|
Change date |
Change description |
|---|---|
|
March 10, 2024 |
Revised the Monthly timeline adding more hardening related content and removed the February 2024 entry from the timeline as it is not hardening related. |
Introduction
Hardening is a key element of our ongoing security strategy to help keep your estate protected while you focus on your job. Increasingly creative cyberthreats target weaknesses anywhere possible, from the chip to the cloud. Have you seen our publications on hardening on the Windows message center? Some of those recently enforced include DCOM authentication hardening and Netjoin: domain join hardening. Let's review vulnerable areas that are undergoing hardening in the upcoming months.
Note: This article will be updated over time to provide the latest information about hardening changes and timelines. Last updated: March 10, 2024.
Hardening changes at a glance
Review the visual timeline to focus on the specific changes that are of interest to you. Find the details for each phase below.
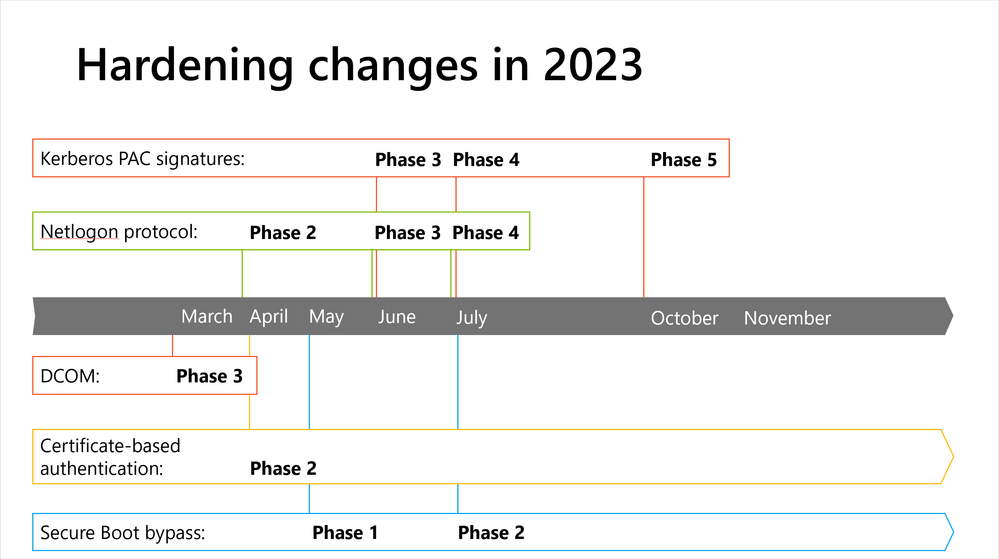
Figure 1: A visual timeline of the hardening changes taking place in 2023.
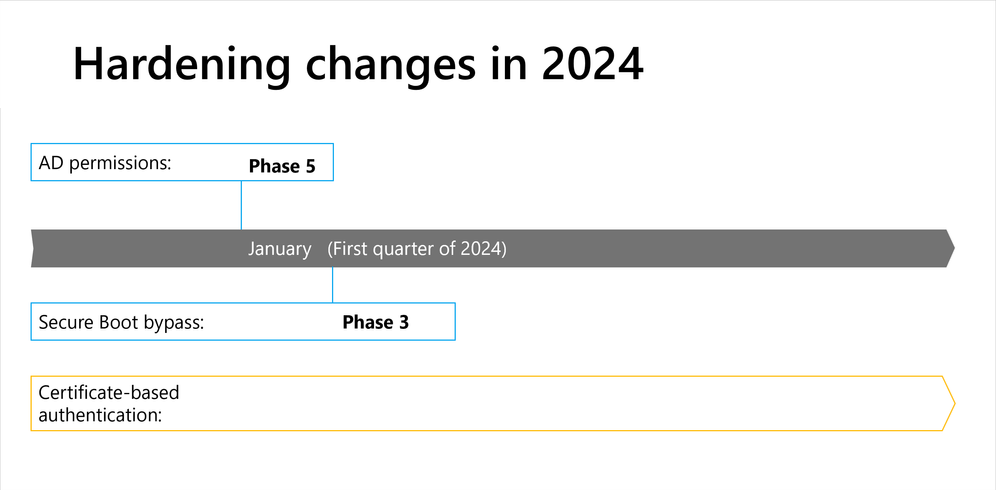
Figure 2: A visual timeline of the hardening changes taking place in 2024.
Hardening changes by month
Consult the details for all upcoming hardening changes by month to help you plan for each phase and final enforcement.
-
Secure Boot bypass protections KB5025885 | Phase 1
Initial Deployment phase. Windows Updates released on or after May 9, 2023 address vulnerabilities discussed in CVE-2023-24932, changes to Windows boot components, and two revocation files which can be manually applied (a Code Integrity policy and an updated Secure Boot disallow list (DBX)).
-
Netlogon protocol changes KB5021130 | Phase 3
Enforcement by default. RequireSeal subkey will be moved to Enforcement mode unless you explicitly configure it to be under Compatibility mode. -
Kerberos PAC Signatures KB5020805 | Phase 3
Third Deployment phase. Removes the ability to disable PAC signature addition by setting the KrbtgtFullPacSignature subkey to a value of 0.
-
Netlogon protocol changes KB5021130 | Phase 4
Final enforcement. The Windows updates released on July 11, 2023 will remove the ability to set value 1 to the RequireSeal registry subkey. This enables the Enforcement phase of CVE-2022-38023. -
Kerberos PAC Signatures KB5020805 | Phase 4
Initial Enforcement mode. Removes the ability to set value 1 for the KrbtgtFullPacSignature subkey, and moves to Enforcement mode as default (KrbtgtFullPacSignature = 3), which you can override with an explicit Audit setting. -
Secure Boot bypass protections KB5025885 | Phase 2
Second Deployment phase. Updates for Windows released on or after July 11, 2023 include automated deployment of the revocation files, new Event Log events to report whether revocation deployment was successful, and SafeOS Dynamic Update package for WinRE.
-
Kerberos PAC Signatures KB5020805 | Phase 5
Full Enforcement phase. Removes support for the registry subkey KrbtgtFullPacSignature, removes support for Audit mode, and all service tickets without the new PAC signatures will be denied authentication.
-
Active Directory (AD) permissions updates KB5008383 | Phase 5
Final deployment phase. The final deployment phase can begin once you have completed the steps listed in the "Take Action" section of KB5008383. To move to Enforcement mode, follow the instructions in the "Deployment Guidance" section to set the 28th and 29th bits on the dSHeuristics attribute. Then monitor for events 3044-3046. They report when Enforcement mode has blocked an LDAP Add or Modify operation that might have previously been allowed in Audit mode.
-
Secure Boot bypass protections KB5025885 | Phase 3
Third Deployment phase. This phase will add additional boot manager mitigations. This phase will start no sooner than April 9, 2024.
-
Secure Boot bypass protections KB5025885 | Phase 3
Mandatory Enforcement phase. The revocations (Code Integrity Boot policy and Secure Boot disallow list) will be programmatically enforced after installing updates for Windows to all affected systems with no option to be disabled.
-
Certificate-based authentication KB5014754 | Phase 3
Full Enforcement mode. If a certificate cannot be strongly mapped, authentication will be denied.
Get the latest news
Please bookmark the Windows message center to easily find the latest updates and reminders. And if you are an IT admin with access to the Microsoft 365 admin center, set up Email preferences on the Microsoft 365 admin center to receive important notifications and updates.










