Summary
As a follow-up to the CrowdStrike Falcon agent issue impacting Windows clients and servers, we have released an updated recovery tool with two repair options to help IT administrators expedite the repair process. The tool automates the manual steps in KB5042421 (client) and KB5042426 (server). Download the signed Microsoft Recovery Tool from the Microsoft Download Center. You can use the tool to recover Windows clients, servers, and Hyper-V virtual machines (VM).
There are two repair options:
-
Recover from Windows PE: this option uses boot media that automates the device repair.
-
Recover from safe mode: this option uses boot media for affected devices to boot into safe mode. An administrator can then sign in using an account with local administrative privileges and run the remediation steps.
Determine which option to use
This option to recover from Windows PE quickly and directly recovers systems and doesn't require local administrative privileges. If the device uses BitLocker, you may need to manually enter the BitLocker recovery key before you can repair an affected system.
If you use a non-Microsoft disk encryption solution, refer to guidance from that vendor. They should provide options to recover the drive so that you can run the remediation script from Windows PE.
This option to recover from safe mode may enable recovery on BitLocker-enabled devices without requiring the entry of BitLocker recovery keys. You need access to an account with local administrator rights on the device.
Use this option for devices in the following situations:
-
It uses TPM-only protectors.
-
The disk isn't encrypted.
-
The BitLocker recovery key is unknown.
If the device uses TPM+PIN BitLocker protectors, the user will either need to enter the PIN or you need to use the BitLocker recovery key.
If BitLocker isn't enabled, then the user only needs to sign in with an account with local administrator rights.
If you use a non-Microsoft disk encryption solution, refer to guidance from that vendor. They should provide options to recover the drive so that you can run the remediation script from safe mode.
Additional considerations
Although the USB option is preferred, some devices may not support USB connections. For these situations, see the section on how to Use Preboot Execution Environment (PXE) for recovery.
If the device can't connect to a PXE network, and USB isn't an option, try the manual steps in the following articles:
Otherwise, reimaging the device might be a solution.
With any recovery option, first test it on multiple devices before you use it broadly in your environment.
Create the boot media
Prerequisites to create the boot media
-
A Windows 64-bit client with at least 8 GB of free space on which you can run the tool to create the bootable USB drive.
-
Administrative privileges on the Windows client from prerequisite #1.
-
A USB drive with a minimum size of 1 GB and no larger than 32 GB. The tool deletes all existing data on this drive and automatically formats it to FAT32.
Instructions to create the boot media
To create recovery media, from the 64-bit Windows client in prerequisite #1, use the following steps:
-
Download the signed Microsoft Recovery Tool from the Microsoft Download Center.
-
Extract the PowerShell script from the downloaded file.
-
Open Windows PowerShell as an administrator and run the following script: MsftRecoveryToolForCS.ps1
-
The tool downloads and installs the Windows Assessment and Deployment Kit (Windows ADK). This process might take several minutes to complete.
-
Choose one of the two options for recovering affected devices: Windows PE or safe mode.
-
Optionally select a directory that contains driver files to import into the recovery image. We recommend you select N to skip this step.
-
The tool imports any SYS and INI files recursively under the specified directory.
-
Certain devices, such as Surface devices, might need additional drivers for keyboard input.
-
-
Select the option to either generate an ISO file or USB drive.
-
If you choose the USB option:
-
Insert the USB drive when prompted and provide the drive letter.
-
Once the tool completes creating the USB drive, remove it from the Windows client.
-
Instructions to use the recovery option
If you created media in the previous steps for Windows PE, use these instructions on affected devices.
Prerequisites to use the boot media for Windows PE recovery
-
You may need the BitLocker recovery key for each BitLocker-enabled and affected device.
-
If the affected device uses TPM+PIN protectors, and you don't know the PIN for the device, then you may need the recovery key.
-
Instructions to use the boot media for Windows PE recovery
-
Insert the USB key into an affected device.
-
Restart the device.
-
During restart, press F12 to access the BIOS boot menu.
Note: Some devices may use a different key combination to access the BIOS boot menu. Follow manufacturer-specific instructions for the device.
-
From the BIOS boot menu, choose Boot from USB and continue. The tool runs.
-
If BitLocker is enabled, the user will be prompted for the BitLocker recovery key. Include the dashes (-) when you enter the BitLocker recovery key. For more information on recovery key options, see Where to look for your BitLocker recovery key.
Note: For non-Microsoft device encryption solutions, follow any steps provided by the vendor to gain access to the drive.
-
If BitLocker isn't enabled on the device, you may still be prompted for the BitLocker recovery key. Press Enter to skip and continue.
-
-
The tool runs the remediation steps as recommended by CrowdStrike.
-
Once complete, remove the USB drive and restart the device normally.
If you created media in the previous steps for safe mode, use these instructions on affected devices.
Prerequisites to use the boot media for safe mode recovery
-
Access to the local Administrator account.
-
If the affected device uses BitLocker TPM+PIN protectors, and you don't know the PIN for the device, then you may need the BitLocker recovery key.
Instructions to use the boot media for safe mode recovery
-
Insert the USB key into an affected device.
-
Restart the device.
-
During restart, press F12 to access the BIOS boot menu.
Note: Some devices may use a different key combination to access the BIOS boot menu. Follow manufacturer-specific instructions for the device.
-
From the BIOS boot menu, choose Boot from USB and continue.
-
The tool runs and the following message appears:This tool will configure this machine to boot in safe mode. WARNING: In some cases you may need to enter a BitLocker recovery key after running.
-
Press any key to continue. The following message appears:Your PC is configured to boot to Safe Mode now.
-
Press any key to continue. The device restarts into safe mode.
-
Run repair.cmd from the root of the media drive. The script runs the remediation steps as recommended by CrowdStrike.
-
The following message appears:This tool will remove impacted files and restore normal boot configuration. WARNING: You may need BitLocker recovery key in some cases. WARNING: This script must be run in an elevated command prompt.
-
Press any key to continue. The script runs and restores the normal boot mode.
-
Once the tool completes successfully, the following message appears:Success. System will now reboot.
-
Press any key to continue. The device restarts normally.
Use recovery media on Hyper-V virtual machines
You can use the recovery media to remediate affected Hyper-V virtual machines (VM). When you create the boot media, select the option to generate an ISO file.
Note: For non-Hyper-V VMs, follow instructions provided by your hypervisor vendor to use the recovery media.
Instructions to recovery Hyper-V virtual machines
-
On an affected VM, add a DVD Drive under Hyper-V settings > SCSI Controller.
-
Browse to the recovery ISO and add it as an Image file under Hyper-V Settings > SCSI Controller > DVD Drive.
-
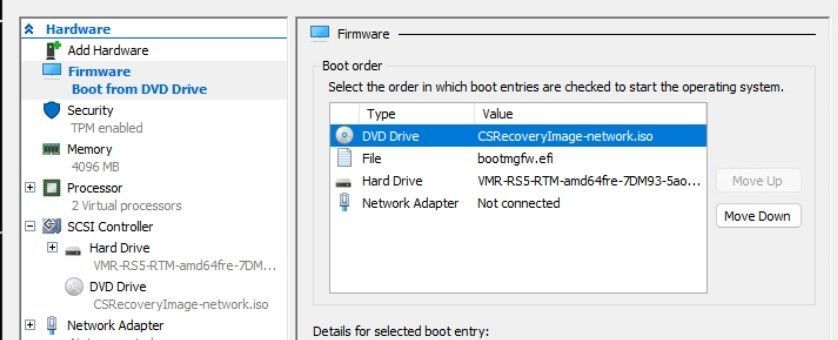
Note the current Boot order so that you can manually restore it later. The following image is an example of a boot order, which may be different than the configuration of your VM.
-
Change the Boot order to move up the DVD Drive as the first boot entry.
-
Start the VM and press any key to continue booting to the ISO image.
-
Depending on how you created the recovery media, follow the additional steps to use the Windows PE or safe mode recovery options.
-
Set the boot order back to the original boot settings from the VM’s Hyper-V settings.
-
Restart the VM normally.
Use PXE for recovery
For most customers, the other recovery options will help restore your devices. However, if devices are unable to use the option to recover from USB, for example, because of security policies or port availability, IT admins can use PXE to remediate.
To use this solution, you can use the Windows Imaging Format (WIM) image that the Microsoft recovery tool creates in an existing PXE environment. The affected devices need to be on the same network subnet as the existing PXE server.
Alternatively, you can use the PXE server approach outlined below. This option works best when you can easily move the PXE server from subnet to subnet for remediation purposes.
Prerequisites for PXE recovery
-
A 64-bit Windows device that hosts the boot image. This device is referred to as the “PXE server.”
-
The PXE server can run on any supported Windows client 64-bit OS.
-
The PXE server should have internet access to download the Microsoft PXE tool from the Microsoft Download Center. You can also copy it to the PXE server from another system on your network.
-
The PXE server should have inbound firewall rules created for UDP ports 67, 68, 69, 547, and 4011. The downloaded PXE tool (MSFTPXEToolForCS.exe) updates the Windows Firewall settings on the PXE server. If the PXE server uses a non-Microsoft firewall solution, create rules following their recommendations.
Note: This script doesn't clean up the firewall rules. You should remove these firewall rules after remediation is complete. To remove these rules from the Windows Firewall, open Windows PowerShell as an administrator and run the following command: MSFTPXEInitToolForCS.ps1 clean
-
Administrative privileges to run the PXE tool.
-
The PXE server requires the Microsoft Visual C++ Redistributable. Download and install the latest version.
-
-
The affected Windows devices should be on the same subnet as the PXE server. They should be hard-wired instead of using a Wi-Fi network.
Configure the PXE server
-
Download the Microsoft PXE tool from the Microsoft Download Center. Extract the contents of the zip archive to any directory. It contains all of the necessary files.
-
Open Windows PowerShell as an administrator. Change to the directory where you extracted the files and run the following command: MSFTPXEInitToolForCS.ps1
-
The script scans for the Windows ADK and Windows PE Add-On installation on the PXE server. If they're not installed, the script installs them. To proceed with installation, review and accept the license terms.
-
The script generates the remediation scripts and creates a valid boot image.
-
If required, accept the prompt and provide a path containing the driver files. Driver files may be required for keyboard or mass storage devices. Generally, you won't need to add drivers. If you don't need any additional driver files, select N.
-
You can configure the PXE server to deliver a default remediation image or a safe mode image. You'll see the following prompts:1. Boot to WinPE to remediate the issue. It requires entering BitLocker recovery key if system disk is BitLocker encrypted. 2. Boot to WinPE configure safe mode and run repair command after entering safe mode. This option is less likely to require BitLocker recovery key if system disk is BitLocker encrypted.
-
The script generates the required distribution files and provides the path where it copies the PXE server tool.
-
-
Double-check the prerequisites for PXE recovery, especially the Microsoft Visual C++ Redistributable.
-
From the PowerShell console as an administrator, change to the directory where the PXE server tool is copied, and run the following command to launch the listener process: .\MSFTPXEToolForCS.exe
-
You won't see additional responses as the PXE server handles connections. Don't close this window as that will stop the PXE server.
-
You can monitor the PXE server progress in the MSFTPXEToolForCS.log file in the same directory.
Note: If you want to run multiple PXE servers for different subnets, copy the directory with the PXE server tool, and rerun steps 3 & 4.
-
Additional information about PXE
Use PXE to recover an affected device
The affected device must be on the same subnet as PXE server. If the devices are in different subnets, configure IP helpers in your network environment to enable the discovery of the PXE server.
If the affected device isn't configured for PXE boot, follow these steps:
-
On the affected device, access the BIOS\UEFI menu.
-
This action is different across different models and manufacturers. Refer to documentation provided by the original equipment manufacturer for the specific make and model of the device.
-
Common options for accessing the BIOS\UEFI involve pressing a key like F2, F12, DEL, or ESC during the startup sequence.
-
-
Ensure Network boot is enabled on the device. For additional guidance, refer to documentation from the device manufacturer.
-
Configure the network boot option as the first boot priority.
-
Save the new settings. Restart the device for the settings to apply and boot from PXE.
When you PXE boot the affected device, the behavior will depend upon whether you chose Windows PE or safe mode recovery media for the PXE server.
For more information on these options, see the additional steps to use the Windows PE or safe mode recovery options.
-
For the Windows PE recovery option, the user is prompted to boot to Windows PE and the remediation script runs automatically.
-
For the safe mode recovery option, the device boots to safe mode. The user needs to sign in with the local Administrator account and manually run the script.
-
In safe mode and signed in as the local Administrator, open Windows PowerShell as an administrator.
-
Run the following commands:del %SystemRoot%\System32\drivers\CrowdStrike\C-00000291*.sys bcdedit /deletevalue {current} safeboot shutdown -r -t 00
-
Once complete, restart the device normally by responding to the prompt on the screen. Access the BIOS\UEFI menu and update the boot order to remove PXE boot.
Contact CrowdStrike
If after following the above steps, if you still experience issues logging into your device, please reach out to CrowdStrike for additional assistance.
Additional information
For more information on the issue impacting Windows clients and servers running the CrowdStrike Falcon agent, see the following resources:
-
A wide variety of Windows information is available from Windows release health (aka.ms/WRH).
-
Detailed recovery steps are available in the following articles:
-
Windows 365 Cloud PC customers can attempt to restore their Cloud PC to a known good state prior to the release of the update (July 19, 2024). For more information, see one of the following articles:
-
For Windows VMs running on Microsoft Azure, follow the mitigation steps in Azure status.
-
Additional details from CrowdStrike are available from the CrowdStrike remediation and guidance hub: Falcon content update for Windows hosts.
-
The Microsoft Intune Customer Success blog post on the recovery tool has comments from other IT administrators that may be helpful.
References
The third-party products that this article discusses are manufactured by companies that are independent of Microsoft. We make no warranty, implied or otherwise, about the performance or reliability of these products.
We provide third-party contact information to help you find technical support. This contact information may change without notice. We do not guarantee the accuracy of this third-party contact information.