Summary
Starting in the Microsoft Exchange Server March 2024 security update, Exchange Server no longer uses “Oracle Outside In Technology” (also known as OutsideInModule or OIT) to perform text extraction workloads when it processes email messages in transport if those messages contain attachments.
This change is made because of security vulnerabilities that were found in this third-party package. For more information, see this MSRC security advisory.
Text extraction is used when you process Exchange Transport Rules (ETR) or Data Loss Prevention (DLP) rules that have attachment scanning conditions. For more information, see Use transport rules to inspect message attachments.
Exchange Server on-premises can scan used attachment types by using the iFiltering platform libraries. However, three file types cannot be processed without using OIT. After you install the March 2024 security update, text extraction workloads can no longer be performed for the following file types:
-
Jpeg
-
Tiff
-
AutoCAD
Notice that before the March 2024 security update is installed, only the metadata text that’s associated with Jpeg(.jpg and .jpeg) and Tiff(.tiff) image files is inspected. No optical character recognition is done for these file types. For AutoCADfiles,only the .dxf file type is inspected.
Processing attachments in ETR and DLP scenarios
You might be affected by this change if you use Data Loss Prevention (DLP) or Exchange Transport Rules (ETR) to inspect attachments. The content of Jpeg, Tiff, and AutoCAD files can no longer be extracted and inspected after the March 2024 security update is installed.
Example
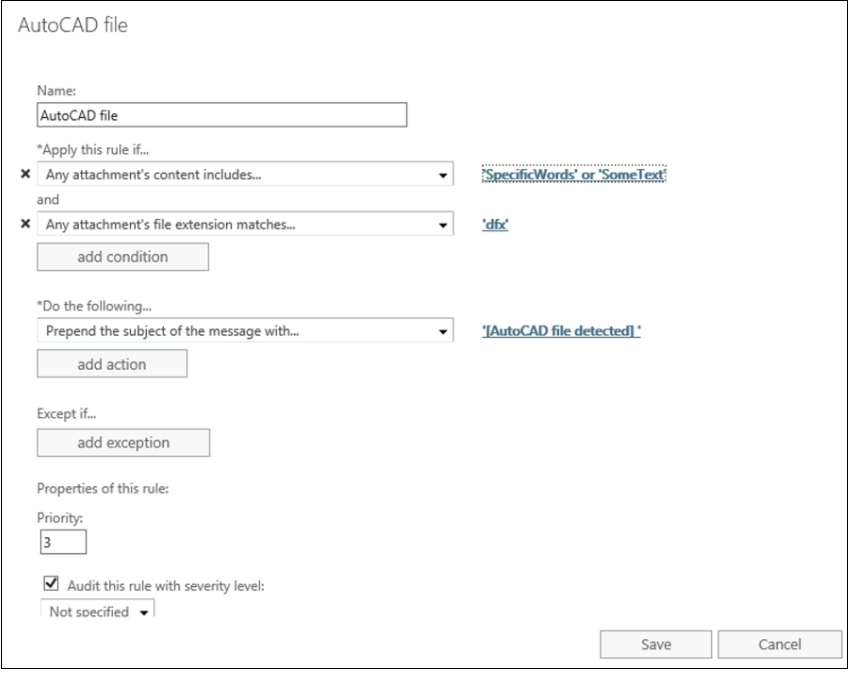
The following Exchange Transport Rule no longer works after the March 2024 security update is installed. Email will still be delivered. However, the subject is not prepended because the file cannot be inspected for the defined text.
-
Name: AutoCAD file
-
Apply this rule if… Any Attachment’s content includes… ‘SpecificWords’ or ‘SomeText’ Any attachment’s file extension matches… ‘dfx’
-
Do the following... Prepend the subject of the message with… ‘[AutoCAD file detected]’
-
Priority: 3
Workaround
To work around this issue, reactivate blocked file type processing after you install the March 2024 security update. We strongly recommend that you not override the default behavior that was introduced in the March 2024 security update if there are no functional issues that affect your organization's mail flow.
Microsoft is providing a PowerShell script for administrators to use if they want to override the default setting that disables OIT. The script enables OIT despite the update’s restrictions. You can find the script and detailed instructions for its use in this CSS-Exchange article.
If you encounter scenarios that are not described here but that are affected by the OutsideInModule disablement, you can contact the Exchange Server team at ExchOnPremFeedback[at]microsoft.com.