Summary
A security vulnerability exists in certain Trusted Platform Module (TPM) chipsets. The vulnerability weakens key strength.
This article helps identify and remedy problems in BitLocker protected-devices that are affected by the vulnerability that is described in Microsoft Security Advisory ADV170012.
More Information
Overview
This document describes how to remedy the vulnerability impact in BitLocker TPM-based protectors.
The impact on other BitLocker protector methods has to be reviewed based on how the relevant secrets are protected. For example, if an external key to unlock BitLocker is protected to the TPM, refer to the advisory to analyze the impact. Remedying of these effects of the vulnerability is not in the scope of this document.
How to identify impact
BitLocker uses the TPM seal and unseal operations together with the storage root key to protect BitLocker secrets on the operating system volume. The vulnerability affects the seal and unseal operations on TPM 1.2, but it does not affect the operations on TPM 2.0.
When TPM-based protector is used to protect the operating system volume, the security of the BitLocker protection is affected only if the TPM firmware version is 1.2.
To identify affected TPMs and TPM versions, see "2. Determine devices in your organization that are affected” under "Recommended Actions" in Microsoft Security Advisory ADV170012.
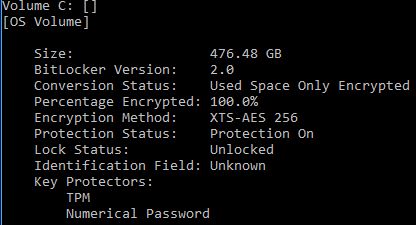
To check BitLocker status, run “manage-bde -status <OS volume letter:>” at a command prompt as an administrator of the computer.
Figure 1 Sample output of an operating system volume that is protected by both TPM protector and Recovery Password protector. (Device encryption is not affected by this TPM vulnerability.)
Remedy BitLocker vulnerability after firmware update
Follow these steps to remedy the vulnerability:
-
Suspend BitLocker protection: Run “manage-bde -protectors <OS volume letter:> –disable” as an administrator of the computer.
-
Clear the TPM. For instructions, see "6. Clear TPM” under Recommended Actions" in Microsoft Security Advisory ADV170012.
-
BitLocker protection automatically resumes after a restart for Windows 8 and later versions of Windows. For Windows 7, run “manage-bde -protectors <OS volume letter:> –enable” as an administrator of the computer to resume BitLocker protection.
The following page provides a full command-line reference for manage-bde.exe:
https://technet.microsoft.com/en-us/library/ff829849(v=ws.11).aspx