Symptoms
Passive federation request fails when accessing an application, such as SharePoint, that uses AD FS and Forms Authentication after previously connecting to Microsoft Dynamics CRM with Claims Based Authentication
It fails with following error:
Encountered error during federation passive request.
Additional Data
Protocol Name:
Relying Party:
Exception details:
Microsoft.IdentityServer.RequestFailedException: MSIS7065: There are no registered protocol handlers on path /adfs/ls/ to process the incoming request.
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
Sign out scenario:
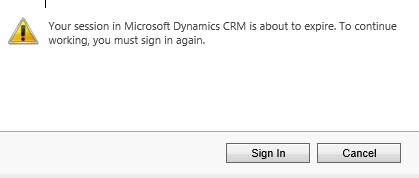
20 minutes before Token expiration below dialog is shown with options to Sign In or Cancel. Clicking Sign In doesn't redirect to ADFS Sign In page prompting for username and password. Instead, it presents a Signed Out ADFS page. Referece - Claims-based authentication and security token expiration.
Cause
The issue is caused by a duplicate MSISAuth cookie issued by Microsoft Dynamics CRM as a domain cookie with an AD FS namespace. This cookie name is not unique and when another application, such as SharePoint is accessed, it is presented with duplicate cookie. This causes authentication to fail.
The Signed Out scenario is caused by Sign Out cookie issued by Microsoft Dynamics CRM as a domain cookie, see below example. This cookie is domain cookie and when presented to ADFS, it's considered for the entire domain, like *.contoso.com/. This causes re-authentication flow to fail and ADFS presents Sign Out page.
Set-Cookie: MSISSignOut=; domain=contoso.com; path=/; secure; HttpOnly
Resolution
To resolve this issue, you will need to configure Microsoft Dynamics CRM with a subdomain value such as crm.domain.com. This will require a different wild card certificate such as *.crm.domain.com.
After performing these changes, you will need to re-configure Claims Based Authentication and IFD using the correct endpoints like shown below:
-
auth.<subdomain>.domain.com
-
dev.<subdomain>.domain.com
-
org.<subdomain>.domain.com
More Information
For additional details on configuring Claims Based Authentication and IFD for Microsoft Dynamics CRM, see the following link:
Configuring Claims-based Authentication for Microsoft Dynamics CRM Server










