-
Maximize on-shelf availability
Alert store managers to rapidly dwindling items before they run out of stock by monitoring inventory with cameras and other in-store equipment.
-
Reduce shrinkage
Decrease inventory losses and other shrinkage with intelligence and insights into theft, ticket switching, return frauds, and voids.
Enhance patient outcomes and healthcare experiences
Accelerate healthcare innovation, overcome latency and processing speed challenges, and improve protection of on-premises health information.
-
Improve analytics and records management
Reduce latency and processing speeds and locally aggregate, process, and store records. And, bring real-time AI and analytics capabilities to specialties like pathology, imaging, research, and genomics.
-
Modernize legacy systems
Connect medical devices and apps to healthcare IT networks. Aggregate essential data within each device and help safeguard patients from equipment malfunctions by minimizing data delays.
-
Update clinical environments
Improve emergency department wait times, operating room performance, bed utilization, and patient-flow bottlenecks by transitioning legacy infrastructures and IT environments to the cloud.
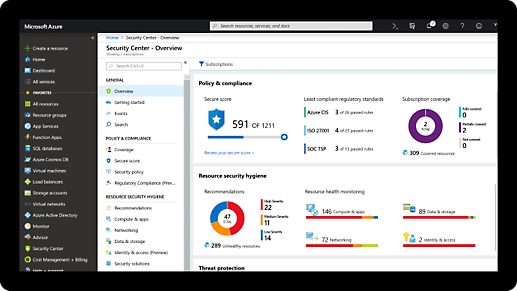
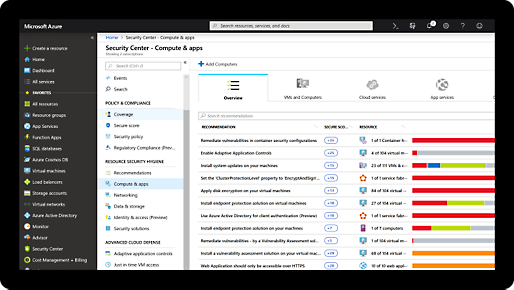
Comprehensive security and compliance, built in
-
Microsoft invests more than $1 billion annually on cybersecurity research and development.


-
We employ more than 3,500 security experts who are dedicated to data security and privacy.
-
Azure has more certifications than any other cloud provider. View the comprehensive list.
Get started with an Azure free account
1

2

After your credit, move to pay as you go to keep building with the same free services. Pay only if you use more than your free monthly amounts.
3

See how customers are using Azure Stack
"When we needed capacity, we pushed our workloads into the cloud. I didn't worry about waiting months for hardware. I knew I had capacity."
Rajeev Siddappa, VP Infrastructure, Molina Healthcare

"With Azure Stack and Azure, we have the flexibility to adapt to change, no matter where change comes from."
Dag Jørgensen, Chief Information Officer, KPMG Norway

a
"We clearly needed a hybrid solution, but we wanted to use the same tool set, administration, and training for both platforms. Only Microsoft checked all the boxes. That's why we chose Azure Stack HCI solutions."
Christopher Rivers, Director, Information Technology, Canadian Museum for Human Rights

i
"We empower decision makers with knowledge so they don't have to wrestle with technology and can just get on with saving lives, opening up roads, and addressing other urgent needs."
John Leipper, Director of Product Strategy, Haivision

1
"There was simply no other company that had the capability and the infrastructure to meet our comprehensive data, analytics, and security needs than Microsoft."
Scott Rechler, Chairman and CEO, RXR Realty

Azure Stack resources and documentation
Azure Stack portfolio webinar
Watch this webinar to learn how the Azure Stack portfolio helps you build, deploy, and run hybrid and edge computing applications consistently across location boundaries to address your diverse workloads.
Cloud Anywhere e-book
Read this e-book to learn about specific opportunities for implementing hybrid cloud infrastructure in your organization.
Azure hybrid graphic
See how Azure gives you flexibility across on-premises, multicloud, and the edge.
Azure Stack Blog
Connect with the community and hear from our engineering teams about news in the tech community.
Learn more about Azure Stack
Azure Stack Hub
Cloud-native integrated system.
Azure Stack HCI
Hyperconverged infrastructure.
Azure Stack Edge
Cloud-managed appliance.



















