Summary
Security updates released on and after July 6, 2021 contain protections for a remote code execution vulnerability in the Windows Print Spooler service (spoolsv.exe) known as “PrintNightmare”, documented in CVE-2021-34527. After installing the July 2021 and later updates, non-administrators, including delegated admin groups like printer operators, cannot install signed and unsigned printer drivers to a print server. By default, only administrators can install both signed and unsigned printer drivers to a print server.
Note Before installing the July 2021 Out-of-band and later Windows updates containing protections for CVE-2021-34527, the printer operators' security group could install both signed and unsigned printer drivers on a printer server. Starting with the July 2021 Out-of-band update, administrator credentials will be required to install signed and unsigned printer drivers on a printer server. Optionally, to override all Point and Print Restrictions Group policy settings and ensure that only administrators can install printer drivers on a print server, configure the RestrictDriverInstallationToAdministrators registry value to 1.
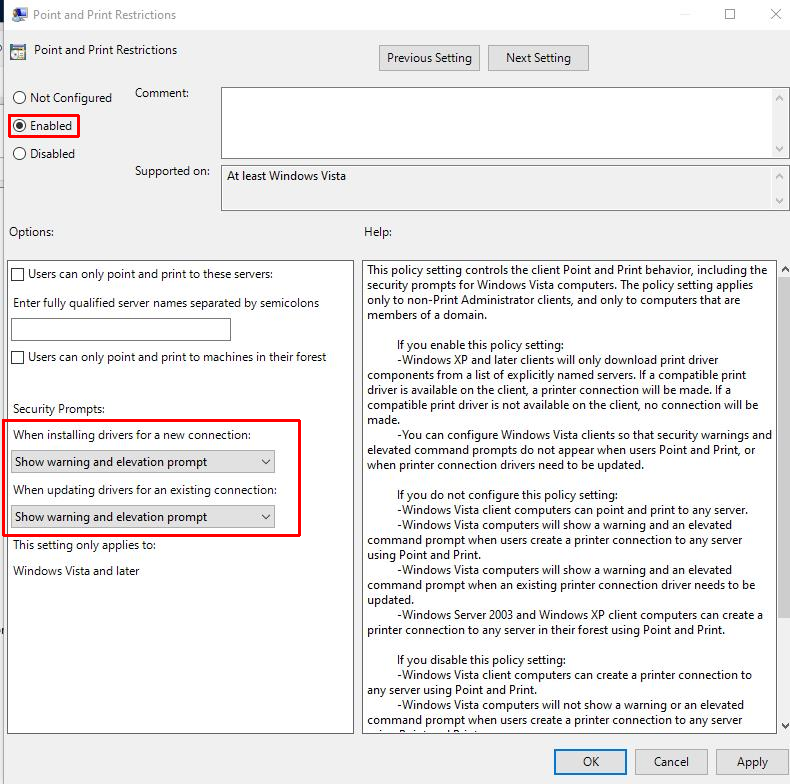
We recommend that you immediately install the latest Windows updates released on or after July 6, 2021 on all supported Windows client and server operating systems, starting with devices that currently host the print spooler service. Next, set the "When installing drivers for a new connection" and "When updating drivers for an existing connection" in the Point and Print Restrictions Group Policy setting to "Show warning and elevation prompt".
Resolution
-
Install the July 2021 Out-of-band or later updates.
-
Check if the following conditions are true:
-
Registry Settings: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
-
NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
-
UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
-
-
Group Policy: You have not configured the Point and Print Restrictions Group Policy.
If both conditions are true, then you are not vulnerable to CVE-2021-34527 and no further action is needed. If either condition is not true, you are vulnerable. Follow the steps below to change the Point and Print Restrictions Group Policy to a secure configuration.
-
Open the group policy editor tool and go to Computer Configuration > Administrative Templates > Printers.
-
Configure the Point and Print Restrictions Group Policy setting as follows:
-
Set the the Point and Print Restrictions Group Policy setting to "Enabled".
-
"When installing drivers for a new connection": "Show warning and elevation prompt".
-
"When updating drivers for an existing connection": "Show warning and elevation prompt".
-
Important We strongly recommend that you apply this policy to all machines that host the print spooler service.
Restart requirements: This policy change does not require a restart of the device or the print spooler service after applying these settings.
3. Use the following registry keys to confirm that the Group Policy was applied correctly:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
-
NoWarningNoElevationOnInstall = 0 (DWORD)
-
UpdatePromptSettings = 0 (DWORD)
Warning Setting these to non-zero values make the devices on which you've installed the CVE-2021-34527 update vulnerable.
Note Configuring these settings does not disable the Point and Print feature.
4. [Recommended] Override Point and Print Restrictions so that only administrators can install print drivers on printer servers. This is done using the registry key RestrictDriverInstallationToAdministrators. Updates released July 6, 2021 or later have a default of 0 (disabled) until updates released August 10, 2021. Updates released August 10, 2021 or later have a default of 1 (enabled). For more information on how to set RestrictDriverInstallationToAdministrators and other print related recommendations, see KB5005652—Manage new Point and Print default driver installation behavior (CVE-2021-34481)
More information
Do the fixes for CVE-2021-34527 impact the default Point and Print driver installation scenario for a client device that is connecting to and installing a print driver for a shared network printer?
No, the fixes for CVE-2021-34527 do not directly affect the default Point and Print driver installation scenario for a client device that is connecting to and installing a print driver for a shared network printer. In this case, a client device connects to a print server and downloads and installs the drivers from that trusted server. This scenario is different from the vulnerable scenario where an attacker is trying to install a malicious driver on the print server itself, either locally or remotely.