Scenario
Consider the following scenario:
-
You are running Exchange Server by using the Shared Permissions Model that is installed by default for Exchange Server.
-
Access Control Entries are put into the Active Directory forest. This gives Exchange Server an elevated level of directory permission.
Cause
Exchange Server is a directory services-enabled application. Therefore, it must be able to modify attributes that are related to Exchange Server-enabled objects. This includes the ability to modify Discretionary Access Control Lists (DACLs) in some instances. Because these objects can exist anywhere in the domain hierarchy, Exchange Server grants rights to servers that are running Exchange Server at the root of the domain. This is done to make sure that the rights are passed on to all applicable objects.
Exchange Server does not currently make use of the Inherit Only flag when DACL propagation is evaluated. This does not apply to the Active Directory Split Permissions model. In a split permissions configuration, Exchange Server applies a permissions model that does not grant servers the ability to create or modify security principals in the directory.
Status
This behavior is by design. It provides Exchange administrators the flexibility to manage attributes on Exchange Server objects that are consistent with their role as an Exchange administrator. Exchange administrators are expected to be able to create user accounts and mailboxes, and reassign mailbox-type objects as resource mailboxes or shared mailboxes if Exchange Server is running in the Shared Permissions Model.
Resolution
Microsoft has evaluated the rights that are granted to servers that are running Exchange Server and to Exchange administrators in the identified scenarios. Microsoft has determined that it is possible to make changes that lower the permissions that are granted within an Active Directory domain. The actual permission changes will vary depending on the version of Exchange Server that is used.
The procedure in this section returns all environments to a common, reduced directory permission profile.
To resolve this issue on Exchange Server 2013 or a later version, customers should install the following cumulative update, as appropriate for their environment:
-
Exchange Server 2019 – Cumulative Update 1
-
Exchange Server 2016 – Cumulative Update 12
-
Exchange Server 2013 – Cumulative Update 22
Environments in which Exchange Server 2013 or a later version is in use require the updated cumulative update package to manually execute /PrepareAD in any Active Directory forest in which Exchange Server is installed or in which the directory schema has been prepared to host servers that are running Exchange Server. Additionally, customers who employ multiple domains in a single forest will have to run /PrepareDomain in all domains in the forest to lower the permissions that are granted to Exchange Server and to Exchange administrators.
Note The /PrepareDomain operation automatically runs in the Active Directory domain in which /PrepareAD is run. However, it may not be able to update other domains in the forest. For this reason, a domain administrator should run /PrepareDomain in other domains in the forest. For more information about the /Prepare switches that are used by Exchange Server, see Prepare Active Directory and domains for Exchange Server.
The prepare operations in these updated cumulative updates make the following changes to the Active Directory environment.
Exchange Server 2016 and later versions
The AdminSDHolder object on the domain is updated to remove the "Allow" ACE that grants the "Exchange Trusted Subsystem" group the "Write DACL" right on the "Group" inherited object types.
Exchange Server 2013 and later versions
The "Allow" Access Control Entry (ACE) that grants the "Exchange Windows Permissions" group the "Write DACL" right to the "User" and "INetOrgPerson" inherited object types is updated to include the "Inherit Only" flag on the domain root object.
Exchange Server 2010
Customers who are running Exchange Server 2010 should apply the following manual updates to their environment by using the LDP tool.
-
Start the LDP tool (In the Run box, type ldp.exe, and then press Enter).
-
Connect to the domain namespace that you want to update. (On the File menu, click Connect.)
-
Bind to the domain namespace by using Domain Admin credentials. (On the File menu, click Bind.)
-
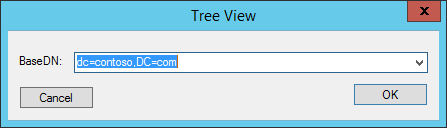
View the tree by using the base DN that corresponds to the root of the domain context to be updated. (On the View menu, click Tree.) For example:
-
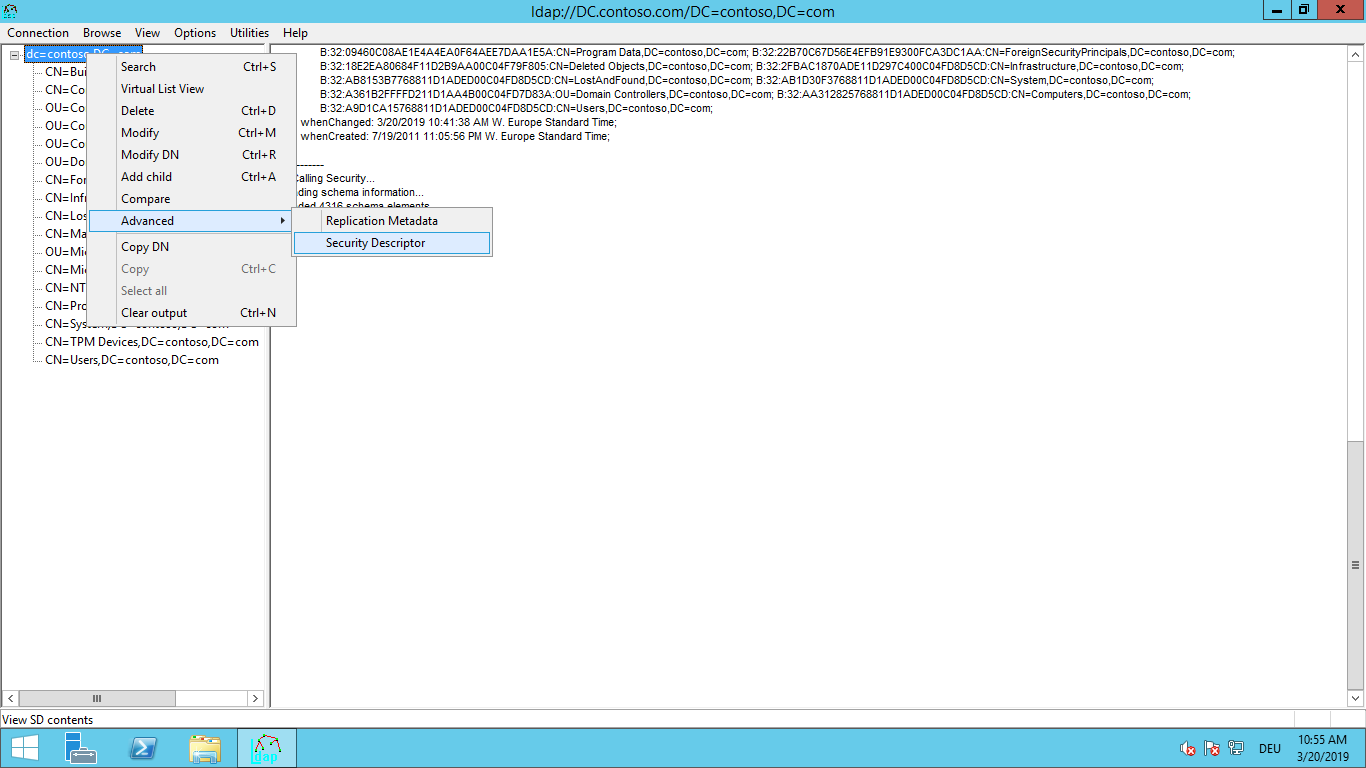
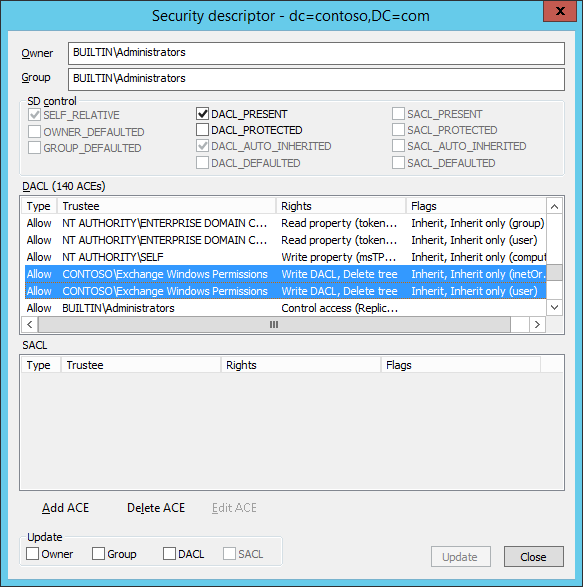
Open Domain Access Control Lists. (Right-Click domain, click Advanced, and then click Security Descriptor.)
-
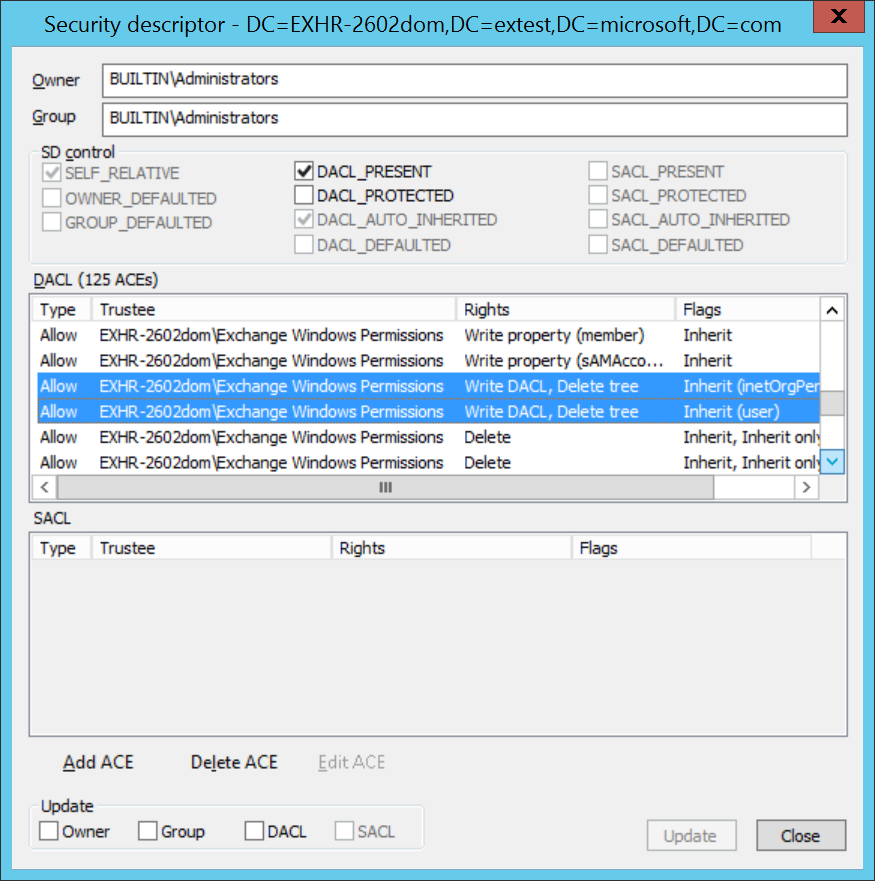
Find the two "Allow" ACEs that grant "Write DACL" right to the "Exchange Windows Permissions" group on the "User" and the "INetOrgPerson" inherited object types:
-
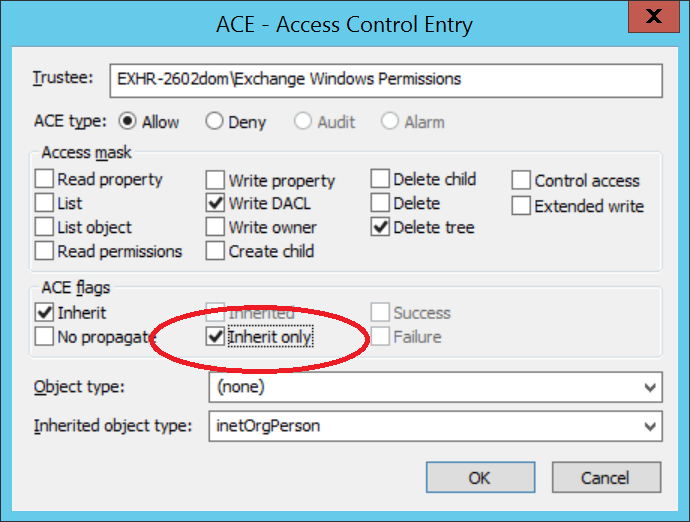
Edit each entry to add the "Inherit Only" flag. To do this, double-click the object, select the flag, and then click OK.
-
Verify that the operation is successful on each ACE. Then, click Update.