Original publish date: August 13, 2024
KB ID: 5042562
Support for Windows 10 has ended on October 14, 2025
After October 14, 2025, Microsoft will no longer provide free software updates from Windows Update, technical assistance, or security fixes for Windows 10. Your PC will still work, but we recommend moving to Windows 11.
Important note about the SkuSiPolicy.p7b policy
For instructions to apply the updated policy, see the Deploying a Microsoft-signed revocation policy (SkuSiPolicy.p7b) section.
In this article
-
Changes made to this article
Summary
Microsoft was made aware of a vulnerability in Windows that allows an attacker with administrator privileges to replace updated Windows system files that have older versions, opening the door for an attacker to reintroduce vulnerabilities to Virtualization-based security (VBS). Rollback of these binaries might allow an attacker to circumvent VBS security features and exfiltrate data that is protected by VBS. This issue is described in CVE-2024-21302 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability.
To resolve this issue, we will revoke vulnerable VBS system files that are not updated. Because of the large number of VBS-related files that must be blocked, we use an alternative approach to block file versions that are not updated.
Scope of Impact
All Windows devices that support VBS are affected by this issue. This includes on-premises physical devices and virtual machines (VMs). VBS is supported on Windows 10 and later Windows versions, and Windows Server 2016 and later Windows Server versions.
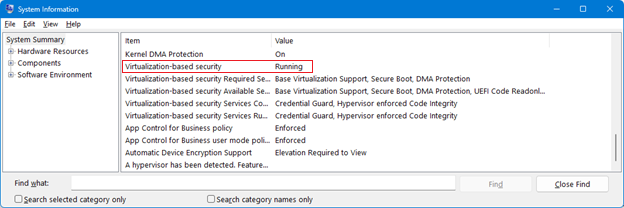
The VBS state can be checked through the Microsoft System Information tool (Msinfo32.exe). This tool collects information about your device. After starting Msinfo32.exe, scroll down to the Virtualization-based security row. If the value of this row is Running, VBS is enabled and running.
The VBS state can also be checked with Windows PowerShell by using the Win32_DeviceGuard WMI class. To query the VBS state from PowerShell, open an elevated Windows PowerShell session and then run the following command:
Get-CimInstance -ClassName Win32_DeviceGuard -Namespace root\Microsoft\Windows\DeviceGuard
After running the above PowerShell command, the VBS state status should be one of the following.
|
Field name |
Status |
|
VirtualizationBasedSecurityStatus |
|
Available mitigations
For all supported versions of Windows 10, version 1507 and later Windows versions, and Windows Server 2016 and later Windows Server versions, administrators can deploy a Microsoft-signed revocation policy (SkuSiPolicy.p7b). This will block vulnerable versions of VBS system files that are not updated from being loaded by the operating system.
When the SkuSiPolicy.p7b is applied to a Windows device, the policy will also be locked to the device by adding a variable to the UEFI firmware. During startup, the policy loads and Windows blocks the loading of binaries that violate the policy. If the UEFI lock is applied and the policy is removed or replaced with an older version, the Windows boot manager will not start, and the device will not start. This boot failure will not show an error and the system will proceed to the next available boot option which might result in a boot loop.
An additional Microsoft-signed CI policy which is enabled by default and requires no additional deployment steps has been added which is not bound to UEFI. This signed CI policy will be loaded during boot and the enforcement of this policy will prevent rollback of VBS system files during that boot session. Unlike the SkuSiPolicy.p7b, a device can continue to boot if the update is un-installed. This policy is included in all supported versions of Windows 10, version 1507 and later. The SkuSkiPolicy.p7b can still be applied by administrators to provide additional protection for rollback across boot sessions.
Windows Measured Boot logs used to attest the boot health of the PC include information about the policy version being loaded during the boot process. These logs are securely maintained by the TPM during boot, and the Microsoft attestation services parse these logs to verify that the correct policy versions are being loaded. The attestation services enforce rules that ensure a specific policy version or higher is loaded; otherwise, the system will not be attested as healthy.
For the policy mitigation to work, the policy must be updated using the Windows servicing update since the components of Windows and the policy must be from the same release. If the policy mitigation is copied to the device, the device might not start if the wrong version of the mitigation is applied, or the mitigation may not work as expected. Additionally, mitigations described in KB5025885 should be applied to your device.
On Windows 11, version 24H2, Windows Server 2022, and Windows Server 23H2, Dynamic Root of Trust for Measurement (DRTM) adds an additional mitigation for the rollback vulnerability. This mitigation is enabled by default. On these systems, the VBS-protected encryption keys are bound to the default-enabled boot session VBS CI policy and will only unseal if the matching CI policy version is being enforced. To enable user-initiated rollbacks, a grace period has been added to enable safe rollback of 1 version of Windows update package without losing the ability to unseal the VSM master key. However, the user-initiated rollback is only possible if the SkuSiPolicy.p7b is not applied. The VBS CI policy enforces that all boot binaries have not been rolled back to revoked versions. This means that if an attacker with administrator privileges rolls back vulnerable boot binaries, the system will not start. If the CI policy and binaries are both rolled back to an earlier version, the VSM-protected data will not be unsealed.
Understanding mitigation risks
You need to be aware of potential risks before applying the Microsoft-signed revocation policy. Please review these risks and make any necessary updates to recovery media before applying the mitigation.
Note These risks are only applicable to the SkuSiPolicy.p7b policy and not applicable to default enabled protections.
-
UEFI Lock and Uninstalling updates. After applying the UEFI lock with the Microsoft-signed revocation policy on a device, the device cannot be reverted (by uninstalling Windows updates, by using a restore point, or by other means) if you continue to apply Secure Boot. Even reformatting the disk will not remove the UEFI lock of the mitigation if it has already been applied. This means that if you attempt to revert the Windows OS to an earlier state that does not have the applied mitigation, the device will not start, no error message will be displayed, and UEFI will proceed to the next available boot option. This might result in a boot loop. You must disable Secure Boot to remove the UEFI lock. Please be aware of all possible implications and test thoroughly before you apply the revocations that are outlined in this article to your device.
-
External Boot Media. After the UEFI lock mitigations have been applied to a device, external boot media must be updated with the latest Windows update installed on the device. If external boot media is not updated to the same Windows update version, the device might not boot from that media. See the instructions in the Updating external boot media section before applying the mitigations.
-
Windows Recovery Environment. The Windows Recovery Environment (WinRE) on the device must be updated with the latest Windows Safe OS Dynamic Update released on July 8, 2025, on the device before the SkuSipolicy.p7b is applied to the device. Omitting this step might prevent WinRE from running the Reset PC feature. For more information, see Add an update package to Windows RE.
-
Pre-boot Execution Environment (PXE) boot. If the mitigation is deployed to a device and you attempt to use PXE boot, the device will not start unless the latest Windows update is also applied to the PXE server boot image. We do not recommend deploying mitigations to network boot sources unless the PXE Boot server has been updated to the latest Windows update released on or after January 2025, including the PXE boot manager.
Mitigation deployment guidelines
To address the issues described in this article, you can deploy a Microsoft-signed revocation policy (SkuSiPolicy.p7b). This mitigation is only supported on Windows 10, version 1507 and later Windows versions, and Windows Server 2016.
Note If you use BitLocker, make sure that your BitLocker recovery key has been backed up. You can run the following command from an Administrator command prompt and take note of the 48-digit numerical password:
manage-bde -protectors -get %systemdrive%
Deploying a Microsoft-signed revocation policy (SkuSiPolicy.p7b)
The Microsoft-signed revocation policy is included as part of the latest Windows update. This policy should only be applied to devices by installing the latest available Windows update and then follow these steps:
Note If updates are missing, the device may not start with the mitigation applied or the mitigation may not work as expected. Make sure to update your bootable Windows media with the latest available Windows update before deploying the policy. For details on how to update bootable media, see the Updating external boot media section.
-
Ensure that the latest Windows update released on or after January 2025, is installed.
-
For Windows 11, version 22H2 and 23H2, install the July 22, 2025 (KB5062663) or a later update before following these steps.
-
For Windows 10, version 21H2, install the Windows update released in August 2025 or a later update before following these steps.
-
-
Run the following commands in an elevated Windows PowerShell prompt:
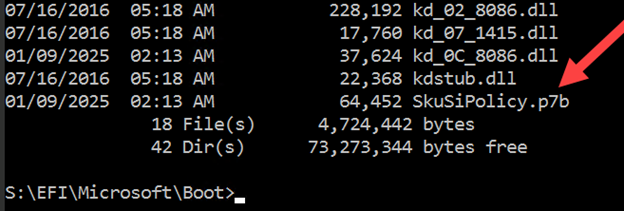
$PolicyBinary = $env:windir+"\System32\SecureBootUpdates\SkuSiPolicy.p7b" $MountPoint = 's:' $EFIDestinationFolder = "$MountPoint\EFI\Microsoft\Boot" mountvol $MountPoint /S if (-Not (Test-Path $EFIDestinationFolder)) { New-Item -Path $EFIDestinationFolder -Type Directory -Force } Copy-Item -Path $PolicyBinary -Destination $EFIDestinationFolder -Force mountvol $MountPoint /D
-
Restart your device.
-
Confirm the policy is loaded in the Event Viewer by using the information in the Windows Event logs section.
Notes
-
You should not remove the SkuSiPolicy.p7b revocation (policy) file after it is deployed. Your device might no longer be able to start if the file is removed.
-
If your device does not start, see the Recovery procedure section.
Updating external boot media
To use external boot media with a device that has a Microsoft-signed revocation policy applied, the external boot media must be updated with the latest Windows update including the Boot manager. If the media does not include the latest Windows update, the media will not start.
Important We recommend that you Create a recovery drive before proceeding. This media can be used to reinstall a device in case there is a major issue.
Use the following steps to update the external boot media:
-
Go to a device where the latest Windows updates have been installed.
-
Mount the external boot media as a drive letter. For example, mount a thumb drive as D:.
-
Click Start, type Create a Recovery Drive in the Search box, and then click Create a recovery drive control panel. Follow the instructions to create a recovery drive by using the mounted thumb drive.
-
Safely remove the mounted thumb drive.
If you manage installable media in your environment by using the Update Windows installation media with Dynamic Update guidance, follow these steps:
-
Go to a device where the latest Windows updates have been installed.
-
Follow the steps in Update Windows installation media with Dynamic Update to create media that has the latest Windows updates installed.
Windows Event logs
Windows logs events when code integrity policies, including SkuSiPolicy.p7b, are loaded and when a file is blocked from loading because of policy enforcement. You can use these events to verify that the mitigation has been applied.
Code integrity logs are available in the Windows Event Viewer under Application and Services logs > Microsoft > Windows > CodeIntegrity > Operational > Application and Services logs > Services logs > Microsoft > Windows > AppLocker > MSI and Script.
For more information on code integrity events, see the Windows Defender Application Control operational guide.
Policy activation events
Policy activation events are available in the Windows Event Viewer under Application and Services logs > Microsoft > Windows > CodeIntegrity > Operational.
-
PolicyNameBuffer – Microsoft Windows SKU SI Policy
-
PolicyGUID – {976d12c8-cb9f-4730-be52-54600843238e}
-
PolicyHash – 107E8FDD187C34CF8B8EA46A4EE99F0DB60F491650DC989DB71B4825DC73169D
If you have applied the audit policy or the mitigation to your device and CodeIntegrity Event 3099 for the applied policy is not present, the policy is not being enforced. Please consult the deployment instructions to verify the policy was installed correctly.
Note The Code Integrity event 3099 is not supported on versions of Windows 10 Enterprise 2016, Windows Server 2016, and Windows 10 Enterprise 2015 LTSB. To verify that the policy has been applied (audit or revocation policy), you must mount the EFI System Partition using the mountvol.exe command and look to see that the policy has been applied to the EFI partition. Be sure to unmount the EFI System Partition after verification.
SkuSiPolicy.p7b - Revocation Policy
Audit and block events
Code integrity audit and block events are available in the Windows Event Viewer under Application and Services logs > Microsoft > Windows > CodeIntegrity > Operational > Application and Services logs > Microsoft > Windows > AppLocker > MSI and Script.
The former logging location includes events about the control of executables, dlls, and drivers. The latter logging location includes events about the control of MSI installers, scripts, and COM objects.
CodeIntegrity Event 3077 in the "CodeIntegrity – Operational" log indicates that an executable, .dll, or driver has been blocked from loading. This event includes information about the blocked file and about the enforced policy. For files blocked by the mitigation, the policy information in CodeIntegrity Event 3077 will match the policy information of SkuSiPolicy.p7b from CodeIntegrity Event 3099. CodeIntegrity Event 3077 will not be present if there are not any executable, .dll, or drivers in violation of code integrity policy on your device.
For other code integrity audit and block events, see Understanding Application Control events.
Policy Removal and Recovery Procedure
If something goes wrong after applying the mitigation, you can use the following steps to remove the mitigation:
-
Suspend BitLocker if it is enabled. Run the following command from an elevated Command Prompt window:
Manager-bde -protectors -disable c: -rebootcount 3
-
Turn off Secure Boot from the UEFI BIOS menu. The procedure for turning off Secure Boot differs between device manufacturers and models. For help locating where to turn off Secure Boot, consult with documentation from your device manufacturer. More details can be found in Disabling Secure Boot.
-
Remove the SkuSiPolicy.p7b policy.
-
Start Windows normally and then sign in. The SkuSiPolicy.p7b policy must be removed from the following location:
-
<EFI System Partition>\Microsoft\Boot\SkuSiPolicy.p7b
-
-
Run the following commands from an elevated Windows PowerShell session to clean up policy from those locations:
$PolicyBinary = $env:windir+"\System32\SecureBootUpdates\SkuSiPolicy.p7b" $MountPoint = 's:' $EFIPolicyPath = "$MountPoint\EFI\Microsoft\Boot\SkuSiPolicy.p7b" $EFIDestinationFolder="$MountPoint\EFI\Microsoft\Boot" mountvol $MountPoint /S if (-Not (Test-Path $EFIDestinationFolder)) { New-Item -Path $EFIDestinationFolder -Type Directory -Force } if (Test-Path $EFIPolicyPath ) {Remove-Item -Path $EFIPolicyPath -Force } mountvol $MountPoint /D
-
-
Turn on Secure Boot from BIOS. Consult with the documentation from your device manufacturer for locating where to turn on Secure Boot. If you turned off Secure Boot in Step 1 and your drive is protected by BitLocker, suspend BitLocker protection and then turn on Secure Boot from your UEFI BIOS menu.
-
Turn on BitLocker. Run the following command from an elevated Command Prompt window:
Manager-bde -protectors -enable c:
-
Restart your device.
|
Change date |
Description |
|
December 17, 2025 |
|
|
July 22, 2025 |
|
|
July 10, 2025 |
|
|
April 8, 2025 |
|
|
February 24, 2025 |
|
|
February 11, 2025 |
|
|
January 14, 2025 |
|
|
November 12, 2024 |
|