Amber's Tuesday started like any other. She'd just sat down at her kitchen table with her coffee and bagel and opened her laptop to check her email.
She was a little preoccupied with an important meeting she had that afternoon – pitching Contoso's new product to the Chief Operating Officer of Tailspin Toys – so she might have been a bit distracted.
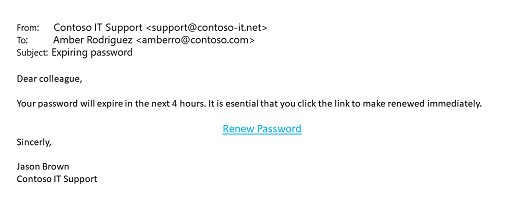
Taking another sip of coffee, she clicked the link and entered her username and password on the page that followed. When she clicked "Submit", however, an uncomfortable feeling came over her. The "confirmation" page didn't put her at ease and she looked carefully at the address bar.
http://contoso.support.contoso-it.net/confirm
That domain name didn't look right! She glanced back at the original email and her heart sank. She hadn't noticed the domain name in the email address, the misspellings in the message, or the fact that it addressed her as "colleague" instead of by name. She quickly opened Teams and searched the company directory for a "Jason Brown". As she feared…there wasn't one.
She grabbed her phone to call Contoso corporate security and report her suspicions just as the notification "ding" sounded. Glancing at her phone, it was a multifactor authentication code for her account. Somebody WAS trying to log in as her. And they had her password.
She immediately dialed the number for Contoso corporate security, and while it rang she went back to her Inbox and clicked Report > Report Phishing on the message.
"Contoso security, Avery speaking." Amber paused a second, then responded. "Hi Avery, this is Amber Rodriguez. I'm a senior account manager in Charlotte. I think I fell for a phishing message this morning."
"OK Amber, how long ago did it happen?"
"Just a couple of minutes ago. I clicked the link and before I thought better of it, I put my username and password into the site." Amber was bracing for a scolding, and maybe a call from HR.
"You did the right thing giving us a call immediately. Did you click ‘Report Phishing' on the message in Outlook?"
Amber exhaled, a bit relieved by Avery's empathetic tone. "Yes, right as I was dialing this number."
"Good. From the logs it looks like there was a successful login this morning at 7:52 your time." Avery said.
"That was me, signing in for email." Amber replied.
"OK. And we had a sign-in attempt a few minutes later at 8:01, but it was from an unknown device and the multifactor prompt was never acknowledged."
"Right! Just as I was calling you my authenticator app wanted me to confirm a sign-in. By that point I was worried that I'd been phished, so I didn't confirm it."
"Excellent," said Avery, "that's exactly what we want you to do. Never acknowledge or confirm a multifactor authentication prompt unless you're sure you're the one who initiated it. Since you're still signed in on your laptop, I need you to go to your Contoso profile page and change your password right away. Can you also forward me a copy of the phishing message you received, as an attachment?"
"Yes, of course." said Amber.
"Terrific. I'll share it with the incident response team so we can warn others in the company to be on the lookout for this attack. You did great by not confirming the multifactor authentication notice and calling us right away. I think it should be ok."
Amber hung up feeling a bit shaken, but relieved. She sipped her now-cold coffee and changed her password.
Summary
Approximately 4% of people who receive a phishing email click the link. In this story a temporary lapse of concentration, which could happen to any of us, put Amber on a dangerous path. The first website she saw looked real enough, so she entered her username and password, but fortunately she got suspicious and took swift action before any real damage was done.
What could Amber have done better?
-
Paid closer attention to the sender address (support@contoso-it.net), which was clearly "phishy".
-
When her company password had expired in the past she'd always had to change that password. An email offering to let her renew an expiring password should have seemed suspicious.
-
She should have looked at the web address of the site (http://contoso.support.contoso-it.net) that was asking for her username and password before she submitted her credentials. "HTTP" is a non-secure protocol; which wouldn't be used to legitimately sign in. The domain name itself is awkward and "contoso-it.net" rather than "contoso.com" seems suspicious.
What did Amber do right?
-
She did ultimately spot the bad web address and had the presence of mind to go back and check the email message more carefully.
-
When the multifactor authentication message came in on her phone, she knew that something was wrong and she didn't confirm it.
-
She promptly called corporate security, told them candidly what had happened, and reported the message in Outlook.
What could have been a disaster turned out ok thanks to her quick recovery.
To learn more visit https://support.microsoft.com/security.
Ready for our next story?
Check out Cameron learns about reusing passwords to find out why reusing passwords, even very strong passwords, can be a dangerous idea.
We're listening!
What did you think of this article? Did you like having cybersecurity information presented in the format of a short story like this? Would you like to see us do more of this? Please select Yes on the feedback control below if you liked it, or No if you didn't. And feel free to leave us any comments if you have feedback on how we can make it better or requests for future topics.
Your feedback will help guide us on future content like this. Thank you!