Summary
A security vulnerability exists in certain Trusted Platform Module (TPM) chipsets. The vulnerability weakens key strength. To learn more about the vulnerability, go to ADV170012.
More Information
Overview
The following sections will help you identify and remedy problems in Active Directory (AD) domains and domain controllers that are affected by the vulnerability that is described in Microsoft Security Advisory ADV170012.
This mitigation process focuses on the following Active Directory public key scenario:
-
Domain-joined computer credential keys
For information about revoking and issuing new KDC certificates, see Mitigation Plan for Active Directory Certificate Services-based scenarios.
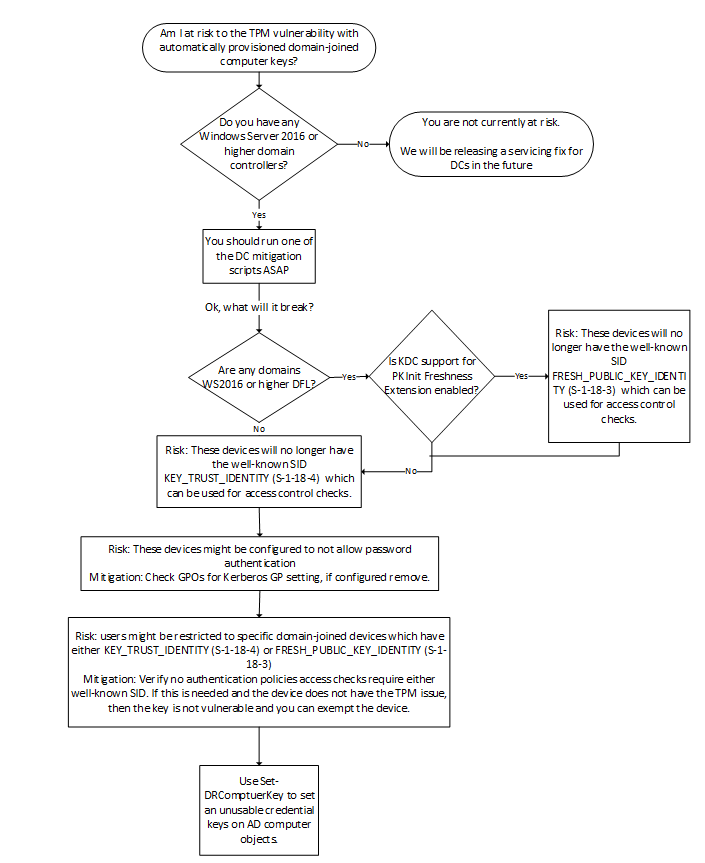
Determining domain-joined computer credential key risk workflow
Do you have Windows Server 2016 (or later) domain controllers?
Credential keys were introduced for Windows Server 2016 domain controllers. Domain controllers add the well-known SID KEY_TRUST_IDENTITY (S-1-18-4) when a credential key is used to authenticate. Earlier domain controllers didn't support credential keys, so the AD doesn't support credential key objects, and down-level domain controllers can't authenticate principals by using credential keys.
Previously, the altSecurityIdentities (frequently referred to as altSecID) attribute could be used to provide similar behavior. Provisioning altSsecID is not supported natively by Windows. Therefore, you would need a third-party solution that provides this behavior. If the key that is provisioned is vulnerable, the corresponding altSsecID would have to be updated in AD.
Are any domains Windows Server 2016 (or later) DFL?
Windows Server 2016 domain controllers support Public Key Cryptography for Initial Authentication in Kerberos (PKINIT) Freshness Extension [RFC 8070], although not by default. WhenSupport for PKInit Freshness Extension is enabled on domain controllers in Windows Server 2016 DFL or later domains, the domain controllers add the well-known SID FRESH_PUBLIC_KEY_IDENTITY (S-1-18-3) when the extension is successfully used. For more information, see Kerberos client and KDC support for RFC 8070 PKInit Freshness Extension.
Patching computers
Servicing Windows 10 computers that have the October 2017 security updates will remove the existing TPM credential key. Windows will only provision Credential Guard-protected keys to ensure Pass-the-Ticket protection for domain-joined device keys. Because many customers are adding Credential Guard well after domain-joining their computers, this change ensures that devices that have Credential Guard enabled can ensure that any TGTs issued by using the credential key are protected by Credential Guard.