Windows Configuration System (WinCS) APIs for Secure Boot
Applies To
Original publish date: October 14, 2025
KB ID: 5068197
|
This article has guidance for:
Note: If you are an individual who owns a personal Windows device, please go to the article Windows devices for home users, businesses, and schools with Microsoft-managed updates. |
|
Availability of this support:
|
|
Change date |
Change description |
|
February 20, 2026 |
|
|
December 16, 2025 |
|
|
December 11, 2025 |
|
Secure Boot CLI using Windows Configuration System (WinCS)
Goal: Domain administrators can alternatively use the Windows Configuration System (WinCS) released with Windows OS updates to deploy the Secure Boot updates across domain-joined Windows clients and servers. It consists of a command-line interface (CLI) utility to query and apply Secure Boot configurations locally to a machine.
WinCS works off a configuration key that can be used with the command-line utility to modify the Secure Boot configuration state on the machine. Once applied, the next scheduled Secure Boot will perform actions according to the key.
First check if Secure Boot certificates are updated in your platform
You can check the status of Secure Boot using the Powershell command:
(Get-ItemProperty 'HKLM:\SYSTEM\CurrentControlSet\Control\SecureBoot\Servicing' -Name 'UEFICA2023Status').UEFICA2023Status
If the Status shows "Updated", then you don't need to run WinCS and can skip the steps below.
If the Certificates are not updated to 2023 versions, then the additional steps below apply.
WinCS supported platforms
The WinCS command-line utility is supported in Windows 10, version 21H2, Windows 10, version 22H2, Windows 10 1607, Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows 11, version 23H2, Windows 11, version 24H2, Windows 11, version 25H2.
This utility is available in the Windows updates released on and after October 28, 2025, for Windows 11, version 24H2 and Windows 11, version 23H2.
This utility is also available in the Windows updates released on and after November 11, 2025, for Windows 10, version 21H2, Windows 10, version 22H2, and Windows Server 2022.
For Windows Server 2019, this utility is shipped in the Windows updates released on and after January 13, 2026.
And for Windows Server 2016, Windows 10 1607, this utility is shipped in the Windows updates released on and after February 10, 2026.
Note: We are working on bringing this WinCS support to Windows 10 platforms. We will update this article as soon as the support is enabled.
Here’s the Secure Boot configuration feature key that domain admins will query and apply to devices through WinCS.
|
Feature name |
WinCS Key |
Description |
|
Feature_AllKeysAndBootMgrByWinCS |
F33E0C8E002 |
Enabling this key allows installation of the following Microsoft-provided Secure Boot new certificates on your device.
|
WinCS key value:
-
F33E0C8E002 – Secure Boot configuration state = Enabled
How to query Secure Boot configuration
Secure Boot configuration can be queried by opening a command prompt as an administrator and running this command:
WinCsFlags.exe /query --key F33E0C8E002
This will return the following information (on a clean machine):
Flag: F33E0C8E
Current Configuration: F33E0C8E001
State: Disabled
Pending Configuration: None
Pending Action: None
FwLink: https://aka.ms/getsecureboot
Available Configurations:
F33E0C8E002
F33E0C8E001
Notice the current configuration on a device is F33E0C8E001, which means the Secure Boot key is in Disabled state.
How to apply Secure Boot configuration
Secure Boot configuration can be applied by opening a command prompt as an administrator and running this command:
WinCsFlags.exe /apply --key "F33E0C8E002"
A successful application of the key should return the following information:
Flag: F33E0C8E
Current Configuration: F33E0C8E002
State: Enabled
Pending Configuration: None
Pending Action: None
FwLink: https://aka.ms/getsecureboot
Available Configurations:
F33E0C8E002
F33E0C8E001
How to audit Secure Boot configuration
To determine the state of the Secure Boot configuration later, you can re-run the initial query command by opening a command prompt as an administrator:
WinCsFlags.exe /query --key F33E0C8E002
The information returned will be similar to the following, depending on the state of the flag:
Flag: F33E0C8E
Current Configuration: F33E0C8E002
State: Enabled
Pending Configuration: None
Pending Action: None
FwLink: https://aka.ms/getsecureboot
Available Configurations:
F33E0C8E002
F33E0C8E001
Notice that the state of the key is now Enabled, and the current configuration is F33E0C8E002.
Note: Applying the Secure Boot key via WinCS does not mean that the Secure Boot certificate installation process has started or has finished. It merely indicates that the machine will proceed with Secure Boot updates when the Secure Boot servicing task (TPMTasks) runs on that machine at the next available opportunity. When TPMTasks runs on that machine, it will detect 0x5944 and carry out the update. By design, the Secure-Boot-Update scheduled task runs every 12 hours to process such Secure Boot update flags. Admins can also expedite by manually running the task or restarting, if desired.
You can also manually trigger the Secure Boot servicing task by following below steps:
-
Open a PowerShell prompt as an administrator and then run the following command:
Start-ScheduledTask -TaskName "\Microsoft\Windows\PI\Secure-Boot-Update"
-
Restart the device two times after running the command to confirm that the device is starting with the updated database of trusted signatures (DB).
-
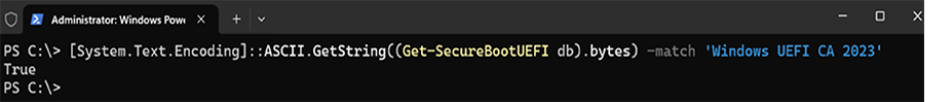
As a quick check if the Secure Boot DB update was successful, open a PowerShell prompt as an administrator and then run the following command:
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match 'Windows UEFI CA 2023'
If the command returns True, the update was successful. In the case of errors while applying the DB update, see the article KB5016061: Addressing vulnerable and revoked Boot Managers.
Note: This is checking only one CA and not all CAs.
-
To verify that all the certificates are updated, please refer to Secure Boot Certificate updates: Guidance for IT professionals and organizations and follow the guidance in the "Monitoring Event Logs" section. This section lists Event ID: 1801 and Event ID: 1808 which is a more complete way to audit that the certificates have been updated.