Summary
Microsoft is announcing the availability of an update for supported editions of Windows 7, Windows Server 2008R2, Windows 8, and Windows Server 2012. This update expands the Audit Process Creation policy to include the command information that is passed to every process. This is a new feature that provides valuable information to help administrators investigate, monitor, and troubleshoot security-related issues on their networks.
Introduction
Microsoft has released a Microsoft security advisory about this issue for IT professionals. The security advisory contains additional security-related information. To view the security advisory, go to the following Microsoft website:
More Information
This update adds a new feature to Windows that expands the Audit Process Creation policy. This new feature, when it is enabled and configured, creates an event log every time that a process is created, and it includes the command-line information that's passed to that process. These events are logged in existing event ID 4688 and in the Windows Security log. Monitoring these events can provide valuable information to help administrators troubleshoot and investigate security-related activities.
After this update is applied and configured, a new element within security event 4688 will appear with the name of Process Command Line, as shown in the following screen shot:
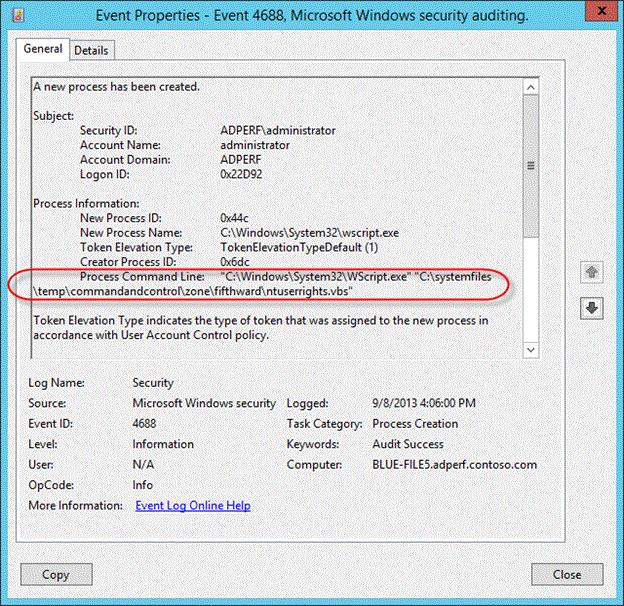
To take full advantage of this feature, administrators must follow these steps:
-
Enable the Audit Process Creation policy.
-
Enable the "Include command line in process creation events" feature.
For more information about how to configure these two features, see the Configuration section.
Background on the Audit Process Creation policy
The Audit Process Creation policy is a security audit policy that determines whether the operating system generates an audit event when a process is created. By default, this policy is not configured and no audit events are logged when processes are created. When this policy is enabled, event ID 4688 is generated and logged in the Windows Security log. Enabling this policy is required to make the expanded command-line auditing feature that's described in this security advisory work. For more information about the Audit Process Creation Policy, see the following Mimcrosoft TechNet article:
Configuration
Enabling Audit Process Creation
To enable the Audit Process Creation policy, edit the following Group Policy settings:
|
Policy configuration |
Details |
|---|---|
|
Policy location |
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Configuration\Detailed Tracking |
|
Policy name |
Audit Process Creation |
|
Default setting |
Not Configured (not enabled) |
|
Supported on |
Windows 7 and later versions |
|
Description |
This security policy setting determines whether the operating system generates audit events when a process is created (starts) and the name of the program or user who created it. |
Enabling the "Include command line in process creation events" feature
To enable the new feature that's described in this Knowledge Base article, edit the following Group Policy settings:
|
Policy configuration |
Details |
|---|---|
|
Policy location |
Administrative Templates\System\Audit Process Creation |
|
Setting |
Include command line in process creation events |
|
Default setting |
Not Configured (not enabled) |
|
Supported on |
Windows 7 and later versions |
|
Description |
This policy setting determines what information is logged in security audit events when a new process is created. |
Note When you configure and use Advanced Audit Policy Configuration settings, you must confirm that the settings are not overwritten by basic audit policy settings. Event 4719 is logged when the settings are overwritten.
The basic audit policy settings can be checked by going to Computer Configuration\Policies\Windows Settings\Security Settings\Audit Policy. You can make sure that the Advanced Audit Policy Configuration settings are not overwritten by enabling the Audit: Force audit policy subcategory settings (Windows Vista or later versions) to override audit policy category settings in the following location:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security OptionsIf you do not already have a formal plan about how to deploy and use a security audit policy in your environment, we strongly recommend that you read the Security auditing documentation on TechNet and also in the Additional resources section.
Additional resources
For more information, go to the following Microsoft websites:
Security auditing
Audit Process Creation
Advanced Security Audit Policy Step-by-Step Guide
Best Practices for securing Active Directory
Microsoft Download Center links
The following files are available for download from the Microsoft Download Center.
Security update for Windows 7 (KB3004375)
Security update for Windows 7 for x64-based Systems (KB3004375)
Security update for Windows Embedded Standard 7 (KB3004375)
Security update for Windows Embedded Standard 7 for x64-based Systems (KB3004375)
Security update for Windows Server 2008 R2 x64 Edition (KB3004375)
Security update for Windows Server 2008 R2 for Itanium-based Systems (KB3004375)
Security update for Windows 8 (KB3004375)
Security update for Windows 8 for x64-based Systems (KB3004375)
Security update for Windows Server 2012 (KB3004375)

Release Date: February 10, 2015
For more information about how to download Microsoft support files, click the following article number to view the article in the Microsoft Knowledge Base:
119591 How to obtain Microsoft support files from online servicesMicrosoft scanned this file for viruses. Microsoft used the most current virus-detection software that was available on the date that the file was posted. The file is stored on security-enhanced servers that help prevent any unauthorized changes to the file.
Known issues with this security update
-
After you apply this update, Microsoft System Center Configuration Manager clients that report to a particular server or subset of servers may repeatedly become inactive. You may also notice that the clients do not send inventory information for 30 days or more and that the data in the Inventoryagent.log file is static. Additionally, the ClientIDManagerStartup.log file displays repeated occurrences of the following error:
[RegTask] - Client is not registered. Sending registration request for GUID:4874BD6C-CB98-4EEB-9F4F-721CC65B25C3 ...
[RegTask] - Client is registered. Server assigned ClientID is GUID:4874BD6C-CB98-4EEB-9F4F-721CC65B25C3. Approval status 1
SetRegistrationState failed (0x80071770)
[RegTask] - Sleeping for 15360 seconds ...
To resolve this issue, apply one of the following security updates:3023562 MS15-010: Description of the security update for Windows kernel mode driver: February 10, 2015
3046049 MS15-031: Vulnerability in SChannel could allow security feature bypass: March 10, 2015 This will update your version of cng.sys. After you apply either of these updates and then restart the computer, the affected client will successfully send up a heartbeat and update the inventory data. This action will also enable the client to remain active. -
After you apply this update, some web server applications may fail with decryption errors that resemble the following:
Failed to decrypt using provider 'DataProtectionConfigurationProvider'. Error message from the provider: The specified file could not be decrypted. (Exception from HRESULT: 0x80071771)
To resolve this issue, install security update 3046049. For more information, click the following article number to view the article in the Microsoft Knowledge Base:3046049 MS15-031: Vulnerability in SChannel could allow security feature bypass: March 10, 2015
-
After you apply this update, Microsoft System Center Configuration Manager clients that report to a particular server or subset of servers may repeatedly become inactive. You may also notice that the clients do not send inventory information for 30 days or more and that the data in the Inventoryagent.log file is static. Additionally, the ClientIDManagerStartup.log displays repeated occurrences of the following error:
[RegTask] - Client is not registered. Sending registration request for GUID:4874BD6C-CB98-4EEB-9F4F-721CC65B25C3 ...
[RegTask] - Client is registered. Server assigned ClientID is GUID:4874BD6C-CB98-4EEB-9F4F-721CC65B25C3. Approval status 1
SetRegistrationState failed (0x80071770)
[RegTask] - Sleeping for 15360 seconds ...
To resolve this issue, apply either of the following security updates:3023562 MS15-010: Description of the security update for Windows kernel mode driver: February 10, 2015
3046049 MS15-031: Vulnerability in SChannel could allow security feature bypass: March 10, 2015
This will update your version of cng.sys. After you apply either of these updates and then restart the computer, the affected client will successfully send up a heartbeat and update the inventory data. This action will also enable the client to remain active.
File information
The English (United States) version of this software update installs files that have the attributes that are listed in the following tables. The dates and times for these files are listed in Coordinated Universal Time (UTC). The dates and times for these files on your local computer are displayed in your local time and with your current daylight saving time (DST) bias. Additionally, the dates and times may change when you perform certain operations on the files.
-
The files that apply to a specific product, milestone (RTM, SPn), and service branch (LDR, GDR) can be identified by examining the file version numbers as shown in the following table:
Version
Product
Milestone
Service branch
6.1.7601. 18xxx
Windows 7 and Windows Server 2008 R2
SP1
GDR
6.1.7601. 22xxx
Windows 7 and Windows Server 2008 R2
SP1
LDR
-
GDR service branches contain only those fixes that are widely released to address widespread, critical issues. LDR service branches contain hotfixes in addition to widely released fixes.
Note The MANIFEST files (.manifest) and MUM files (.mum) that are installed are not listed.
For all supported x86-based versions of Windows 7
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Appid-ppdlic.xrm-ms |
Not applicable |
3,013 |
14-Jan-2015 |
06:36 |
Not applicable |
|
Appid.sys |
6.1.7601.22736 |
50,688 |
07-Jul-2014 |
00:45 |
x86 |
|
Appidapi.dll |
6.1.7601.22736 |
50,688 |
07-Jul-2014 |
01:40 |
x86 |
|
Appidcertstorecheck.exe |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
02:06 |
x86 |
|
Appidpolicyconverter.exe |
6.1.7601.22653 |
97,792 |
12-Apr-2014 |
02:06 |
x86 |
|
Appidsvc.dll |
6.1.7601.22736 |
29,696 |
07-Jul-2014 |
01:40 |
x86 |
|
Setbcdlocale.dll |
6.1.7601.22780 |
50,176 |
19-Aug-2014 |
02:48 |
x86 |
|
Winload.exe |
6.1.7601.22854 |
521,384 |
29-Oct-2014 |
02:16 |
x86 |
|
Winresume.exe |
6.1.7601.22730 |
456,776 |
28-Jun-2014 |
00:22 |
x86 |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
01:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,384 |
14-Jul-2009 |
01:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
36,944 |
14-Jul-2009 |
01:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
01:11 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:33 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
01:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,880 |
14-Jul-2009 |
01:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:46 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
01:48 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
02:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,264 |
14-Jul-2009 |
03:45 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,776 |
14-Jul-2009 |
03:02 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,384 |
14-Jul-2009 |
01:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
01:52 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
01:52 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:51 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
01:53 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,384 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:45 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,872 |
14-Jul-2009 |
01:53 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:02 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
02:52 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
01:43 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:02 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
02:56 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
01:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,384 |
14-Jul-2009 |
01:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
36,944 |
14-Jul-2009 |
01:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
01:11 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:33 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
01:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,880 |
14-Jul-2009 |
01:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:46 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
01:48 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
02:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,264 |
14-Jul-2009 |
03:45 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,776 |
14-Jul-2009 |
03:02 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,384 |
14-Jul-2009 |
01:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
01:52 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
01:52 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:51 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
01:53 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,384 |
14-Jul-2009 |
01:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:45 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,872 |
14-Jul-2009 |
01:53 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:02 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
02:52 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
01:43 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:02 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
02:56 |
Not applicable |
|
Winload.exe |
6.1.7601.22854 |
521,384 |
29-Oct-2014 |
02:16 |
x86 |
|
Winresume.exe |
6.1.7601.22730 |
456,776 |
28-Jun-2014 |
00:22 |
x86 |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
02:24 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
9,728 |
07-Jul-2014 |
01:35 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
02:24 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
02:25 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
11,264 |
07-Jul-2014 |
02:24 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
6,656 |
07-Jul-2014 |
02:24 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
9,728 |
07-Jul-2014 |
02:21 |
Not applicable |
|
Ci.dll |
6.1.7601.22730 |
409,272 |
28-Jun-2014 |
00:22 |
x86 |
|
Driver.stl |
Not applicable |
4,186 |
26-Jun-2014 |
22:21 |
Not applicable |
|
Csrsrv.dll |
6.1.7601.18113 |
38,912 |
19-Mar-2013 |
04:48 |
x86 |
|
Csrsrv.dll |
6.1.7601.22653 |
38,912 |
12-Apr-2014 |
02:06 |
x86 |
|
Setbcdlocale.dll |
6.1.7601.22780 |
50,176 |
19-Aug-2014 |
02:48 |
x86 |
|
Winload.exe |
6.1.7601.22854 |
521,384 |
29-Oct-2014 |
02:16 |
x86 |
|
Winresume.exe |
6.1.7601.22908 |
456,776 |
12-Dec-2014 |
05:40 |
x86 |
|
Winload.exe.mui |
6.1.7601.17514 |
34,688 |
20-Nov-2010 |
12:50 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,176 |
20-Nov-2010 |
12:50 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,720 |
02-Apr-2010 |
04:13 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
36,736 |
20-Nov-2010 |
12:50 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,168 |
02-Apr-2010 |
04:09 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:33 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:10 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,688 |
20-Nov-2010 |
12:50 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:46 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:10 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,200 |
20-Nov-2010 |
12:58 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:08 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
02:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,072 |
02-Apr-2010 |
05:06 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
29,568 |
20-Nov-2010 |
13:45 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,176 |
20-Nov-2010 |
12:49 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
07-Apr-2010 |
09:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,712 |
20-Nov-2010 |
12:59 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:51 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,200 |
20-Nov-2010 |
13:01 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,712 |
20-Nov-2010 |
12:59 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,688 |
20-Nov-2010 |
12:58 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:50 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,176 |
20-Nov-2010 |
12:58 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:45 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
33,664 |
20-Nov-2010 |
13:01 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
13:45 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
02:52 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
12:45 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
13:46 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
02:56 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,720 |
02-Apr-2010 |
04:13 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,168 |
02-Apr-2010 |
04:09 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:33 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:10 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:53 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:10 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
02:54 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:08 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
02:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,072 |
02-Apr-2010 |
05:06 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
02:57 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
07-Apr-2010 |
09:51 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
02:47 |
Not applicable |
|
Winload.exe |
6.1.7601.22854 |
521,384 |
29-Oct-2014 |
02:16 |
x86 |
|
Winresume.exe |
6.1.7601.22908 |
456,776 |
12-Dec-2014 |
05:40 |
x86 |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
45,056 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
49,664 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
52,224 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
56,320 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
57,344 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
46,592 |
19-Sep-2014 |
09:18 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
54,272 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
50,688 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
56,832 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
43,008 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
54,272 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
55,296 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
34,304 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
33,280 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
50,176 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
54,784 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
53,248 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
52,224 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
53,760 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
52,736 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
50,688 |
19-Sep-2014 |
09:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
49,664 |
19-Sep-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
26,624 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
27,136 |
19-Sep-2014 |
09:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
45,056 |
04-Mar-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
49,664 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
52,224 |
04-Mar-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
56,832 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
57,856 |
04-Mar-2014 |
11:08 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
47,104 |
04-Mar-2014 |
10:35 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
54,784 |
04-Mar-2014 |
11:08 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
50,688 |
04-Mar-2014 |
11:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
56,832 |
04-Mar-2014 |
11:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
43,008 |
04-Mar-2014 |
11:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
54,272 |
04-Mar-2014 |
11:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
55,296 |
04-Mar-2014 |
11:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
34,304 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
33,280 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
50,176 |
04-Mar-2014 |
11:08 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
55,296 |
04-Mar-2014 |
11:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
53,248 |
04-Mar-2014 |
11:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
52,736 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
54,272 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
52,736 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
50,688 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
49,664 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
26,624 |
04-Mar-2014 |
11:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
27,136 |
04-Mar-2014 |
11:11 |
Not applicable |
|
Cng.sys |
6.1.7601.18682 |
370,480 |
29-Dec-2014 |
23:29 |
x86 |
|
Ksecdd.sys |
6.1.7601.18717 |
67,512 |
14-Jan-2015 |
05:44 |
x86 |
|
Ksecpkg.sys |
6.1.7601.18717 |
136,640 |
14-Jan-2015 |
05:44 |
x86 |
|
Lsasrv.dll |
6.1.7601.18717 |
1,061,376 |
14-Jan-2015 |
05:40 |
x86 |
|
Lsasrv.mof |
Not applicable |
13,780 |
04-Jul-2013 |
12:18 |
Not applicable |
|
Lsass.exe |
6.1.7601.18717 |
22,528 |
14-Jan-2015 |
05:40 |
x86 |
|
Secur32.dll |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
05:41 |
x86 |
|
Sspicli.dll |
6.1.7601.18717 |
100,352 |
14-Jan-2015 |
05:41 |
x86 |
|
Sspisrv.dll |
6.1.7601.18717 |
15,872 |
14-Jan-2015 |
05:41 |
x86 |
|
Cng.sys |
6.1.7601.22891 |
370,480 |
29-Dec-2014 |
23:29 |
x86 |
|
Ksecdd.sys |
6.1.7601.22653 |
67,520 |
12-Apr-2014 |
02:10 |
x86 |
|
Ksecpkg.sys |
6.1.7601.22843 |
136,632 |
14-Oct-2014 |
01:53 |
x86 |
|
Lsasrv.dll |
6.1.7601.22923 |
1,062,912 |
14-Jan-2015 |
06:21 |
x86 |
|
Lsasrv.mof |
Not applicable |
13,780 |
09-Jul-2013 |
06:22 |
Not applicable |
|
Lsass.exe |
6.1.7601.22653 |
22,528 |
12-Apr-2014 |
02:06 |
x86 |
|
Secur32.dll |
6.1.7601.22653 |
22,016 |
12-Apr-2014 |
02:06 |
x86 |
|
Sspicli.dll |
6.1.7601.22653 |
100,352 |
12-Apr-2014 |
02:06 |
x86 |
|
Sspisrv.dll |
6.1.7601.22653 |
15,872 |
12-Apr-2014 |
02:06 |
x86 |
|
Adtschema.dll.mui |
6.1.7601.18717 |
245,760 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
152,064 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
62,464 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
263,168 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
164,864 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,728 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
253,440 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,720 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
156,672 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
67,584 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
279,040 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,256 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,216 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
308,736 |
14-Jan-2015 |
06:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
187,392 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
75,776 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
248,320 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:36 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
295,936 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,256 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
185,344 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,632 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
253,952 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,768 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,632 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
311,808 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
183,296 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
216,064 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
136,192 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
62,976 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
280,064 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,744 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
171,008 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
78,336 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
281,600 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
168,448 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
72,192 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
176,640 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,528 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
110,592 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,520 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
159,232 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
101,376 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,008 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
256,512 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,208 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
153,600 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
66,560 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
268,800 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,256 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
165,888 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
72,192 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
290,816 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,744 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
180,224 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,728 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
294,400 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
181,248 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
70,144 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
288,256 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,792 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
181,248 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
283,648 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,720 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
163,328 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
76,800 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
255,488 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,208 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
161,280 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
66,560 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
256,000 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,696 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
159,744 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
61,952 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
134,656 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
19,968 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
87,040 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
139,264 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
18,944 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
89,600 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
36,864 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
246,784 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
152,064 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
62,464 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
264,704 |
11-Nov-2014 |
03:52 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
164,864 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,728 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
254,976 |
11-Nov-2014 |
03:52 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,720 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
156,672 |
14-Oct-2014 |
02:40 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
67,584 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
280,576 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,256 |
14-Oct-2014 |
02:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,216 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
310,784 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
187,392 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
75,776 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
249,856 |
11-Nov-2014 |
03:14 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:02 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
146,432 |
14-Oct-2014 |
01:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
60,416 |
12-Apr-2014 |
02:03 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
297,472 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,256 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
185,344 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
255,488 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,768 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
313,856 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
183,296 |
14-Oct-2014 |
02:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
217,600 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
136,192 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
62,976 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
282,112 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,744 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
171,008 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
78,336 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
283,136 |
11-Nov-2014 |
03:54 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
168,448 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
72,192 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
177,664 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,528 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
110,592 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,520 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
159,744 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,016 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
101,376 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,008 |
12-Apr-2014 |
02:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
258,048 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,208 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
153,600 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
66,560 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
270,336 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,256 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
165,888 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
72,192 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
292,352 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,744 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
180,224 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,728 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
296,448 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
181,248 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
70,144 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
290,304 |
14-Jan-2015 |
06:41 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,792 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
181,248 |
14-Oct-2014 |
02:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
285,184 |
14-Jan-2015 |
06:40 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,720 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
163,328 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
76,800 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
257,024 |
11-Nov-2014 |
03:52 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,208 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
161,280 |
14-Oct-2014 |
02:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
66,560 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
257,536 |
14-Jan-2015 |
06:41 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,696 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
159,744 |
14-Oct-2014 |
02:40 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
61,952 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
135,168 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
19,968 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
87,040 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
139,264 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
89,600 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
36,864 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll |
6.1.7601.18717 |
686,080 |
14-Jan-2015 |
05:36 |
x86 |
|
Auditpol.exe |
6.1.7601.18717 |
50,176 |
14-Jan-2015 |
05:40 |
x86 |
|
Msaudite.dll |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:37 |
x86 |
|
Msobjs.dll |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:38 |
x86 |
|
Adtschema.dll |
6.1.7601.22923 |
690,688 |
14-Jan-2015 |
06:14 |
x86 |
|
Auditpol.exe |
6.1.7601.22923 |
50,176 |
14-Jan-2015 |
06:20 |
x86 |
|
Msaudite.dll |
6.1.7601.22923 |
146,432 |
14-Jan-2015 |
06:15 |
x86 |
|
Msobjs.dll |
6.1.7601.22923 |
60,416 |
14-Jan-2015 |
06:15 |
x86 |
|
Ncrypt.dll |
6.1.7601.18606 |
221,184 |
19-Sep-2014 |
09:23 |
x86 |
|
Ncrypt.dll |
6.1.7601.22923 |
220,160 |
14-Jan-2015 |
06:21 |
x86 |
|
Ntkrnlpa.exe |
6.1.7601.18717 |
3,972,544 |
14-Jan-2015 |
05:44 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.18717 |
3,917,760 |
14-Jan-2015 |
05:44 |
Not applicable |
|
Ntkrnlpa.exe |
6.1.7601.22923 |
3,977,656 |
14-Jan-2015 |
06:25 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.22923 |
3,921,848 |
14-Jan-2015 |
06:25 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,103 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
05:36 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
14-Jan-2015 |
06:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,103 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
06:13 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
14-Jan-2015 |
06:34 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
14-Jan-2015 |
06:34 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
14-Jan-2015 |
06:35 |
Not applicable |
|
Credssp.dll |
6.1.7601.18606 |
17,408 |
19-Sep-2014 |
09:23 |
x86 |
|
Tspkg.dll |
6.1.7601.18606 |
65,536 |
19-Sep-2014 |
09:23 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
04-Jul-2013 |
12:24 |
Not applicable |
|
Credssp.dll |
6.1.7601.22750 |
17,408 |
16-Jul-2014 |
02:56 |
x86 |
|
Tspkg.dll |
6.1.7601.22750 |
65,536 |
16-Jul-2014 |
02:56 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
09-Jul-2013 |
06:39 |
Not applicable |
|
Wdigest.dll |
6.1.7601.18606 |
172,032 |
19-Sep-2014 |
09:23 |
x86 |
|
Wdigest.dll |
6.1.7601.22616 |
172,032 |
04-Mar-2014 |
10:39 |
x86 |
|
Kerberos.dll |
6.1.7601.18658 |
550,912 |
11-Nov-2014 |
02:44 |
x86 |
|
Kerberos.dll |
6.1.7601.22865 |
551,424 |
11-Nov-2014 |
03:21 |
x86 |
|
Msv1_0.dll |
6.1.7601.18606 |
259,584 |
19-Sep-2014 |
09:23 |
x86 |
|
Msv1_0.dll |
6.1.7601.22616 |
260,096 |
04-Mar-2014 |
10:39 |
x86 |
|
Schannel.dll |
6.1.7601.18606 |
248,832 |
19-Sep-2014 |
09:23 |
x86 |
|
Schannel.dll |
6.1.7601.22923 |
248,832 |
14-Jan-2015 |
06:21 |
x86 |
|
Auditsettings.admx |
Not applicable |
1,337 |
15-Dec-2014 |
18:26 |
Not applicable |
|
Auditsettings.admx |
Not applicable |
1,337 |
19-Oct-2014 |
22:21 |
Not applicable |
|
Apisetschema.dll |
6.1.7600.16385 |
6,656 |
14-Jul-2009 |
01:03 |
x86 |
|
Smss.exe |
6.1.7601.18113 |
69,632 |
19-Mar-2013 |
02:49 |
x86 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:03 |
x86 |
|
Smss.exe |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
02:06 |
x86 |
|
Apisetschema.dll |
6.1.7600.16385 |
12,648 |
02-Apr-2010 |
03:07 |
x86 |
|
Smss.exe |
6.1.7601.18113 |
69,632 |
19-Mar-2013 |
02:49 |
x86 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:03 |
x86 |
|
Smss.exe |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
02:06 |
x86 |
|
Rstrui.exe |
6.1.7601.21988 |
262,656 |
05-May-2012 |
07:29 |
x86 |
|
Srclient.dll |
6.1.7601.21988 |
43,008 |
05-May-2012 |
07:33 |
x86 |
|
Srcore.dll |
6.1.7601.22780 |
400,896 |
19-Aug-2014 |
02:48 |
x86 |
For all supported x64-based versions of Windows 7 and Windows Server 2008 R2
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Appid-ppdlic.xrm-ms |
Not applicable |
3,013 |
14-Jan-2015 |
06:44 |
Not applicable |
|
Appid.sys |
6.1.7601.22736 |
62,464 |
07-Jul-2014 |
01:04 |
x64 |
|
Appidapi.dll |
6.1.7601.22736 |
58,880 |
07-Jul-2014 |
02:06 |
x64 |
|
Appidcertstorecheck.exe |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
02:31 |
x64 |
|
Appidpolicyconverter.exe |
6.1.7601.22653 |
148,480 |
12-Apr-2014 |
02:31 |
x64 |
|
Appidsvc.dll |
6.1.7601.22736 |
34,304 |
07-Jul-2014 |
02:06 |
x64 |
|
Setbcdlocale.dll |
6.1.7601.22780 |
63,488 |
19-Aug-2014 |
03:05 |
x64 |
|
Winload.efi |
6.1.7601.22908 |
693,176 |
12-Dec-2014 |
06:07 |
Not applicable |
|
Winload.exe |
6.1.7601.22854 |
619,056 |
29-Oct-2014 |
02:16 |
x64 |
|
Winresume.efi |
6.1.7601.22908 |
617,384 |
12-Dec-2014 |
06:05 |
Not applicable |
|
Winresume.exe |
6.1.7601.22730 |
533,200 |
28-Jun-2014 |
00:21 |
x64 |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,368 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:43 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:43 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
36,944 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
01:31 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
01:31 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
29,264 |
14-Jul-2009 |
02:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,264 |
14-Jul-2009 |
02:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
29,776 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,776 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,368 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:32 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:32 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,880 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,368 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,856 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
02:03 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,240 |
14-Jul-2009 |
02:03 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:29 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:29 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
28,240 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,368 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:43 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:43 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
36,944 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
01:31 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
01:31 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,896 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
29,264 |
14-Jul-2009 |
02:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,264 |
14-Jul-2009 |
02:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
29,776 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,776 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,368 |
14-Jul-2009 |
02:06 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,408 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,904 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,392 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,920 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:32 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:32 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,880 |
14-Jul-2009 |
02:10 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,360 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
34,368 |
14-Jul-2009 |
02:09 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,344 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,856 |
14-Jul-2009 |
02:00 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
02:03 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,240 |
14-Jul-2009 |
02:03 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:29 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:29 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
28,240 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
28,224 |
14-Jul-2009 |
03:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi |
6.1.7601.22908 |
693,176 |
12-Dec-2014 |
06:07 |
Not applicable |
|
Winload.exe |
6.1.7601.22854 |
619,056 |
29-Oct-2014 |
02:16 |
x64 |
|
Winresume.efi |
6.1.7601.22908 |
617,384 |
12-Dec-2014 |
06:05 |
Not applicable |
|
Winresume.exe |
6.1.7601.22730 |
533,200 |
28-Jun-2014 |
00:21 |
x64 |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
03:16 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
9,728 |
07-Jul-2014 |
02:01 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
03:15 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
03:16 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
11,264 |
07-Jul-2014 |
03:15 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
6,656 |
07-Jul-2014 |
03:14 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
9,728 |
07-Jul-2014 |
03:15 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,336 |
12-Apr-2014 |
03:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,384 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
03:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
03:51 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,336 |
12-Apr-2014 |
02:28 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,408 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,384 |
12-Apr-2014 |
03:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,848 |
12-Apr-2014 |
03:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,384 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
10,240 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
9,728 |
12-Apr-2014 |
03:51 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
15,360 |
12-Apr-2014 |
03:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,408 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
18,432 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
15,872 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,848 |
12-Apr-2014 |
03:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
8,192 |
12-Apr-2014 |
03:51 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
8,192 |
12-Apr-2014 |
03:52 |
Not applicable |
|
Certcli.dll |
6.1.7601.22923 |
463,872 |
14-Jan-2015 |
06:28 |
x64 |
|
Ci.dll |
6.1.7601.22730 |
457,400 |
28-Jun-2014 |
00:21 |
x64 |
|
Driver.stl |
Not applicable |
4,186 |
26-Jun-2014 |
22:22 |
Not applicable |
|
Csrsrv.dll |
6.1.7601.18229 |
43,520 |
02-Aug-2013 |
02:12 |
x64 |
|
Csrsrv.dll |
6.1.7601.22653 |
43,520 |
12-Apr-2014 |
02:31 |
x64 |
|
Setbcdlocale.dll |
6.1.7601.22780 |
63,488 |
19-Aug-2014 |
03:05 |
x64 |
|
Winload.efi |
6.1.7601.22908 |
693,176 |
12-Dec-2014 |
06:07 |
Not applicable |
|
Winload.exe |
6.1.7601.22854 |
619,056 |
29-Oct-2014 |
02:16 |
x64 |
|
Winresume.efi |
6.1.7601.22908 |
571,320 |
12-Dec-2014 |
06:07 |
Not applicable |
|
Winresume.exe |
6.1.7601.22908 |
533,200 |
12-Dec-2014 |
06:05 |
x64 |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:38 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,688 |
20-Nov-2010 |
13:38 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:40 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,176 |
20-Nov-2010 |
13:40 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:43 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:43 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:40 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
36,736 |
20-Nov-2010 |
13:40 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,168 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,160 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,160 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:36 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,688 |
20-Nov-2010 |
13:36 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,200 |
20-Nov-2010 |
13:47 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,160 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
29,064 |
02-Apr-2010 |
05:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,064 |
02-Apr-2010 |
05:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
29,568 |
20-Nov-2010 |
14:34 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
29,568 |
20-Nov-2010 |
14:34 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
28,088 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:42 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,176 |
20-Nov-2010 |
13:42 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:31 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,160 |
07-Apr-2010 |
17:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,208 |
07-Apr-2010 |
17:47 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,712 |
20-Nov-2010 |
13:48 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:49 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,200 |
20-Nov-2010 |
13:49 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,656 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
35,712 |
20-Nov-2010 |
13:47 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:32 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:32 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,688 |
20-Nov-2010 |
13:48 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:48 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
34,176 |
20-Nov-2010 |
13:48 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:37 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
33,152 |
20-Nov-2010 |
13:49 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
33,664 |
20-Nov-2010 |
13:49 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,144 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,648 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
14:34 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
14:34 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:33 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
13:38 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
13:38 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:29 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,072 |
07-Jul-2014 |
03:29 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
14:34 |
Not applicable |
|
Winload.exe.mui |
6.1.7601.17514 |
28,032 |
20-Nov-2010 |
14:34 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,064 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,168 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
33,160 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
01:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,160 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,160 |
07-Jul-2014 |
03:36 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,728 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,680 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,160 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,216 |
02-Apr-2010 |
04:22 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,672 |
07-Jul-2014 |
03:35 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
29,064 |
02-Apr-2010 |
05:17 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
29,064 |
02-Apr-2010 |
05:17 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
27,576 |
07-Jul-2014 |
03:40 |
Not applicable |
|
Winload.efi.mui |
6.1.7600.16385 |
33,160 |
07-Apr-2010 |
17:47 |
Not applicable |
|
Winload.exe.mui |
6.1.7600.16385 |
35,208 |
07-Apr-2010 |
17:47 |
Not applicable |
|
Winresume.efi.mui |
6.1.7601.22736 |
30,136 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winresume.exe.mui |
6.1.7601.22736 |
31,168 |
07-Jul-2014 |
03:41 |
Not applicable |
|
Winload.efi |
6.1.7601.22908 |
693,176 |
12-Dec-2014 |
06:07 |
Not applicable |
|
Winload.exe |
6.1.7601.22854 |
619,056 |
29-Oct-2014 |
02:16 |
x64 |
|
Winresume.efi |
6.1.7601.22908 |
571,320 |
12-Dec-2014 |
06:07 |
Not applicable |
|
Winresume.exe |
6.1.7601.22908 |
533,200 |
12-Dec-2014 |
06:05 |
x64 |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
45,056 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
49,664 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
52,224 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
56,320 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
57,344 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
46,592 |
19-Sep-2014 |
09:39 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
54,272 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
50,688 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
56,832 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
43,008 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
54,272 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
55,296 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
34,304 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
33,280 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
50,176 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
54,784 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
53,248 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
52,224 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
53,760 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
52,736 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
50,688 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
49,664 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
26,624 |
19-Sep-2014 |
11:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
27,136 |
19-Sep-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
45,056 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
49,664 |
04-Mar-2014 |
12:14 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
52,224 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
56,832 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
57,856 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
47,104 |
04-Mar-2014 |
11:03 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
54,784 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
50,688 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
56,832 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
43,008 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
54,272 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
55,296 |
04-Mar-2014 |
12:16 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
34,304 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
33,280 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
50,176 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
55,296 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
53,248 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
52,736 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
54,272 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
52,736 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
50,688 |
04-Mar-2014 |
12:16 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
49,664 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
26,624 |
04-Mar-2014 |
12:15 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
27,136 |
04-Mar-2014 |
12:13 |
Not applicable |
|
Cng.sys |
6.1.7601.18682 |
459,336 |
30-Dec-2014 |
01:23 |
x64 |
|
Ksecdd.sys |
6.1.7601.18717 |
95,680 |
14-Jan-2015 |
06:09 |
x64 |
|
Ksecpkg.sys |
6.1.7601.18717 |
155,064 |
14-Jan-2015 |
06:09 |
x64 |
|
Lsasrv.dll |
6.1.7601.18717 |
1,461,760 |
14-Jan-2015 |
06:05 |
x64 |
|
Lsasrv.mof |
Not applicable |
13,780 |
04-Jul-2013 |
12:20 |
Not applicable |
|
Lsass.exe |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:04 |
x64 |
|
Secur32.dll |
6.1.7601.18717 |
28,160 |
14-Jan-2015 |
06:05 |
x64 |
|
Sspicli.dll |
6.1.7601.18717 |
136,192 |
14-Jan-2015 |
06:05 |
x64 |
|
Sspisrv.dll |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
06:05 |
x64 |
|
Cng.sys |
6.1.7601.22891 |
459,336 |
29-Dec-2014 |
23:30 |
x64 |
|
Ksecdd.sys |
6.1.7601.22653 |
95,680 |
12-Apr-2014 |
02:34 |
x64 |
|
Ksecpkg.sys |
6.1.7601.22843 |
155,064 |
14-Oct-2014 |
02:20 |
x64 |
|
Lsasrv.dll |
6.1.7601.22923 |
1,464,832 |
14-Jan-2015 |
06:29 |
x64 |
|
Lsasrv.mof |
Not applicable |
13,780 |
09-Jul-2013 |
06:30 |
Not applicable |
|
Lsass.exe |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:31 |
x64 |
|
Secur32.dll |
6.1.7601.22653 |
28,160 |
12-Apr-2014 |
02:32 |
x64 |
|
Sspicli.dll |
6.1.7601.22653 |
136,192 |
12-Apr-2014 |
02:32 |
x64 |
|
Sspisrv.dll |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:32 |
x64 |
|
Adtschema.dll.mui |
6.1.7601.18717 |
245,760 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
152,064 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
62,464 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
263,168 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
164,864 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,728 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
253,440 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,720 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
156,672 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
67,584 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
279,040 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,256 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,216 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
308,736 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
187,392 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
75,776 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
248,320 |
14-Jan-2015 |
06:01 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
06:01 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
06:01 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
295,936 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,256 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
185,344 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,632 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
253,952 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,768 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,632 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
311,808 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
183,296 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
216,064 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
136,192 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
62,976 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
280,064 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,744 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
171,008 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
78,336 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
281,600 |
14-Jan-2015 |
07:14 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
07:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
168,448 |
14-Jan-2015 |
07:32 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
72,192 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
176,640 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,528 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
110,592 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,520 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
159,232 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
101,376 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,008 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
256,512 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,208 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
153,600 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
66,560 |
14-Jan-2015 |
07:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
268,800 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,256 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
165,888 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
72,192 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
290,816 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,744 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
180,224 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,728 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
294,400 |
14-Jan-2015 |
07:14 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
07:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
181,248 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
70,144 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
288,256 |
14-Jan-2015 |
07:14 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,792 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
181,248 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
283,648 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,720 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
163,328 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
76,800 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
255,488 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,208 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
161,280 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
66,560 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
256,000 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,696 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
159,744 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
61,952 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
134,656 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
19,968 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
87,040 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
139,264 |
14-Jan-2015 |
07:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
18,944 |
14-Jan-2015 |
07:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
89,600 |
14-Jan-2015 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
36,864 |
14-Jan-2015 |
07:01 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
246,784 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
152,064 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
62,464 |
12-Apr-2014 |
03:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
264,704 |
11-Nov-2014 |
05:04 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
164,864 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,728 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
254,976 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,720 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
156,672 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
67,584 |
12-Apr-2014 |
03:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
280,576 |
11-Nov-2014 |
05:03 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,256 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,216 |
12-Apr-2014 |
03:28 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
310,784 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
03:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
187,392 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
75,776 |
12-Apr-2014 |
03:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
249,856 |
11-Nov-2014 |
03:36 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:28 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
146,432 |
14-Oct-2014 |
02:11 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
60,416 |
12-Apr-2014 |
02:28 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
297,472 |
14-Jan-2015 |
07:54 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,256 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
185,344 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
03:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
255,488 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,768 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
03:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
313,856 |
14-Jan-2015 |
07:55 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
183,296 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
03:28 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
217,600 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
136,192 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
62,976 |
12-Apr-2014 |
03:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
282,112 |
11-Nov-2014 |
05:03 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,744 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
171,008 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
78,336 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
283,136 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
168,448 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
72,192 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
177,664 |
11-Nov-2014 |
05:03 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,528 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
110,592 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,520 |
12-Apr-2014 |
03:28 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
159,744 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,016 |
12-Apr-2014 |
03:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
101,376 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,008 |
12-Apr-2014 |
03:28 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
258,048 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,208 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
153,600 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
66,560 |
12-Apr-2014 |
03:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
270,336 |
11-Nov-2014 |
05:03 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,256 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
165,888 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
72,192 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
292,352 |
11-Nov-2014 |
05:04 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,744 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
180,224 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,728 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
296,448 |
14-Jan-2015 |
07:54 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
181,248 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
70,144 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
290,304 |
14-Jan-2015 |
07:54 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,792 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
181,248 |
14-Oct-2014 |
03:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
285,184 |
14-Jan-2015 |
07:55 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,720 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
163,328 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
76,800 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
257,024 |
11-Nov-2014 |
05:03 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,208 |
12-Apr-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
161,280 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
66,560 |
12-Apr-2014 |
03:28 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
257,536 |
14-Jan-2015 |
07:54 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,696 |
12-Apr-2014 |
03:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
159,744 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
61,952 |
12-Apr-2014 |
03:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
135,168 |
11-Nov-2014 |
05:02 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
19,968 |
12-Apr-2014 |
03:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
87,040 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
139,264 |
11-Nov-2014 |
05:03 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
89,600 |
14-Oct-2014 |
03:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
36,864 |
12-Apr-2014 |
03:27 |
Not applicable |
|
Adtschema.dll |
6.1.7601.18717 |
686,080 |
14-Jan-2015 |
05:59 |
x64 |
|
Auditpol.exe |
6.1.7601.18717 |
64,000 |
14-Jan-2015 |
06:04 |
x64 |
|
Msaudite.dll |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
06:02 |
x64 |
|
Msobjs.dll |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
06:02 |
x64 |
|
Adtschema.dll |
6.1.7601.22923 |
690,688 |
14-Jan-2015 |
06:21 |
x64 |
|
Auditpol.exe |
6.1.7601.22923 |
64,000 |
14-Jan-2015 |
06:28 |
x64 |
|
Msaudite.dll |
6.1.7601.22923 |
146,432 |
14-Jan-2015 |
06:23 |
x64 |
|
Msobjs.dll |
6.1.7601.22923 |
60,416 |
14-Jan-2015 |
06:23 |
x64 |
|
Ncrypt.dll |
6.1.7601.18606 |
309,760 |
19-Sep-2014 |
09:42 |
x64 |
|
Ncrypt.dll |
6.1.7601.22923 |
308,224 |
14-Jan-2015 |
06:29 |
x64 |
|
Ocspisapi.dll |
6.1.7601.22653 |
355,840 |
12-Apr-2014 |
02:32 |
x64 |
|
Ocspisapictrs.h |
Not applicable |
1,421 |
09-Jul-2013 |
06:42 |
Not applicable |
|
Ocspisapictrs.ini |
Not applicable |
2,636 |
09-Jul-2013 |
06:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
10,240 |
12-Apr-2014 |
04:03 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,960 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
10,752 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,134 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
9,728 |
12-Apr-2014 |
02:29 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,918 |
12-Apr-2014 |
02:29 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
11,264 |
12-Apr-2014 |
04:01 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,210 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
11,776 |
12-Apr-2014 |
04:03 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,098 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
11,264 |
12-Apr-2014 |
04:01 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,028 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
10,752 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,140 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,642 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
6,144 |
12-Apr-2014 |
04:01 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,576 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
10,752 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,026 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
12,288 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,028 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
10,752 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,188 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
11,264 |
12-Apr-2014 |
04:01 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,130 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
10,240 |
12-Apr-2014 |
04:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,064 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
9,728 |
12-Apr-2014 |
04:03 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,092 |
12-Apr-2014 |
03:42 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
9,728 |
12-Apr-2014 |
04:00 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,828 |
12-Apr-2014 |
03:40 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
5,120 |
12-Apr-2014 |
04:00 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,158 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe.mui |
6.1.7601.22653 |
5,120 |
12-Apr-2014 |
04:01 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,460 |
12-Apr-2014 |
03:41 |
Not applicable |
|
Ocspsvc.exe |
6.1.7601.22653 |
276,480 |
12-Apr-2014 |
02:31 |
x64 |
|
Ocspsvcctrs.h |
Not applicable |
1,569 |
09-Jul-2013 |
06:42 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,918 |
09-Jul-2013 |
06:42 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.18717 |
5,554,112 |
14-Jan-2015 |
06:09 |
x64 |
|
Ntoskrnl.exe |
6.1.7601.22923 |
5,553,080 |
14-Jan-2015 |
06:34 |
x64 |
|
Auditsettings.adml |
Not applicable |
2,103 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
06:01 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
07:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
14-Jan-2015 |
07:07 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,103 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
14-Jan-2015 |
07:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
14-Jan-2015 |
07:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
06:21 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
14-Jan-2015 |
07:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
14-Jan-2015 |
07:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
14-Jan-2015 |
07:48 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
07:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
14-Jan-2015 |
07:47 |
Not applicable |
|
Credssp.dll |
6.1.7601.18606 |
22,016 |
19-Sep-2014 |
09:42 |
x64 |
|
Tspkg.dll |
6.1.7601.18606 |
86,528 |
19-Sep-2014 |
09:42 |
x64 |
|
Tspkg.mof |
Not applicable |
964 |
04-Jul-2013 |
12:25 |
Not applicable |
|
Credssp.dll |
6.1.7601.22750 |
22,016 |
16-Jul-2014 |
03:23 |
x64 |
|
Tspkg.dll |
6.1.7601.22750 |
86,528 |
16-Jul-2014 |
03:23 |
x64 |
|
Tspkg.mof |
Not applicable |
964 |
09-Jul-2013 |
06:41 |
Not applicable |
|
Wdigest.dll |
6.1.7601.18606 |
210,944 |
19-Sep-2014 |
09:42 |
x64 |
|
Wdigest.dll |
6.1.7601.22616 |
210,944 |
04-Mar-2014 |
11:08 |
x64 |
|
Kerberos.dll |
6.1.7601.18658 |
728,064 |
11-Nov-2014 |
03:08 |
x64 |
|
Kerberos.dll |
6.1.7601.22865 |
729,600 |
11-Nov-2014 |
03:45 |
x64 |
|
Msv1_0.dll |
6.1.7601.18606 |
314,880 |
19-Sep-2014 |
09:42 |
x64 |
|
Msv1_0.dll |
6.1.7601.22616 |
315,904 |
04-Mar-2014 |
11:08 |
x64 |
|
Schannel.dll |
6.1.7601.18606 |
342,016 |
19-Sep-2014 |
09:42 |
x64 |
|
Schannel.dll |
6.1.7601.22923 |
341,504 |
14-Jan-2015 |
06:29 |
x64 |
|
Auditsettings.admx |
Not applicable |
1,337 |
15-Dec-2014 |
18:26 |
Not applicable |
|
Auditsettings.admx |
Not applicable |
1,337 |
19-Oct-2014 |
22:22 |
Not applicable |
|
Apisetschema.dll |
6.1.7601.18229 |
6,656 |
02-Aug-2013 |
02:12 |
x64 |
|
Smss.exe |
6.1.7601.18229 |
112,640 |
02-Aug-2013 |
00:59 |
x64 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:28 |
x64 |
|
Smss.exe |
6.1.7601.22653 |
112,640 |
12-Apr-2014 |
02:31 |
x64 |
|
Apisetschema.dll |
6.1.7601.18229 |
6,656 |
02-Aug-2013 |
02:12 |
x64 |
|
Smss.exe |
6.1.7601.18229 |
112,640 |
02-Aug-2013 |
00:59 |
x64 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:28 |
x64 |
|
Smss.exe |
6.1.7601.22653 |
112,640 |
12-Apr-2014 |
02:31 |
x64 |
|
Rstrui.exe |
6.1.7601.18717 |
296,960 |
14-Jan-2015 |
06:04 |
x64 |
|
Srclient.dll |
6.1.7601.18717 |
50,176 |
14-Jan-2015 |
06:05 |
x64 |
|
Srcore.dll |
6.1.7601.18717 |
503,808 |
14-Jan-2015 |
06:05 |
x64 |
|
Rstrui.exe |
6.1.7601.21988 |
296,960 |
05-May-2012 |
08:17 |
x64 |
|
Srclient.dll |
6.1.7601.21988 |
50,176 |
05-May-2012 |
08:18 |
x64 |
|
Srcore.dll |
6.1.7601.22780 |
503,808 |
19-Aug-2014 |
03:05 |
x64 |
|
Appidapi.dll |
6.1.7601.22736 |
50,688 |
07-Jul-2014 |
01:40 |
x86 |
|
Lsasrv.mof |
Not applicable |
13,780 |
04-Jul-2013 |
12:18 |
Not applicable |
|
Secur32.dll |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
05:41 |
x86 |
|
Sspicli.dll |
6.1.7601.18717 |
96,768 |
14-Jan-2015 |
05:40 |
x86 |
|
Lsasrv.mof |
Not applicable |
13,780 |
09-Jul-2013 |
06:22 |
Not applicable |
|
Secur32.dll |
6.1.7601.22923 |
22,016 |
14-Jan-2015 |
06:21 |
x86 |
|
Sspicli.dll |
6.1.7601.22923 |
96,768 |
14-Jan-2015 |
06:18 |
x86 |
|
Wdigest.dll |
6.1.7601.18606 |
172,032 |
19-Sep-2014 |
09:23 |
x86 |
|
Wdigest.dll |
6.1.7601.22616 |
172,032 |
04-Mar-2014 |
10:39 |
x86 |
|
Kerberos.dll |
6.1.7601.18658 |
550,912 |
11-Nov-2014 |
02:44 |
x86 |
|
Kerberos.dll |
6.1.7601.22865 |
551,424 |
11-Nov-2014 |
03:21 |
x86 |
|
Msv1_0.dll |
6.1.7601.18606 |
259,584 |
19-Sep-2014 |
09:23 |
x86 |
|
Msv1_0.dll |
6.1.7601.22616 |
260,096 |
04-Mar-2014 |
10:39 |
x86 |
|
Schannel.dll |
6.1.7601.18606 |
248,832 |
19-Sep-2014 |
09:23 |
x86 |
|
Schannel.dll |
6.1.7601.22923 |
248,832 |
14-Jan-2015 |
06:21 |
x86 |
|
Apisetschema.dll |
6.1.7601.18229 |
6,656 |
02-Aug-2013 |
01:48 |
x86 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:03 |
x86 |
|
Apisetschema.dll |
6.1.7601.18229 |
6,656 |
02-Aug-2013 |
01:48 |
x86 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:03 |
x86 |
|
Srclient.dll |
6.1.7601.18717 |
43,008 |
14-Jan-2015 |
05:41 |
x86 |
|
Srclient.dll |
6.1.7601.21988 |
43,008 |
05-May-2012 |
07:33 |
x86 |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,336 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,384 |
12-Apr-2014 |
02:51 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
02:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,336 |
12-Apr-2014 |
02:03 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,408 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,384 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,848 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,384 |
12-Apr-2014 |
02:52 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
10,240 |
12-Apr-2014 |
02:51 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
9,728 |
12-Apr-2014 |
02:51 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
15,360 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,408 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
17,920 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
18,432 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
15,872 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
16,896 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
14,848 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
8,192 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll.mui |
6.1.7601.22653 |
8,192 |
12-Apr-2014 |
02:50 |
Not applicable |
|
Certcli.dll |
6.1.7601.22923 |
342,528 |
14-Jan-2015 |
06:21 |
x86 |
|
Adtschema.dll.mui |
6.1.7601.18717 |
245,760 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
152,064 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
62,464 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
263,168 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
164,864 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,728 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
253,440 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,720 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
156,672 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
67,584 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
279,040 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,256 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,216 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
308,736 |
14-Jan-2015 |
06:13 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
187,392 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
75,776 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
248,320 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:36 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
295,936 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,256 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
185,344 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,632 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
253,952 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,768 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,632 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
311,808 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
183,296 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
216,064 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
136,192 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
62,976 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
280,064 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,744 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
171,008 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
78,336 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
281,600 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
168,448 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
72,192 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
176,640 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,528 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
110,592 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,520 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
159,232 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
101,376 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,008 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
256,512 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,208 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
153,600 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
66,560 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
268,800 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,256 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
165,888 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
72,192 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
290,816 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,744 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
180,224 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,728 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
294,400 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
31,232 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
181,248 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
70,144 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
288,256 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,792 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
181,248 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
283,648 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,720 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
163,328 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
76,800 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
255,488 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
30,208 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
161,280 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
66,560 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
256,000 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,696 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
159,744 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
61,952 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
134,656 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
19,968 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
87,040 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
139,264 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
18,944 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
89,600 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
36,864 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
246,784 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
152,064 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
62,464 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
264,704 |
11-Nov-2014 |
03:52 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
164,864 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,728 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
254,976 |
11-Nov-2014 |
03:52 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,720 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
156,672 |
14-Oct-2014 |
02:40 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
67,584 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
280,576 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,256 |
14-Oct-2014 |
02:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,216 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
310,784 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
187,392 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
75,776 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
249,856 |
11-Nov-2014 |
03:14 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:02 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
146,432 |
14-Oct-2014 |
01:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
60,416 |
12-Apr-2014 |
02:03 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
297,472 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,256 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
185,344 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
255,488 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,768 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,632 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
313,856 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
183,296 |
14-Oct-2014 |
02:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
217,600 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
136,192 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
62,976 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
282,112 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,744 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
171,008 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
78,336 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
283,136 |
11-Nov-2014 |
03:54 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
168,448 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
72,192 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
177,664 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,528 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
110,592 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,520 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
159,744 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,016 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
101,376 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,008 |
12-Apr-2014 |
02:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
258,048 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,208 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
153,600 |
14-Oct-2014 |
02:38 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
66,560 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
270,336 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,256 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
165,888 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
72,192 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
292,352 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,744 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
180,224 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,728 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
296,448 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
31,232 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
181,248 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
70,144 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
290,304 |
14-Jan-2015 |
06:41 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,792 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
181,248 |
14-Oct-2014 |
02:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
285,184 |
14-Jan-2015 |
06:40 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,720 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
163,328 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
76,800 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
257,024 |
11-Nov-2014 |
03:52 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
30,208 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
161,280 |
14-Oct-2014 |
02:41 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
66,560 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
257,536 |
14-Jan-2015 |
06:41 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,696 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
159,744 |
14-Oct-2014 |
02:40 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
61,952 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
135,168 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
19,968 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
87,040 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
139,264 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
89,600 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
36,864 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll |
6.1.7601.18717 |
686,080 |
14-Jan-2015 |
05:36 |
x86 |
|
Auditpol.exe |
6.1.7601.18717 |
50,176 |
14-Jan-2015 |
05:40 |
x86 |
|
Msaudite.dll |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:37 |
x86 |
|
Msobjs.dll |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:38 |
x86 |
|
Adtschema.dll |
6.1.7601.22923 |
690,688 |
14-Jan-2015 |
06:14 |
x86 |
|
Auditpol.exe |
6.1.7601.22923 |
50,176 |
14-Jan-2015 |
06:20 |
x86 |
|
Msaudite.dll |
6.1.7601.22923 |
146,432 |
14-Jan-2015 |
06:15 |
x86 |
|
Msobjs.dll |
6.1.7601.22923 |
60,416 |
14-Jan-2015 |
06:15 |
x86 |
|
Ncrypt.dll |
6.1.7601.18606 |
221,184 |
19-Sep-2014 |
09:23 |
x86 |
|
Ncrypt.dll |
6.1.7601.22923 |
220,160 |
14-Jan-2015 |
06:21 |
x86 |
|
Ntkrnlpa.exe |
6.1.7601.18717 |
3,972,544 |
14-Jan-2015 |
05:44 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.18717 |
3,917,760 |
14-Jan-2015 |
05:44 |
Not applicable |
|
Ntkrnlpa.exe |
6.1.7601.22923 |
3,977,656 |
14-Jan-2015 |
06:25 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.22923 |
3,921,848 |
14-Jan-2015 |
06:25 |
Not applicable |
|
Credssp.dll |
6.1.7601.18606 |
17,408 |
19-Sep-2014 |
09:23 |
x86 |
|
Tspkg.dll |
6.1.7601.18606 |
65,536 |
19-Sep-2014 |
09:23 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
04-Jul-2013 |
12:24 |
Not applicable |
|
Credssp.dll |
6.1.7601.22750 |
17,408 |
16-Jul-2014 |
02:56 |
x86 |
|
Tspkg.dll |
6.1.7601.22750 |
65,536 |
16-Jul-2014 |
02:56 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
09-Jul-2013 |
06:39 |
Not applicable |
For all supported IA-64-based versions of Windows Server 2008 R2
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Appid-ppdlic.xrm-ms |
Not applicable |
3,013 |
14-Jan-2015 |
05:36 |
Not applicable |
|
Appid.sys |
6.1.7601.22736 |
131,584 |
07-Jul-2014 |
00:41 |
IA-64 |
|
Appidapi.dll |
6.1.7601.22736 |
116,736 |
07-Jul-2014 |
01:25 |
IA-64 |
|
Appidcertstorecheck.exe |
6.1.7601.22923 |
39,424 |
14-Jan-2015 |
05:21 |
IA-64 |
|
Appidpolicyconverter.exe |
6.1.7601.22653 |
282,624 |
12-Apr-2014 |
01:35 |
IA-64 |
|
Appidsvc.dll |
6.1.7601.22923 |
74,240 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Setbcdlocale.dll |
6.1.7601.22780 |
154,112 |
19-Aug-2014 |
02:13 |
IA-64 |
|
Winload.efi |
6.1.7601.22908 |
1,840,576 |
12-Dec-2014 |
04:48 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
35,776 |
19-Aug-2014 |
04:00 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
33,208 |
19-Aug-2014 |
02:12 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
35,768 |
19-Aug-2014 |
04:00 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
29,112 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
29,624 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
28,088 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
28,088 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
35,776 |
19-Aug-2014 |
04:00 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
33,208 |
19-Aug-2014 |
02:12 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
35,768 |
19-Aug-2014 |
04:00 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
29,112 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
29,624 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
28,088 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi.mui |
6.1.7601.22780 |
28,088 |
19-Aug-2014 |
03:59 |
Not applicable |
|
Winload.efi |
6.1.7601.22908 |
1,840,576 |
12-Dec-2014 |
04:48 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
02:35 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
9,728 |
07-Jul-2014 |
01:20 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
10,752 |
07-Jul-2014 |
02:40 |
Not applicable |
|
Ci.dll.mui |
6.1.7601.22736 |
6,656 |
07-Jul-2014 |
02:37 |
Not applicable |
|
Ci.dll |
6.1.7601.22730 |
218,856 |
28-Jun-2014 |
00:19 |
IA-64 |
|
Driver.stl |
Not applicable |
4,186 |
26-Jun-2014 |
22:20 |
Not applicable |
|
Csrsrv.dll |
6.1.7601.18229 |
94,720 |
02-Aug-2013 |
01:25 |
IA-64 |
|
Csrsrv.dll |
6.1.7601.22653 |
94,720 |
12-Apr-2014 |
01:36 |
IA-64 |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
56,320 |
19-Sep-2014 |
10:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
46,592 |
19-Sep-2014 |
08:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
56,832 |
19-Sep-2014 |
10:44 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
34,304 |
19-Sep-2014 |
10:46 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
33,280 |
19-Sep-2014 |
10:41 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
26,624 |
19-Sep-2014 |
10:42 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.18606 |
27,136 |
19-Sep-2014 |
10:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
56,832 |
04-Mar-2014 |
11:49 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
47,104 |
04-Mar-2014 |
10:16 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
56,832 |
04-Mar-2014 |
11:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
34,304 |
04-Mar-2014 |
11:48 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
33,280 |
04-Mar-2014 |
11:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
26,624 |
04-Mar-2014 |
11:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.1.7601.22616 |
27,136 |
04-Mar-2014 |
11:48 |
Not applicable |
|
Cng.sys |
6.1.7601.18682 |
790,168 |
29-Dec-2014 |
23:25 |
IA-64 |
|
Ksecdd.sys |
6.1.7601.18717 |
179,640 |
14-Jan-2015 |
05:25 |
IA-64 |
|
Ksecpkg.sys |
6.1.7601.18717 |
316,864 |
14-Jan-2015 |
05:25 |
IA-64 |
|
Lsasrv.dll |
6.1.7601.18717 |
2,696,704 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Lsasrv.mof |
Not applicable |
13,780 |
04-Jul-2013 |
12:25 |
Not applicable |
|
Lsass.exe |
6.1.7601.18717 |
56,320 |
14-Jan-2015 |
05:21 |
IA-64 |
|
Secur32.dll |
6.1.7601.18717 |
48,640 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Sspicli.dll |
6.1.7601.18717 |
275,456 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Sspisrv.dll |
6.1.7601.18717 |
46,080 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Cng.sys |
6.1.7601.22891 |
790,168 |
29-Dec-2014 |
23:27 |
IA-64 |
|
Ksecdd.sys |
6.1.7601.22653 |
179,648 |
12-Apr-2014 |
01:38 |
IA-64 |
|
Ksecpkg.sys |
6.1.7601.22843 |
316,864 |
14-Oct-2014 |
01:30 |
IA-64 |
|
Lsasrv.dll |
6.1.7601.22923 |
2,700,800 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Lsasrv.mof |
Not applicable |
13,780 |
09-Jul-2013 |
06:28 |
Not applicable |
|
Lsass.exe |
6.1.7601.22653 |
56,320 |
12-Apr-2014 |
01:36 |
IA-64 |
|
Secur32.dll |
6.1.7601.22653 |
48,640 |
12-Apr-2014 |
01:36 |
IA-64 |
|
Sspicli.dll |
6.1.7601.22653 |
275,456 |
12-Apr-2014 |
01:36 |
IA-64 |
|
Sspisrv.dll |
6.1.7601.22653 |
46,080 |
12-Apr-2014 |
01:36 |
IA-64 |
|
Adtschema.dll.mui |
6.1.7601.18717 |
279,040 |
14-Jan-2015 |
06:48 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:46 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,256 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,216 |
14-Jan-2015 |
06:50 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
248,320 |
14-Jan-2015 |
05:17 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
05:18 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:17 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:18 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
311,808 |
14-Jan-2015 |
06:49 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
183,296 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
06:48 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
176,640 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,528 |
14-Jan-2015 |
06:46 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
110,592 |
14-Jan-2015 |
06:50 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,520 |
14-Jan-2015 |
06:49 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
159,232 |
14-Jan-2015 |
06:45 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
06:50 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
101,376 |
14-Jan-2015 |
06:49 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,008 |
14-Jan-2015 |
06:46 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
134,656 |
14-Jan-2015 |
06:46 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
19,968 |
14-Jan-2015 |
06:48 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
87,040 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
139,264 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
18,944 |
14-Jan-2015 |
06:50 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
89,600 |
14-Jan-2015 |
06:51 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
36,864 |
14-Jan-2015 |
06:45 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
280,576 |
11-Nov-2014 |
04:37 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
03:22 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,256 |
14-Oct-2014 |
02:56 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,216 |
12-Apr-2014 |
03:23 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
249,856 |
11-Nov-2014 |
02:18 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
01:32 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
146,432 |
14-Oct-2014 |
01:22 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
60,416 |
12-Apr-2014 |
01:33 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
313,856 |
14-Jan-2015 |
07:36 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
03:22 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
183,296 |
14-Oct-2014 |
02:55 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
03:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
177,664 |
11-Nov-2014 |
04:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,528 |
12-Apr-2014 |
03:22 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
110,592 |
14-Oct-2014 |
03:00 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,520 |
12-Apr-2014 |
03:21 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
159,744 |
11-Nov-2014 |
04:41 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,016 |
12-Apr-2014 |
03:25 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
101,376 |
14-Oct-2014 |
02:58 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,008 |
12-Apr-2014 |
03:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
135,168 |
11-Nov-2014 |
04:38 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
19,968 |
12-Apr-2014 |
03:26 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
87,040 |
14-Oct-2014 |
02:58 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
03:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
139,264 |
11-Nov-2014 |
04:39 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
03:22 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
89,600 |
14-Oct-2014 |
02:55 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
36,864 |
12-Apr-2014 |
03:22 |
Not applicable |
|
Adtschema.dll |
6.1.7601.18717 |
686,080 |
14-Jan-2015 |
05:17 |
IA-64 |
|
Auditpol.exe |
6.1.7601.18717 |
145,408 |
14-Jan-2015 |
05:21 |
IA-64 |
|
Msaudite.dll |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:19 |
IA-64 |
|
Msobjs.dll |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:19 |
IA-64 |
|
Adtschema.dll |
6.1.7601.22923 |
690,688 |
14-Jan-2015 |
05:17 |
IA-64 |
|
Auditpol.exe |
6.1.7601.22923 |
145,408 |
14-Jan-2015 |
05:21 |
IA-64 |
|
Msaudite.dll |
6.1.7601.22923 |
146,432 |
14-Jan-2015 |
05:19 |
IA-64 |
|
Msobjs.dll |
6.1.7601.22923 |
60,416 |
14-Jan-2015 |
05:19 |
IA-64 |
|
Ncrypt.dll |
6.1.7601.18606 |
552,448 |
19-Sep-2014 |
09:03 |
IA-64 |
|
Ncrypt.dll |
6.1.7601.22923 |
553,472 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Ntoskrnl.exe |
6.1.7601.18717 |
11,121,592 |
14-Jan-2015 |
05:26 |
IA-64 |
|
Ntoskrnl.exe |
6.1.7601.22923 |
11,125,176 |
14-Jan-2015 |
05:26 |
IA-64 |
|
Auditsettings.adml |
Not applicable |
2,123 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
05:17 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
14-Jan-2015 |
06:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
14-Jan-2015 |
06:49 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
14-Jan-2015 |
06:50 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
14-Jan-2015 |
06:50 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
14-Jan-2015 |
06:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
14-Jan-2015 |
07:39 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
14-Jan-2015 |
05:17 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
14-Jan-2015 |
07:37 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
14-Jan-2015 |
07:36 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
14-Jan-2015 |
07:38 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
14-Jan-2015 |
07:39 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
14-Jan-2015 |
07:41 |
Not applicable |
|
Credssp.dll |
6.1.7601.18606 |
49,664 |
19-Sep-2014 |
09:03 |
IA-64 |
|
Tspkg.dll |
6.1.7601.18606 |
188,416 |
19-Sep-2014 |
09:03 |
IA-64 |
|
Tspkg.mof |
Not applicable |
964 |
04-Jul-2013 |
12:32 |
Not applicable |
|
Credssp.dll |
6.1.7601.22750 |
49,664 |
16-Jul-2014 |
02:34 |
IA-64 |
|
Tspkg.dll |
6.1.7601.22750 |
188,416 |
16-Jul-2014 |
02:34 |
IA-64 |
|
Tspkg.mof |
Not applicable |
964 |
09-Jul-2013 |
06:41 |
Not applicable |
|
Wdigest.dll |
6.1.7601.18606 |
475,136 |
19-Sep-2014 |
09:03 |
IA-64 |
|
Wdigest.dll |
6.1.7601.22616 |
475,136 |
04-Mar-2014 |
10:20 |
IA-64 |
|
Kerberos.dll |
6.1.7601.18658 |
1,525,760 |
11-Nov-2014 |
02:23 |
IA-64 |
|
Kerberos.dll |
6.1.7601.22865 |
1,527,296 |
11-Nov-2014 |
02:24 |
IA-64 |
|
Msv1_0.dll |
6.1.7601.18606 |
647,680 |
19-Sep-2014 |
09:03 |
IA-64 |
|
Msv1_0.dll |
6.1.7601.22616 |
650,240 |
04-Mar-2014 |
10:20 |
IA-64 |
|
Schannel.dll |
6.1.7601.18606 |
714,240 |
19-Sep-2014 |
09:03 |
IA-64 |
|
Schannel.dll |
6.1.7601.22923 |
714,240 |
14-Jan-2015 |
05:22 |
IA-64 |
|
Auditsettings.admx |
Not applicable |
1,337 |
15-Dec-2014 |
18:24 |
Not applicable |
|
Auditsettings.admx |
Not applicable |
1,337 |
19-Oct-2014 |
22:19 |
Not applicable |
|
Apisetschema.dll |
6.1.7601.18229 |
6,656 |
02-Aug-2013 |
01:25 |
IA-64 |
|
Smss.exe |
6.1.7601.18229 |
207,872 |
02-Aug-2013 |
00:34 |
IA-64 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
01:32 |
IA-64 |
|
Smss.exe |
6.1.7601.22653 |
207,872 |
12-Apr-2014 |
01:36 |
IA-64 |
|
Appidapi.dll |
6.1.7601.22736 |
50,688 |
07-Jul-2014 |
01:40 |
x86 |
|
Lsasrv.mof |
Not applicable |
13,780 |
04-Jul-2013 |
12:18 |
Not applicable |
|
Secur32.dll |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
05:41 |
x86 |
|
Sspicli.dll |
6.1.7601.18717 |
96,768 |
14-Jan-2015 |
05:40 |
x86 |
|
Lsasrv.mof |
Not applicable |
13,780 |
09-Jul-2013 |
06:22 |
Not applicable |
|
Secur32.dll |
6.1.7601.22923 |
22,016 |
14-Jan-2015 |
06:21 |
x86 |
|
Sspicli.dll |
6.1.7601.22923 |
96,768 |
14-Jan-2015 |
06:18 |
x86 |
|
Wdigest.dll |
6.1.7601.18606 |
172,032 |
19-Sep-2014 |
09:23 |
x86 |
|
Wdigest.dll |
6.1.7601.22616 |
172,032 |
04-Mar-2014 |
10:39 |
x86 |
|
Kerberos.dll |
6.1.7601.18658 |
550,912 |
11-Nov-2014 |
02:44 |
x86 |
|
Kerberos.dll |
6.1.7601.22865 |
551,424 |
11-Nov-2014 |
03:21 |
x86 |
|
Msv1_0.dll |
6.1.7601.18606 |
259,584 |
19-Sep-2014 |
09:23 |
x86 |
|
Msv1_0.dll |
6.1.7601.22616 |
260,096 |
04-Mar-2014 |
10:39 |
x86 |
|
Schannel.dll |
6.1.7601.18606 |
248,832 |
19-Sep-2014 |
09:23 |
x86 |
|
Schannel.dll |
6.1.7601.22923 |
248,832 |
14-Jan-2015 |
06:21 |
x86 |
|
Apisetschema.dll |
6.1.7601.18229 |
6,656 |
02-Aug-2013 |
01:48 |
x86 |
|
Apisetschema.dll |
6.1.7601.22653 |
6,656 |
12-Apr-2014 |
02:03 |
x86 |
|
Adtschema.dll.mui |
6.1.7601.18717 |
279,040 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
160,256 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
73,216 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
248,320 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
29,184 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:36 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:35 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
311,808 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
32,768 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
183,296 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
69,120 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
176,640 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,528 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
110,592 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,520 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
159,232 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
22,016 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
101,376 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
43,008 |
14-Jan-2015 |
06:00 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
134,656 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
19,968 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
87,040 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
33,280 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.18717 |
139,264 |
14-Jan-2015 |
06:12 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.18717 |
18,944 |
14-Jan-2015 |
06:29 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.18717 |
89,600 |
14-Jan-2015 |
06:33 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.18717 |
36,864 |
14-Jan-2015 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
280,576 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:55 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
160,256 |
14-Oct-2014 |
02:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
73,216 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
249,856 |
11-Nov-2014 |
03:14 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
29,184 |
12-Apr-2014 |
02:02 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
146,432 |
14-Oct-2014 |
01:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
60,416 |
12-Apr-2014 |
02:03 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22923 |
313,856 |
14-Jan-2015 |
06:42 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
32,768 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
183,296 |
14-Oct-2014 |
02:44 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
69,120 |
12-Apr-2014 |
02:25 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
177,664 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,528 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
110,592 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,520 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
159,744 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
22,016 |
12-Apr-2014 |
02:54 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
101,376 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
43,008 |
12-Apr-2014 |
02:27 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
135,168 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
19,968 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
87,040 |
14-Oct-2014 |
02:43 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
33,280 |
12-Apr-2014 |
02:26 |
Not applicable |
|
Adtschema.dll.mui |
6.1.7601.22865 |
139,264 |
11-Nov-2014 |
03:53 |
Not applicable |
|
Auditpol.exe.mui |
6.1.7601.22653 |
18,944 |
12-Apr-2014 |
02:53 |
Not applicable |
|
Msaudite.dll.mui |
6.1.7601.22843 |
89,600 |
14-Oct-2014 |
02:42 |
Not applicable |
|
Msobjs.dll.mui |
6.1.7601.22653 |
36,864 |
12-Apr-2014 |
02:24 |
Not applicable |
|
Adtschema.dll |
6.1.7601.18717 |
686,080 |
14-Jan-2015 |
05:36 |
x86 |
|
Auditpol.exe |
6.1.7601.18717 |
50,176 |
14-Jan-2015 |
05:40 |
x86 |
|
Msaudite.dll |
6.1.7601.18717 |
146,432 |
14-Jan-2015 |
05:37 |
x86 |
|
Msobjs.dll |
6.1.7601.18717 |
60,416 |
14-Jan-2015 |
05:38 |
x86 |
|
Adtschema.dll |
6.1.7601.22923 |
690,688 |
14-Jan-2015 |
06:14 |
x86 |
|
Auditpol.exe |
6.1.7601.22923 |
50,176 |
14-Jan-2015 |
06:20 |
x86 |
|
Msaudite.dll |
6.1.7601.22923 |
146,432 |
14-Jan-2015 |
06:15 |
x86 |
|
Msobjs.dll |
6.1.7601.22923 |
60,416 |
14-Jan-2015 |
06:15 |
x86 |
|
Ncrypt.dll |
6.1.7601.18606 |
221,184 |
19-Sep-2014 |
09:23 |
x86 |
|
Ncrypt.dll |
6.1.7601.22923 |
220,160 |
14-Jan-2015 |
06:21 |
x86 |
|
Ntkrnlpa.exe |
6.1.7601.18717 |
3,972,544 |
14-Jan-2015 |
05:44 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.18717 |
3,917,760 |
14-Jan-2015 |
05:44 |
Not applicable |
|
Ntkrnlpa.exe |
6.1.7601.22923 |
3,977,656 |
14-Jan-2015 |
06:25 |
Not applicable |
|
Ntoskrnl.exe |
6.1.7601.22923 |
3,921,848 |
14-Jan-2015 |
06:25 |
Not applicable |
|
Credssp.dll |
6.1.7601.18606 |
17,408 |
19-Sep-2014 |
09:23 |
x86 |
|
Tspkg.dll |
6.1.7601.18606 |
65,536 |
19-Sep-2014 |
09:23 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
04-Jul-2013 |
12:24 |
Not applicable |
|
Credssp.dll |
6.1.7601.22750 |
17,408 |
16-Jul-2014 |
02:56 |
x86 |
|
Tspkg.dll |
6.1.7601.22750 |
65,536 |
16-Jul-2014 |
02:56 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
09-Jul-2013 |
06:39 |
Not applicable |
-
The files that apply to a specific product, milestone (RTM,SPn), and service branch (LDR, GDR) can be identified by examining the file version numbers as shown in the following table:
Version
Product
Milestone
Service branch
6.2.920 0.16 xxx
Windows 8 and Windows Server 2012
RTM
GDR
6.2.920 0.20 xxx
Windows 8 and Windows Server 2012
RTM
LDR
-
GDR service branches contain only those fixes that are widely released to address widespread, critical issues. LDR service branches contain hotfixes in addition to widely released fixes.
Note The MANIFEST files (.manifest) and MUM files (.mum) that are installed are not listed.
For all supported x86-based versions of Windows 8
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
08:00 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
08:00 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,960 |
12-Apr-2014 |
09:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
43,008 |
12-Apr-2014 |
09:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
46,080 |
12-Apr-2014 |
07:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
48,128 |
12-Apr-2014 |
09:36 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:18 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,960 |
12-Apr-2014 |
07:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
45,056 |
12-Apr-2014 |
07:56 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:07 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:24 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
47,616 |
12-Apr-2014 |
07:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,448 |
12-Apr-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:07 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,544 |
12-Apr-2014 |
09:13 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
45,056 |
12-Apr-2014 |
09:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
28,160 |
12-Apr-2014 |
07:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
27,648 |
12-Apr-2014 |
09:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
09:42 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
08:59 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:26 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
46,592 |
12-Apr-2014 |
08:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,544 |
12-Apr-2014 |
09:44 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
43,008 |
12-Apr-2014 |
09:36 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,544 |
12-Apr-2014 |
09:03 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
08:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,032 |
12-Apr-2014 |
08:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
08:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
08:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.17218 |
41,472 |
18-Dec-2014 |
08:30 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
08:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,960 |
12-Apr-2014 |
09:00 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
42,496 |
12-Apr-2014 |
09:36 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
22,528 |
12-Apr-2014 |
09:26 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
23,040 |
12-Apr-2014 |
08:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
23,040 |
12-Apr-2014 |
09:06 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
08:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
08:20 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,960 |
12-Apr-2014 |
10:34 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
43,008 |
12-Apr-2014 |
09:23 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
46,080 |
12-Apr-2014 |
08:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
48,128 |
12-Apr-2014 |
09:46 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:32 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,960 |
12-Apr-2014 |
08:12 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
45,056 |
12-Apr-2014 |
08:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:40 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
47,616 |
12-Apr-2014 |
08:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,448 |
12-Apr-2014 |
09:27 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,544 |
12-Apr-2014 |
09:22 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
45,056 |
12-Apr-2014 |
09:33 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
28,160 |
12-Apr-2014 |
08:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
27,648 |
12-Apr-2014 |
09:32 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
09:21 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
09:21 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
10:35 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
46,592 |
12-Apr-2014 |
09:35 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,544 |
12-Apr-2014 |
09:23 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
43,008 |
12-Apr-2014 |
09:43 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,544 |
12-Apr-2014 |
10:28 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
09:39 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,032 |
12-Apr-2014 |
09:33 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
09:54 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21317 |
41,472 |
18-Dec-2014 |
02:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:26 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:22 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,960 |
12-Apr-2014 |
09:37 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
42,496 |
12-Apr-2014 |
09:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
22,528 |
12-Apr-2014 |
09:22 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
23,040 |
12-Apr-2014 |
09:37 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
23,040 |
12-Apr-2014 |
09:22 |
Not applicable |
|
Cng.sys |
6.2.9200.17200 |
493,256 |
09-Dec-2014 |
23:14 |
x86 |
|
Ksecpkg.sys |
6.2.9200.17150 |
156,480 |
11-Oct-2014 |
06:18 |
x86 |
|
Lsasrv.dll |
6.2.9200.17218 |
1,026,560 |
18-Dec-2014 |
06:19 |
x86 |
|
Cng.sys |
6.2.9200.21317 |
494,280 |
09-Dec-2014 |
23:15 |
x86 |
|
Ksecpkg.sys |
6.2.9200.21269 |
156,480 |
11-Oct-2014 |
05:58 |
x86 |
|
Lsasrv.dll |
6.2.9200.21317 |
1,033,728 |
18-Dec-2014 |
00:37 |
x86 |
|
Adtschema.dll.mui |
6.2.9200.17218 |
277,504 |
18-Dec-2014 |
08:25 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
165,376 |
11-Oct-2014 |
08:07 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
267,776 |
18-Dec-2014 |
07:46 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
157,184 |
11-Oct-2014 |
07:29 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
69,632 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
294,400 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
160,768 |
11-Oct-2014 |
06:04 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
05:28 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
325,120 |
18-Dec-2014 |
07:40 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
187,904 |
11-Oct-2014 |
07:22 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
77,312 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
262,144 |
18-Dec-2014 |
06:38 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
146,944 |
11-Oct-2014 |
06:17 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
312,320 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
185,856 |
11-Oct-2014 |
06:06 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:01 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
268,800 |
18-Dec-2014 |
08:53 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
161,280 |
11-Oct-2014 |
08:29 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
06:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
329,728 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
183,808 |
11-Oct-2014 |
06:04 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
295,936 |
18-Dec-2014 |
09:08 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
171,520 |
11-Oct-2014 |
08:21 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
79,872 |
26-Jul-2012 |
06:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
297,472 |
18-Dec-2014 |
07:46 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
168,960 |
11-Oct-2014 |
07:27 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
04:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
185,856 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
111,104 |
11-Oct-2014 |
06:06 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,544 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
166,912 |
18-Dec-2014 |
07:41 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
101,888 |
11-Oct-2014 |
07:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,032 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
09:30 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
154,112 |
11-Oct-2014 |
08:28 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
283,648 |
18-Dec-2014 |
07:54 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
166,912 |
11-Oct-2014 |
07:40 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
06:37 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
306,688 |
18-Dec-2014 |
07:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
180,736 |
11-Oct-2014 |
07:26 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,776 |
26-Jul-2012 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
309,760 |
18-Dec-2014 |
07:41 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
181,760 |
11-Oct-2014 |
07:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
05:12 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
304,128 |
18-Dec-2014 |
07:59 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
181,760 |
11-Oct-2014 |
07:48 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
70,656 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
298,496 |
18-Dec-2014 |
07:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
164,352 |
11-Oct-2014 |
07:44 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
78,848 |
26-Jul-2012 |
04:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
08:17 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
161,792 |
11-Oct-2014 |
07:39 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
05:08 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
07:48 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
160,256 |
11-Oct-2014 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
63,488 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
141,824 |
18-Dec-2014 |
08:40 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
87,040 |
11-Oct-2014 |
08:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
34,304 |
26-Jul-2012 |
06:38 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
145,408 |
18-Dec-2014 |
08:39 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
90,112 |
11-Oct-2014 |
08:22 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
145,408 |
18-Dec-2014 |
07:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
90,112 |
11-Oct-2014 |
07:41 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
277,504 |
18-Dec-2014 |
03:30 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
165,376 |
11-Oct-2014 |
06:46 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
267,776 |
18-Dec-2014 |
02:31 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
157,184 |
11-Oct-2014 |
07:10 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
69,632 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
294,912 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
160,768 |
11-Oct-2014 |
05:34 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
05:28 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
325,632 |
18-Dec-2014 |
02:21 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
187,904 |
11-Oct-2014 |
07:35 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
77,312 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
262,144 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
146,944 |
11-Oct-2014 |
05:30 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
312,832 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
185,856 |
11-Oct-2014 |
05:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:01 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
268,800 |
18-Dec-2014 |
02:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
161,280 |
11-Oct-2014 |
07:08 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
06:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
329,728 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
183,808 |
11-Oct-2014 |
05:32 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
296,448 |
18-Dec-2014 |
02:33 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
171,520 |
11-Oct-2014 |
06:52 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
79,872 |
26-Jul-2012 |
06:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
297,984 |
18-Dec-2014 |
03:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
168,960 |
11-Oct-2014 |
06:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
04:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
185,856 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
111,104 |
11-Oct-2014 |
05:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,544 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
166,912 |
18-Dec-2014 |
02:30 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
101,888 |
11-Oct-2014 |
06:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,032 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
270,848 |
18-Dec-2014 |
02:58 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
154,112 |
11-Oct-2014 |
07:08 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
284,160 |
18-Dec-2014 |
03:34 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
166,912 |
11-Oct-2014 |
08:10 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
06:37 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
306,688 |
18-Dec-2014 |
02:40 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
180,736 |
11-Oct-2014 |
07:03 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,776 |
26-Jul-2012 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
310,272 |
18-Dec-2014 |
03:20 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
181,760 |
11-Oct-2014 |
07:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
05:12 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
304,640 |
18-Dec-2014 |
02:20 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
181,760 |
11-Oct-2014 |
06:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
70,656 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
299,008 |
18-Dec-2014 |
02:28 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
164,352 |
11-Oct-2014 |
06:53 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
78,848 |
26-Jul-2012 |
04:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
270,336 |
18-Dec-2014 |
02:27 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
161,792 |
11-Oct-2014 |
08:01 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
05:08 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
270,336 |
18-Dec-2014 |
03:13 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
160,256 |
11-Oct-2014 |
07:34 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
63,488 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
141,824 |
18-Dec-2014 |
02:24 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
87,040 |
11-Oct-2014 |
06:46 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
34,304 |
26-Jul-2012 |
06:38 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
145,408 |
18-Dec-2014 |
03:32 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
90,112 |
11-Oct-2014 |
08:11 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
145,408 |
18-Dec-2014 |
03:16 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
90,112 |
11-Oct-2014 |
07:38 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll |
6.2.9200.17218 |
717,824 |
18-Dec-2014 |
04:15 |
x86 |
|
Msaudite.dll |
6.2.9200.17150 |
146,944 |
11-Oct-2014 |
05:05 |
x86 |
|
Msobjs.dll |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
02:47 |
x86 |
|
Adtschema.dll |
6.2.9200.21317 |
719,360 |
08-Dec-2014 |
03:40 |
x86 |
|
Msaudite.dll |
6.2.9200.21269 |
146,944 |
11-Oct-2014 |
04:35 |
x86 |
|
Msobjs.dll |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
02:47 |
x86 |
|
Ntoskrnl.exe |
6.2.9200.17218 |
5,573,952 |
18-Dec-2014 |
07:05 |
Not applicable |
|
Ntoskrnl.exe |
6.2.9200.21317 |
5,538,112 |
18-Dec-2014 |
00:54 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,103 |
18-Dec-2014 |
07:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
18-Dec-2014 |
08:08 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
18-Dec-2014 |
06:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
18-Dec-2014 |
07:53 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
18-Dec-2014 |
06:51 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
18-Dec-2014 |
06:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
18-Dec-2014 |
07:41 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
18-Dec-2014 |
06:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
18-Dec-2014 |
07:44 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
18-Dec-2014 |
08:26 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
18-Dec-2014 |
06:47 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
18-Dec-2014 |
08:18 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
18-Dec-2014 |
08:40 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
18-Dec-2014 |
07:42 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
18-Dec-2014 |
09:28 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
18-Dec-2014 |
07:54 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
18-Dec-2014 |
08:13 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
18-Dec-2014 |
07:51 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
18-Dec-2014 |
08:15 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
18-Dec-2014 |
07:49 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
18-Dec-2014 |
08:14 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
07:59 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
07:43 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,103 |
18-Dec-2014 |
02:36 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
18-Dec-2014 |
02:56 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
18-Dec-2014 |
01:12 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
18-Dec-2014 |
02:38 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
18-Dec-2014 |
01:13 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
18-Dec-2014 |
01:14 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
18-Dec-2014 |
02:22 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
18-Dec-2014 |
01:12 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
18-Dec-2014 |
03:10 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
18-Dec-2014 |
02:52 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
18-Dec-2014 |
01:11 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
18-Dec-2014 |
02:36 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
18-Dec-2014 |
02:54 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
18-Dec-2014 |
03:08 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
18-Dec-2014 |
02:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
18-Dec-2014 |
02:41 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
18-Dec-2014 |
02:55 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
18-Dec-2014 |
02:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
18-Dec-2014 |
02:21 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
18-Dec-2014 |
02:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
18-Dec-2014 |
03:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
02:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
02:22 |
Not applicable |
|
Credssp.dll |
6.2.9200.16891 |
17,408 |
12-Apr-2014 |
07:22 |
x86 |
|
Tspkg.dll |
6.2.9200.16891 |
76,800 |
12-Apr-2014 |
07:23 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
02-Jun-2012 |
14:33 |
Not applicable |
|
Credssp.dll |
6.2.9200.21012 |
17,408 |
12-Apr-2014 |
07:31 |
x86 |
|
Tspkg.dll |
6.2.9200.21012 |
76,800 |
12-Apr-2014 |
07:32 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
02-Jun-2012 |
14:33 |
Not applicable |
|
Wdigest.dll |
6.2.9200.16891 |
178,688 |
12-Apr-2014 |
07:23 |
x86 |
|
Wdigest.dll |
6.2.9200.21012 |
176,640 |
12-Apr-2014 |
07:32 |
x86 |
|
Kerberos.dll |
6.2.9200.17172 |
666,624 |
08-Nov-2014 |
06:56 |
x86 |
|
Kerberos.dll |
6.2.9200.21289 |
663,552 |
10-Nov-2014 |
23:30 |
x86 |
|
Msv1_0.dll |
6.2.9200.16891 |
273,920 |
12-Apr-2014 |
07:23 |
x86 |
|
Msv1_0.dll |
6.2.9200.21012 |
273,920 |
12-Apr-2014 |
07:31 |
x86 |
|
Auditsettings.admx |
Not applicable |
1,337 |
16-Dec-2014 |
01:34 |
Not applicable |
|
Auditsettings.admx |
Not applicable |
1,337 |
19-Oct-2014 |
22:09 |
Not applicable |
|
Shcore.dll |
6.2.9200.17218 |
452,608 |
18-Dec-2014 |
06:20 |
x86 |
|
Shcore.dll |
6.2.9200.21317 |
460,800 |
18-Dec-2014 |
00:38 |
x86 |
|
Lsm.dll |
6.2.9200.16891 |
350,720 |
12-Apr-2014 |
07:23 |
x86 |
|
Workerdd.dll |
6.2.9200.16384 |
12,288 |
26-Jul-2012 |
02:38 |
x86 |
|
Lsm.dll |
6.2.9200.21012 |
350,720 |
12-Apr-2014 |
07:31 |
x86 |
|
Workerdd.dll |
6.2.9200.16384 |
12,288 |
26-Jul-2012 |
02:38 |
x86 |
|
Usercpl.dll |
6.2.9200.17218 |
961,536 |
18-Dec-2014 |
06:20 |
x86 |
|
Usercpl.ptxml |
Not applicable |
789 |
11-Oct-2012 |
00:41 |
Not applicable |
|
Usercpl.dll |
6.2.9200.21012 |
961,536 |
12-Apr-2014 |
07:32 |
x86 |
|
Usercpl.ptxml |
Not applicable |
789 |
11-Oct-2012 |
00:42 |
Not applicable |
|
Winlogon.exe |
6.2.9200.16891 |
429,056 |
12-Apr-2014 |
07:24 |
x86 |
|
Winlogon.exe |
6.2.9200.21012 |
429,056 |
12-Apr-2014 |
07:33 |
x86 |
For all supported x64-based versions of Windows 8 and Windows Server 2012
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
09:59 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
09:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,960 |
12-Apr-2014 |
11:21 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
43,008 |
12-Apr-2014 |
13:08 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
46,080 |
12-Apr-2014 |
09:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
48,128 |
12-Apr-2014 |
10:54 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
13:11 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,960 |
12-Apr-2014 |
09:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
45,056 |
12-Apr-2014 |
09:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
10:54 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
11:09 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
47,616 |
12-Apr-2014 |
09:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,448 |
12-Apr-2014 |
12:59 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
13:41 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,544 |
12-Apr-2014 |
13:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
45,056 |
12-Apr-2014 |
10:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
28,160 |
12-Apr-2014 |
09:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
27,648 |
12-Apr-2014 |
13:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
11:08 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
13:34 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
10:59 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
46,592 |
12-Apr-2014 |
10:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,544 |
12-Apr-2014 |
10:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
43,008 |
12-Apr-2014 |
11:06 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,544 |
12-Apr-2014 |
10:57 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
13:28 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
44,032 |
12-Apr-2014 |
11:18 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,984 |
12-Apr-2014 |
11:20 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
12:46 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.17218 |
41,472 |
18-Dec-2014 |
10:52 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
10:58 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
41,472 |
12-Apr-2014 |
13:40 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
40,960 |
12-Apr-2014 |
13:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
42,496 |
12-Apr-2014 |
11:21 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
22,528 |
12-Apr-2014 |
13:16 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
23,040 |
12-Apr-2014 |
13:54 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.16891 |
23,040 |
12-Apr-2014 |
11:45 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
09:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
09:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,960 |
12-Apr-2014 |
12:31 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
43,008 |
12-Apr-2014 |
11:43 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
46,080 |
12-Apr-2014 |
09:52 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
48,128 |
12-Apr-2014 |
13:41 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
12:01 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,960 |
12-Apr-2014 |
09:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
45,056 |
12-Apr-2014 |
09:51 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
13:39 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
12:41 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
47,616 |
12-Apr-2014 |
09:52 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,448 |
12-Apr-2014 |
13:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
13:04 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,544 |
12-Apr-2014 |
13:01 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
45,056 |
12-Apr-2014 |
12:16 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
28,160 |
12-Apr-2014 |
09:52 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
27,648 |
12-Apr-2014 |
11:39 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
12:55 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
12:38 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
12:10 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
46,592 |
12-Apr-2014 |
11:46 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,544 |
12-Apr-2014 |
11:46 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
43,008 |
12-Apr-2014 |
11:43 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,544 |
12-Apr-2014 |
11:54 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
13:07 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
44,032 |
12-Apr-2014 |
11:43 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,984 |
12-Apr-2014 |
11:48 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
12:20 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21317 |
41,472 |
18-Dec-2014 |
04:36 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
13:24 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
41,472 |
12-Apr-2014 |
12:33 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
40,960 |
12-Apr-2014 |
11:47 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
42,496 |
12-Apr-2014 |
11:44 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
22,528 |
12-Apr-2014 |
11:46 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
23,040 |
12-Apr-2014 |
12:36 |
Not applicable |
|
Lsasrv.dll.mui |
6.2.9200.21012 |
23,040 |
12-Apr-2014 |
12:12 |
Not applicable |
|
Cng.sys |
6.2.9200.17200 |
569,720 |
09-Dec-2014 |
23:14 |
x64 |
|
Ksecpkg.sys |
6.2.9200.17150 |
171,840 |
11-Oct-2014 |
08:35 |
x64 |
|
Lsasrv.dll |
6.2.9200.17218 |
1,282,560 |
18-Dec-2014 |
06:51 |
x64 |
|
Cng.sys |
6.2.9200.21317 |
565,072 |
09-Dec-2014 |
23:15 |
x64 |
|
Ksecpkg.sys |
6.2.9200.21269 |
171,840 |
11-Oct-2014 |
07:50 |
x64 |
|
Lsasrv.dll |
6.2.9200.21317 |
1,280,512 |
18-Dec-2014 |
00:46 |
x64 |
|
Adtschema.dll.mui |
6.2.9200.17218 |
277,504 |
18-Dec-2014 |
11:01 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
165,376 |
11-Oct-2014 |
11:16 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
07:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
267,776 |
18-Dec-2014 |
11:02 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
157,184 |
11-Oct-2014 |
09:34 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
69,632 |
26-Jul-2012 |
07:31 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
294,400 |
18-Dec-2014 |
08:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
160,768 |
11-Oct-2014 |
08:19 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
07:46 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
325,120 |
18-Dec-2014 |
09:35 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
187,904 |
11-Oct-2014 |
10:16 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
77,312 |
26-Jul-2012 |
07:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
262,144 |
18-Dec-2014 |
06:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
146,944 |
11-Oct-2014 |
08:18 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
312,320 |
18-Dec-2014 |
06:56 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
185,856 |
11-Oct-2014 |
08:19 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:06 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
268,800 |
18-Dec-2014 |
10:31 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
161,280 |
11-Oct-2014 |
09:28 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
05:05 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
329,728 |
18-Dec-2014 |
07:05 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
183,808 |
11-Oct-2014 |
08:18 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:05 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
295,936 |
18-Dec-2014 |
10:58 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
171,520 |
11-Oct-2014 |
11:00 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
79,872 |
26-Jul-2012 |
07:49 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
297,472 |
18-Dec-2014 |
09:20 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
168,960 |
11-Oct-2014 |
11:08 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
08:01 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
185,856 |
18-Dec-2014 |
06:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
111,104 |
11-Oct-2014 |
08:19 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,544 |
26-Jul-2012 |
08:40 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
166,912 |
18-Dec-2014 |
09:49 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
101,888 |
11-Oct-2014 |
10:09 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,032 |
26-Jul-2012 |
05:19 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
10:30 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
154,112 |
11-Oct-2014 |
10:14 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
05:05 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
283,648 |
18-Dec-2014 |
09:21 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
166,912 |
11-Oct-2014 |
09:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
07:50 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
306,688 |
18-Dec-2014 |
10:35 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
180,736 |
11-Oct-2014 |
09:39 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,776 |
26-Jul-2012 |
05:06 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
309,760 |
18-Dec-2014 |
10:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
181,760 |
11-Oct-2014 |
10:30 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
08:00 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
304,128 |
18-Dec-2014 |
11:34 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
181,760 |
11-Oct-2014 |
09:34 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
70,656 |
26-Jul-2012 |
08:06 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
298,496 |
18-Dec-2014 |
10:22 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
164,352 |
11-Oct-2014 |
10:20 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
78,848 |
26-Jul-2012 |
05:26 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
10:47 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
161,792 |
11-Oct-2014 |
09:22 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
07:46 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
09:24 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
160,256 |
11-Oct-2014 |
10:09 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
63,488 |
26-Jul-2012 |
05:40 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
141,824 |
18-Dec-2014 |
09:30 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
87,040 |
11-Oct-2014 |
09:22 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
34,304 |
26-Jul-2012 |
07:38 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
145,408 |
18-Dec-2014 |
10:44 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
90,112 |
11-Oct-2014 |
10:36 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
07:29 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
145,408 |
18-Dec-2014 |
10:22 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
90,112 |
11-Oct-2014 |
10:13 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
05:19 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
277,504 |
11-Nov-2014 |
03:55 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
165,376 |
11-Oct-2014 |
10:03 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
07:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
267,776 |
11-Nov-2014 |
05:22 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
157,184 |
11-Oct-2014 |
09:24 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
69,632 |
26-Jul-2012 |
07:31 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
294,912 |
11-Nov-2014 |
02:02 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
160,768 |
11-Oct-2014 |
07:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
07:46 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
325,632 |
11-Nov-2014 |
03:49 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
187,904 |
11-Oct-2014 |
08:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
77,312 |
26-Jul-2012 |
07:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
262,144 |
11-Nov-2014 |
02:01 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
146,944 |
11-Oct-2014 |
07:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
312,832 |
18-Dec-2014 |
03:11 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
185,856 |
11-Oct-2014 |
07:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:06 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
268,800 |
11-Nov-2014 |
04:16 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
161,280 |
11-Oct-2014 |
10:20 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
05:05 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
329,728 |
18-Dec-2014 |
03:05 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
183,808 |
11-Oct-2014 |
07:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:05 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
296,448 |
11-Nov-2014 |
04:35 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
171,520 |
11-Oct-2014 |
10:13 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
79,872 |
26-Jul-2012 |
07:49 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
297,984 |
11-Nov-2014 |
04:32 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
168,960 |
11-Oct-2014 |
10:02 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
08:01 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
185,856 |
11-Nov-2014 |
02:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
111,104 |
11-Oct-2014 |
07:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,544 |
26-Jul-2012 |
08:40 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
166,912 |
11-Nov-2014 |
03:50 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
101,888 |
11-Oct-2014 |
08:53 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,032 |
26-Jul-2012 |
05:19 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
270,848 |
11-Nov-2014 |
04:33 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
154,112 |
11-Oct-2014 |
08:45 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
05:05 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
284,160 |
11-Nov-2014 |
04:24 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
166,912 |
11-Oct-2014 |
09:28 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
07:50 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
306,688 |
11-Nov-2014 |
04:53 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
180,736 |
11-Oct-2014 |
09:56 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,776 |
26-Jul-2012 |
05:06 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
310,272 |
18-Dec-2014 |
04:38 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
181,760 |
11-Oct-2014 |
09:15 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
08:00 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
304,640 |
18-Dec-2014 |
04:29 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
181,760 |
11-Oct-2014 |
09:55 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
70,656 |
26-Jul-2012 |
08:06 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
299,008 |
18-Dec-2014 |
04:01 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
164,352 |
11-Oct-2014 |
09:20 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
78,848 |
26-Jul-2012 |
05:26 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
270,336 |
11-Nov-2014 |
04:19 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
161,792 |
11-Oct-2014 |
09:26 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
07:46 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
270,336 |
18-Dec-2014 |
05:02 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
160,256 |
11-Oct-2014 |
08:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
63,488 |
26-Jul-2012 |
05:40 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
141,824 |
11-Nov-2014 |
03:51 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
87,040 |
11-Oct-2014 |
08:53 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
34,304 |
26-Jul-2012 |
07:38 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
145,408 |
11-Nov-2014 |
03:56 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
90,112 |
11-Oct-2014 |
08:51 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
07:29 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
145,408 |
11-Nov-2014 |
04:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
90,112 |
11-Oct-2014 |
10:16 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
05:19 |
Not applicable |
|
Adtschema.dll |
6.2.9200.17218 |
717,824 |
18-Dec-2014 |
04:47 |
x64 |
|
Msaudite.dll |
6.2.9200.17150 |
146,944 |
11-Oct-2014 |
05:41 |
x64 |
|
Msobjs.dll |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
02:36 |
x64 |
|
Adtschema.dll |
6.2.9200.21289 |
719,360 |
10-Nov-2014 |
04:43 |
x64 |
|
Msaudite.dll |
6.2.9200.21269 |
146,944 |
11-Oct-2014 |
05:38 |
x64 |
|
Msobjs.dll |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
02:36 |
x64 |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
12:32 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,960 |
26-Jul-2012 |
05:07 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
10,752 |
12-Apr-2014 |
09:54 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,134 |
26-Jul-2012 |
08:00 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
09:53 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,918 |
26-Jul-2012 |
04:43 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
11,264 |
12-Apr-2014 |
09:53 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,210 |
26-Jul-2012 |
07:59 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
11,776 |
12-Apr-2014 |
09:53 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,098 |
26-Jul-2012 |
08:00 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
13:02 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,028 |
26-Jul-2012 |
07:59 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
10,752 |
12-Apr-2014 |
12:17 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,140 |
26-Jul-2012 |
05:21 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
6,656 |
12-Apr-2014 |
09:54 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,642 |
26-Jul-2012 |
08:11 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
6,144 |
12-Apr-2014 |
11:41 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,576 |
26-Jul-2012 |
05:20 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
11:47 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,026 |
26-Jul-2012 |
07:36 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
11:47 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,028 |
26-Jul-2012 |
07:48 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
10,752 |
12-Apr-2014 |
11:44 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,188 |
26-Jul-2012 |
05:30 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
11:54 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,126 |
26-Jul-2012 |
05:08 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
10,240 |
12-Apr-2014 |
11:44 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,064 |
26-Jul-2012 |
07:49 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
13:25 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
3,092 |
26-Jul-2012 |
07:52 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
9,728 |
12-Apr-2014 |
11:48 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,828 |
26-Jul-2012 |
05:12 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
5,120 |
12-Apr-2014 |
11:47 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,464 |
26-Jul-2012 |
08:05 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
5,120 |
12-Apr-2014 |
12:36 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,480 |
26-Jul-2012 |
05:13 |
Not applicable |
|
Ocspsvc.exe.mui |
6.2.9200.21012 |
5,120 |
12-Apr-2014 |
12:13 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,460 |
26-Jul-2012 |
08:11 |
Not applicable |
|
Ocspsvc.exe |
6.2.9200.21317 |
272,384 |
18-Dec-2014 |
00:46 |
x64 |
|
Ocspsvcctrs.h |
Not applicable |
1,569 |
02-Jun-2012 |
14:34 |
Not applicable |
|
Ocspsvcctrs.ini |
Not applicable |
2,918 |
02-Jun-2012 |
14:34 |
Not applicable |
|
Ntoskrnl.exe |
6.2.9200.17218 |
6,973,760 |
18-Dec-2014 |
08:48 |
x64 |
|
Ntoskrnl.exe |
6.2.9200.21317 |
6,941,504 |
18-Dec-2014 |
02:53 |
x64 |
|
Auditsettings.adml |
Not applicable |
2,103 |
18-Dec-2014 |
10:57 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
18-Dec-2014 |
09:35 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
18-Dec-2014 |
08:45 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
18-Dec-2014 |
09:33 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
18-Dec-2014 |
08:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
18-Dec-2014 |
08:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
18-Dec-2014 |
09:27 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
18-Dec-2014 |
08:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
18-Dec-2014 |
10:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
18-Dec-2014 |
10:56 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
18-Dec-2014 |
08:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
18-Dec-2014 |
09:24 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
18-Dec-2014 |
09:26 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
18-Dec-2014 |
10:43 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
18-Dec-2014 |
11:54 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
18-Dec-2014 |
11:28 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
18-Dec-2014 |
09:24 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
18-Dec-2014 |
10:34 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
18-Dec-2014 |
09:28 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
18-Dec-2014 |
09:30 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
18-Dec-2014 |
09:43 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
09:24 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
11:37 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,103 |
18-Dec-2014 |
04:09 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,984 |
18-Dec-2014 |
05:53 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,123 |
18-Dec-2014 |
02:53 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
3,373 |
18-Dec-2014 |
05:14 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,846 |
18-Dec-2014 |
02:53 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,136 |
18-Dec-2014 |
02:53 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,962 |
18-Dec-2014 |
04:19 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,233 |
18-Dec-2014 |
02:51 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,081 |
18-Dec-2014 |
04:03 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,173 |
18-Dec-2014 |
04:03 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,208 |
18-Dec-2014 |
02:51 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,018 |
18-Dec-2014 |
05:25 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,957 |
18-Dec-2014 |
04:46 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,019 |
18-Dec-2014 |
04:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,163 |
18-Dec-2014 |
04:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,161 |
18-Dec-2014 |
04:06 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,152 |
18-Dec-2014 |
04:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
2,974 |
18-Dec-2014 |
04:05 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,976 |
18-Dec-2014 |
04:40 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,986 |
18-Dec-2014 |
04:22 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,637 |
18-Dec-2014 |
04:38 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
04:12 |
Not applicable |
|
Auditsettings.adml |
Not applicable |
1,761 |
18-Dec-2014 |
04:42 |
Not applicable |
|
Credssp.dll |
6.2.9200.16891 |
20,480 |
12-Apr-2014 |
09:07 |
x64 |
|
Tspkg.dll |
6.2.9200.16891 |
94,720 |
12-Apr-2014 |
09:09 |
x64 |
|
Tspkg.mof |
Not applicable |
964 |
02-Jun-2012 |
14:33 |
Not applicable |
|
Credssp.dll |
6.2.9200.21012 |
20,480 |
12-Apr-2014 |
07:49 |
x64 |
|
Tspkg.dll |
6.2.9200.21012 |
94,720 |
12-Apr-2014 |
07:51 |
x64 |
|
Tspkg.mof |
Not applicable |
964 |
02-Jun-2012 |
14:33 |
Not applicable |
|
Wdigest.dll |
6.2.9200.16891 |
208,896 |
12-Apr-2014 |
09:09 |
x64 |
|
Wdigest.dll |
6.2.9200.21012 |
208,896 |
12-Apr-2014 |
07:51 |
x64 |
|
Kerberos.dll |
6.2.9200.17172 |
827,904 |
08-Nov-2014 |
11:21 |
x64 |
|
Kerberos.dll |
6.2.9200.21289 |
827,392 |
10-Nov-2014 |
23:27 |
x64 |
|
Msv1_0.dll |
6.2.9200.16891 |
318,464 |
12-Apr-2014 |
09:08 |
x64 |
|
Msv1_0.dll |
6.2.9200.21012 |
317,440 |
12-Apr-2014 |
07:50 |
x64 |
|
Auditsettings.admx |
Not applicable |
1,337 |
16-Dec-2014 |
01:35 |
Not applicable |
|
Auditsettings.admx |
Not applicable |
1,337 |
19-Oct-2014 |
22:10 |
Not applicable |
|
Shcore.dll |
6.2.9200.17218 |
588,800 |
18-Dec-2014 |
06:52 |
x64 |
|
Shcore.dll |
6.2.9200.21317 |
591,360 |
18-Dec-2014 |
00:46 |
x64 |
|
Lsm.dll |
6.2.9200.16931 |
439,808 |
29-May-2014 |
23:02 |
x64 |
|
Workerdd.dll |
6.2.9200.16891 |
14,848 |
12-Apr-2014 |
06:58 |
x64 |
|
Lsm.dll |
6.2.9200.21012 |
439,808 |
12-Apr-2014 |
07:49 |
x64 |
|
Workerdd.dll |
6.2.9200.21012 |
14,848 |
12-Apr-2014 |
06:58 |
x64 |
|
Usercpl.dll |
6.2.9200.17218 |
1,043,968 |
18-Dec-2014 |
06:52 |
x64 |
|
Usercpl.ptxml |
Not applicable |
789 |
11-Oct-2012 |
00:40 |
Not applicable |
|
Usercpl.dll |
6.2.9200.21012 |
1,043,968 |
12-Apr-2014 |
07:51 |
x64 |
|
Usercpl.ptxml |
Not applicable |
789 |
11-Oct-2012 |
00:40 |
Not applicable |
|
Winlogon.exe |
6.2.9200.16891 |
578,048 |
12-Apr-2014 |
09:10 |
x64 |
|
Winlogon.exe |
6.2.9200.21012 |
578,048 |
12-Apr-2014 |
07:52 |
x64 |
|
Wdigest.dll |
6.2.9200.16891 |
178,688 |
12-Apr-2014 |
07:23 |
x86 |
|
Wdigest.dll |
6.2.9200.21012 |
176,640 |
12-Apr-2014 |
07:32 |
x86 |
|
Kerberos.dll |
6.2.9200.17172 |
666,624 |
08-Nov-2014 |
06:56 |
x86 |
|
Kerberos.dll |
6.2.9200.21289 |
663,552 |
10-Nov-2014 |
23:30 |
x86 |
|
Msv1_0.dll |
6.2.9200.16891 |
273,920 |
12-Apr-2014 |
07:23 |
x86 |
|
Msv1_0.dll |
6.2.9200.21012 |
273,920 |
12-Apr-2014 |
07:31 |
x86 |
|
Adtschema.dll.mui |
6.2.9200.17218 |
277,504 |
18-Dec-2014 |
08:25 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
165,376 |
11-Oct-2014 |
08:07 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
267,776 |
18-Dec-2014 |
07:46 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
157,184 |
11-Oct-2014 |
07:29 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
69,632 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
294,400 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
160,768 |
11-Oct-2014 |
06:04 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
05:28 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
325,120 |
18-Dec-2014 |
07:40 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
187,904 |
11-Oct-2014 |
07:22 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
77,312 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
262,144 |
18-Dec-2014 |
06:38 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
146,944 |
11-Oct-2014 |
06:17 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
312,320 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
185,856 |
11-Oct-2014 |
06:06 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:01 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
268,800 |
18-Dec-2014 |
08:53 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
161,280 |
11-Oct-2014 |
08:29 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
06:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
329,728 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
183,808 |
11-Oct-2014 |
06:04 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
295,936 |
18-Dec-2014 |
09:08 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
171,520 |
11-Oct-2014 |
08:21 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
79,872 |
26-Jul-2012 |
06:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
297,472 |
18-Dec-2014 |
07:46 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
168,960 |
11-Oct-2014 |
07:27 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
04:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
185,856 |
18-Dec-2014 |
06:37 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
111,104 |
11-Oct-2014 |
06:06 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,544 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
166,912 |
18-Dec-2014 |
07:41 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
101,888 |
11-Oct-2014 |
07:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,032 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
09:30 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
154,112 |
11-Oct-2014 |
08:28 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
283,648 |
18-Dec-2014 |
07:54 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
166,912 |
11-Oct-2014 |
07:40 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
06:37 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
306,688 |
18-Dec-2014 |
07:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
180,736 |
11-Oct-2014 |
07:26 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,776 |
26-Jul-2012 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
309,760 |
18-Dec-2014 |
07:41 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
181,760 |
11-Oct-2014 |
07:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
05:12 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
304,128 |
18-Dec-2014 |
07:59 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
181,760 |
11-Oct-2014 |
07:48 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
70,656 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
298,496 |
18-Dec-2014 |
07:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
164,352 |
11-Oct-2014 |
07:44 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
78,848 |
26-Jul-2012 |
04:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
08:17 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
161,792 |
11-Oct-2014 |
07:39 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
05:08 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
270,336 |
18-Dec-2014 |
07:48 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
160,256 |
11-Oct-2014 |
07:31 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
63,488 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
141,824 |
18-Dec-2014 |
08:40 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
87,040 |
11-Oct-2014 |
08:23 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
34,304 |
26-Jul-2012 |
06:38 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
145,408 |
18-Dec-2014 |
08:39 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
90,112 |
11-Oct-2014 |
08:22 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.17218 |
145,408 |
18-Dec-2014 |
07:57 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.17150 |
90,112 |
11-Oct-2014 |
07:41 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
277,504 |
11-Nov-2014 |
02:48 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
165,376 |
11-Oct-2014 |
06:46 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
267,776 |
11-Nov-2014 |
01:20 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
157,184 |
11-Oct-2014 |
07:10 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
69,632 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
294,912 |
10-Nov-2014 |
23:53 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
160,768 |
11-Oct-2014 |
05:34 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,264 |
26-Jul-2012 |
05:28 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
325,632 |
11-Nov-2014 |
01:10 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
187,904 |
11-Oct-2014 |
07:35 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
77,312 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
262,144 |
10-Nov-2014 |
23:53 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
146,944 |
11-Oct-2014 |
05:30 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
03:27 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
312,832 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
185,856 |
11-Oct-2014 |
05:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
05:01 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
268,800 |
11-Nov-2014 |
01:31 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
161,280 |
11-Oct-2014 |
07:08 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
06:41 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
329,728 |
18-Dec-2014 |
01:00 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
183,808 |
11-Oct-2014 |
05:32 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,168 |
26-Jul-2012 |
04:45 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
296,448 |
11-Nov-2014 |
01:23 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
171,520 |
11-Oct-2014 |
06:52 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
79,872 |
26-Jul-2012 |
06:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
297,984 |
11-Nov-2014 |
01:16 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
168,960 |
11-Oct-2014 |
06:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
04:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
185,856 |
10-Nov-2014 |
23:53 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
111,104 |
11-Oct-2014 |
05:33 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,544 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
166,912 |
11-Nov-2014 |
01:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
101,888 |
11-Oct-2014 |
06:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
44,032 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
270,848 |
11-Nov-2014 |
01:52 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
154,112 |
11-Oct-2014 |
07:08 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
284,160 |
11-Nov-2014 |
02:07 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
166,912 |
11-Oct-2014 |
08:10 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
73,728 |
26-Jul-2012 |
06:37 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
306,688 |
11-Nov-2014 |
01:34 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
180,736 |
11-Oct-2014 |
07:03 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
75,776 |
26-Jul-2012 |
05:59 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
310,272 |
18-Dec-2014 |
03:20 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
181,760 |
11-Oct-2014 |
07:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
71,680 |
26-Jul-2012 |
05:12 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
304,640 |
18-Dec-2014 |
02:20 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
181,760 |
11-Oct-2014 |
06:43 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
70,656 |
26-Jul-2012 |
04:48 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
299,008 |
18-Dec-2014 |
02:28 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
164,352 |
11-Oct-2014 |
06:53 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
78,848 |
26-Jul-2012 |
04:47 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
270,336 |
11-Nov-2014 |
01:42 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
161,792 |
11-Oct-2014 |
08:01 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
68,096 |
26-Jul-2012 |
05:08 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21317 |
270,336 |
18-Dec-2014 |
03:13 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
160,256 |
11-Oct-2014 |
07:34 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
63,488 |
26-Jul-2012 |
06:43 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
141,824 |
11-Nov-2014 |
01:33 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
87,040 |
11-Oct-2014 |
06:46 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
34,304 |
26-Jul-2012 |
06:38 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
145,408 |
11-Nov-2014 |
02:47 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
90,112 |
11-Oct-2014 |
08:11 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll.mui |
6.2.9200.21289 |
145,408 |
11-Nov-2014 |
01:56 |
Not applicable |
|
Msaudite.dll.mui |
6.2.9200.21269 |
90,112 |
11-Oct-2014 |
07:38 |
Not applicable |
|
Msobjs.dll.mui |
6.2.9200.16384 |
37,376 |
26-Jul-2012 |
06:34 |
Not applicable |
|
Adtschema.dll |
6.2.9200.17218 |
717,824 |
18-Dec-2014 |
04:15 |
x86 |
|
Msaudite.dll |
6.2.9200.17150 |
146,944 |
11-Oct-2014 |
05:05 |
x86 |
|
Msobjs.dll |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
02:47 |
x86 |
|
Adtschema.dll |
6.2.9200.21289 |
719,360 |
10-Nov-2014 |
03:40 |
x86 |
|
Msaudite.dll |
6.2.9200.21269 |
146,944 |
11-Oct-2014 |
04:35 |
x86 |
|
Msobjs.dll |
6.2.9200.16384 |
61,952 |
26-Jul-2012 |
02:47 |
x86 |
|
Credssp.dll |
6.2.9200.16891 |
17,408 |
12-Apr-2014 |
07:22 |
x86 |
|
Tspkg.dll |
6.2.9200.16891 |
76,800 |
12-Apr-2014 |
07:23 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
02-Jun-2012 |
14:33 |
Not applicable |
|
Credssp.dll |
6.2.9200.21012 |
17,408 |
12-Apr-2014 |
07:31 |
x86 |
|
Tspkg.dll |
6.2.9200.21012 |
76,800 |
12-Apr-2014 |
07:32 |
x86 |
|
Tspkg.mof |
Not applicable |
964 |
02-Jun-2012 |
14:33 |
Not applicable |
|
Shcore.dll |
6.2.9200.17218 |
452,608 |
18-Dec-2014 |
06:20 |
x86 |
|
Shcore.dll |
6.2.9200.21317 |
460,800 |
18-Dec-2014 |
00:38 |
x86 |
|
Usercpl.dll |
6.2.9200.17218 |
961,536 |
18-Dec-2014 |
06:20 |
x86 |
|
Usercpl.ptxml |
Not applicable |
789 |
11-Oct-2012 |
00:41 |
Not applicable |
|
Usercpl.dll |
6.2.9200.21012 |
961,536 |
12-Apr-2014 |
07:32 |
x86 |
|
Usercpl.ptxml |
Not applicable |
789 |
11-Oct-2012 |
00:42 |
Not applicable |
|
Windows6.1-KB3004375-v3-ia64.msu |
5CFC417B852EAED389B5FA19A32BD943BBD64B08 |
8B69356D65DF62CBA59B21071FBA03EE275A208E6CF64A197311D7F6194EE50F |
|
Windows6.1-KB3004375-v3-x86.msu |
822F779B87D3CD4EF4DE004C344ABCE202A8AAC6 |
D4A46833B1948919A1D1D2F506716544B6093BB5999EB8AA78ED5D5561FE85E0 |
|
Windows8-RT-KB3004375-v5-x86.msu |
97E05C5294FFA53888D4D0B08FEA701307A777ED |
FBA0B25F7EBF3B71A3D66D6D4925C844BC6F02839C3CFB3A8CBAFD6E831B58ED |










