Summary
You may notice a very large number of block events collecting in the Microsoft Defender Advanced Threat Protection (MDATP) portal. These events are generated by the Code Integrity (CI) engine and can be identified by their ExploitGuardNonMicrosoftSignedBlocked ActionType.
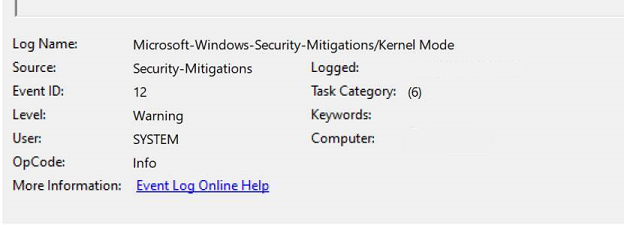
Event as seen in the endpoint event log
|
ActionType |
Provider/source |
Event ID |
Description |
|
ExploitGuardNonMicrosoftSignedBlocked |
Security-Mitigations |
12 |
Code integrity guard block |
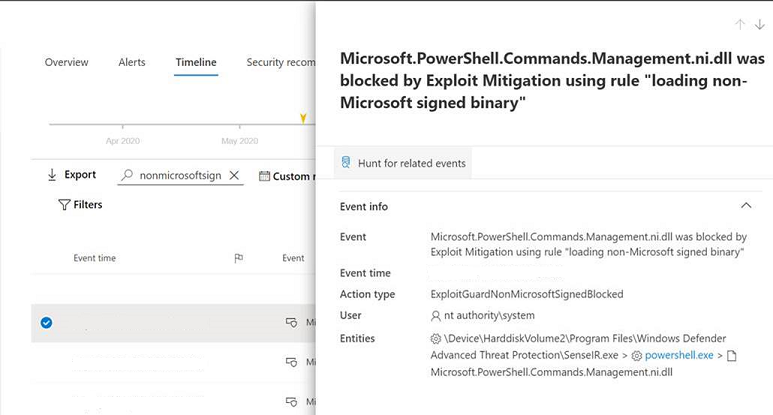
Event as seen in the timeline
Process '\Device\HarddiskVolume3\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' (PID 8780) was blocked from loading the non-Microsoft-signed binary '\Windows\assembly\NativeImages_v4.0.30319_64\Microsoft.M870d558a#\08d37b687669e97c65681029a1026d28\Microsoft.Management.Infrastructure.Native.ni.dll'
More information
The CI engine makes sure that only trusted files are permitted to execute on a device. When CI is enabled and encounters an untrusted file, it generates a block event. In Audit mode, the file is still allowed to execute, whereas in Enforce mode, the file is prevented from executing.
CI can be enabled in several ways including when you deploy a Windows Defender Application Control (WDAC) policy. However, in this situation, MDATP is enabling CI on the back end, which is triggering events when it encounters unsigned Native Image (NI) files originating from Microsoft.
The signing of a file is meant to enable verification of that files authenticity. CI can verify that a file is unmodified and originated from a trusted authority based on its signature. Most files that originate from Microsoft are signed, however some files cannot be or are not signed for various reasons. For example, NI binaries (compiled from .NET Framework code) are generally signed if they are included in a release. However, they are typically re-generated on a device and cannot be signed. Separately, many applications only have their CAB or MSI file signed to verify their authenticity at installation. When they run, they create additional files which are not signed.
Mitigation
We do not recommend that you ignore these events as they can indicate genuine security issues. For example, a malicious attacker might try to load an unsigned binary under the guise of originating from Microsoft.
However, these events can be filtered out by query when you try to analyze other events in Advanced Hunting by excluding events that have the ExploitGuardNonMicrosoftSignedBlocked ActionType.
This query would show you all of the events related to this particular over-detection:
DeviceEvents | where ActionType == "ExploitGuardNonMicrosoftSignedBlocked" and InitiatingProcessFileName == "powershell.exe" and FileName endswith "ni.dll" | where Timestamp > ago(7d)
If you want to exclude this event, then you’d have to invert the query. This would show all of the ExploitGuard (inclusive of EP) events except for these:
DeviceEvents | where ActionType startswith "ExploitGuard" | where ActionType != "ExploitGuardNonMicrosoftSignedBlocked" or (ActionType == "ExploitGuardNonMicrosoftSignedBlocked" and InitiatingProcessFileName != "powershell.exe") or (ActionType == "ExploitGuardNonMicrosoftSignedBlocked" and InitiatingProcessFileName == "powershell.exe" and FileName !endswith "ni.dll") | where Timestamp > ago(7d)
Additionally, if you use .NET Framework 4.5 or a later version, you have the option of regenerating NI files to resolve many of the superfluous events. To do this, delete all the NI files in the NativeImages directory and then run the ngen update command to regenerate them.