Original publish date: August 15, 2025
KB ID: 5065996
In this article
Introduction
The Policy-Based Removal of Pre-installed Microsoft Store Apps feature streamlines the removal of pre-installed Microsoft Store apps in Windows Enterprise and Education editions. IT administrators can use new Group Policy or MDM Configuration Service Provider (CSP) settings to select apps for removal from a predefined list. Apps are removed at the device level, not the user level.
We appreciate any feedback regarding this feature and are excited to have your help!
Installing Windows 11 Insider Preview Dev Build
Option 1
-
On a test device, go to the Windows Insider Program page and sign in with your Microsoft account.
-
Accept the terms and conditions to enroll your account.
-
On the test device, go to Settings > Update & Security > Windows Insider Program, link your account, and then choose the Dev channel.
-
Restart the device, if prompted.
-
Go to Settings > Update & Security > Windows Update > Check for updates. Your device will download the latest Insider Preview build for your chosen channel.
Option 2
If you prefer a clean installation, download the ISO from the Windows Insider Preview ISO page.
Policy control
IT administrators can use Group Policy and MDM on Windows 11 to enable/disable removal of pre-installed Microsoft Store apps.
Group Policy settings
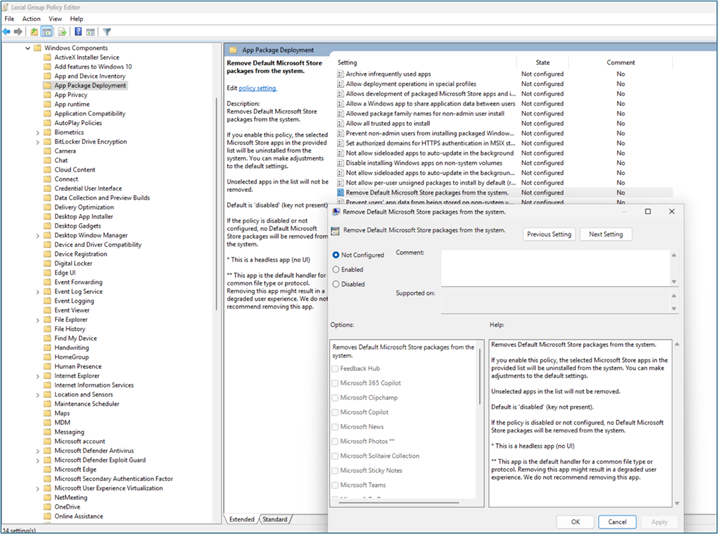
To access Group Policy settings, open the Group Policy Editor and navigate to Computer Configuration > Administrative Templates > Windows Components > App Package Deployment.
Access MDM settings
This feature is currently unavailable. When this feature becomes generally available, you can search for Remove Default Microsoft Store packages settings in the Settings picker. For now, you need to create a custom policy.
Create a custom MDM policy (Intune example)
To create a custom MDM policy for Enable Microsoft Default Store packages policy, follow these steps:
-
Navigate to the Devices Configuration page on Intune.
-
Create a new policy.
-
Under the Policy tab, click on + Create -> New Policy.
-
-
Select the Platform and Profile Type.
-
Platform: Select Win 10 and later.
-
Profile Type: Choose Templates.
-
Templates window: Click Custom and then select Create.
-
-
Basic policy configuration.
-
Basics tab:
-
Name: Enter a descriptive name such as RemovalMicrosoftPreinstalledApps Policy.
-
Description: You can skip this or enter a brief note such as Removal preinstalled apps policy.
-
-
Click Next.
-
-
Configuration settings
-
Click Add to configure the policy.
-
Add Row Side tab.
-
Setting Name: Enter a name such as RemoveMicrosoftPreinstalledApps.
-
Description: You can skip this field.
-
OMA URI: Provide the CSP URI:
ISO v1:
./Device/Vendor/MSFT/Policy/Config/ApplicationManagement/RemoveDefaultMicrosoftStorePackages
-
Data Type: Select String (as this is an ADMX-backed policy).
-
Value: Enter the below data (“true” means remove the app)
<enabled/><data id="WindowsFeedbackHub" value="false"/> <data id="MicrosoftOfficeHub" value="false"/> <data id="Clipchamp" value="false"/> <data id="Copilot" value="false"/> <data id="BingNews" value="true"/> <data id="Photos" value="false"/> <data id="MicrosoftSolitaireCollection" value="true"/> <data id="MicrosoftStickyNotes" value="true"/> <data id="MSTeams" value="false"/> <data id="Todo" value="false"/> <data id="BingWeather" value="true"/> <data id="OutlookForWindows" value="false"/> <data id="Paint" value="false"/><data id="QuickAssist" value="false"/> <data id="ScreenSketch" value="false"/> <data id="WindowsCalculator" value="false"/> <data id="WindowsCamera" value="false"/> <data id="MediaPlayer" value="false"/> <data id="WindowsNotepad" value="false"/> <data id="WindowsSoundRecorder" value="false"/> <data id="WindowsTerminal" value="false"/> <data id="GamingApp" value="true"/> <data id="XboxIdentityProvider" value="true"/> <data id="XboxSpeechToTextOverlay" value="true"/> <data id="XboxTCUI" value="true"/>Note: The packages with true value are the default apps selected for removal. You can update the package values from false to true or vice versa, based on your organization's requirements.
-
-
Click Save and then click Next.
-
-
Assignments
-
Under Assignments, click Included Groups.
-
Select the group name you created earlier.
-
Click Next.
-
-
Skip Applicability Rules
-
Skip the applicability rules and click Next.
-
-
Review and Create
-
Under Review and Create, review the information (policy name, assigned group, and so forth).
-
Click Create. Your policy has now been created!
-
Policy-Based Removal of Pre-installed Microsoft Store Apps
This section guides you through policy-based app removal on Enterprise or Education edition devices. Policy-based removal is supported on Microsoft Entra and Microsoft Entra-Hybrid joined devices. Before proceeding, ensure you have the following:
-
A Windows 11 device with the Dev channel release.
-
A Microsoft Entra account.
Enable the removal policy
Policy-Based Removal of Pre-installed Microsoft Store Apps is disabled by default for Microsoft Entra accounts. The new Remove Default Microsoft Store packages policy must be explicitly enabled, from MDM via OMA URI or by enabling the Group Policy via Configuration Manager.
Select the apps for removal
GP Option:
-
Open the Group Policy Editor and navigate to Computer Configuration > Administrative Templates > Windows Components > App Package Deployment > Remove Default Microsoft Store apps.
-
Select the apps for removal.
-
Log off and then log back in to the device.
-
The apps that were selected for removal should no longer be installed.
CSP Option:
-
Select the apps to remove in the custom CSP policy you created in the Create Custom MDM Policy (Intune Example) section by changing their settings to true.
-
Log off and then log back in to the device.
-
The apps that were selected for removal should no longer be installed.
Verify the removal was successful
To confirm the removal of the packages was successful, do one of the following:
-
Log-in to the device, verify the apps selected in the Remove Default Microsoft Store packages policy are not installed, or
-
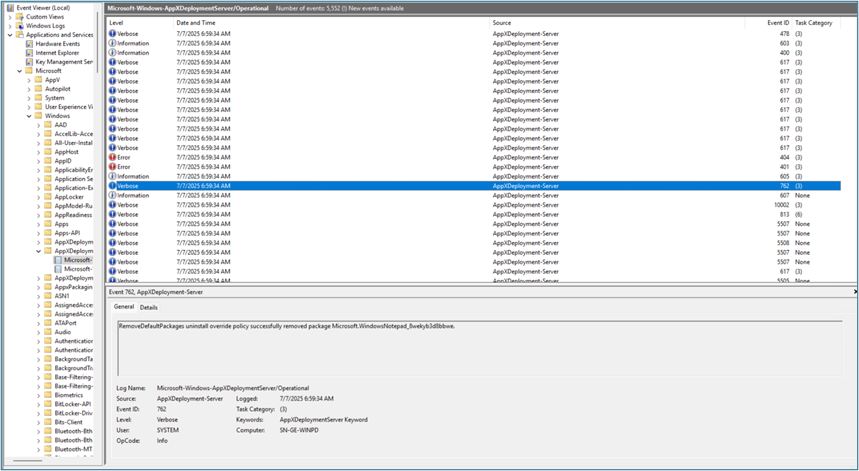
View the event logs. The event logs for app removal can be found by opening the event viewer and navigating to Applications and Service Logs > Microsoft > Windows > AppxDeployment-Server > Microsoft-Windows-AppxDeploymentSever/Operational.
Once an app has been removed, an Event ID: 762 will be logged. The text of the event will start with “RemoveDefaultPackages uninstall override policy successfully removed package.”
Reinstallation of an app
To reinstall an app removed by this policy, first clear the policy selection for the app. Then sync the policy and reinstall the app from the Microsoft Store or redeploy it using your management tool.
Note To clear the policy for an app when using GP, open your GP management tool and de-select the app in the Remove Default Microsoft Store Packages from the system setting. To clear the policy for an app when using the custom CSP, edit the CSP to change the app setting to false.
Other validations
-
Sysprep After confirming the device has no packages opted in Remove Default Microsoft Store packages policy, run Sysprep. Ensure the removed packages are still unavailable following further Windows image customization.
-
Push Button Reset (PBR): After confirming the device has no packages opted in Remove Default Microsoft Store packages policy, use Reset this PC in System Settings. Choose either Keep my settings or Remove everything, confirming that removed packages remain unavailable after reset.
Providing Feedback
-
In the event you find an issue while testing, we want to hear about anything and everything. To provide feedback, use the Feedback Hub.
-
Start the Feedback Hub app (log in with your MSA credentials)
-
Click the Feedback tab in the hamburger menu.
-
On the Feedback tab, click Add new feedback.
-
Select Problem and enter the issue that you are experiencing. Use the optional text box to enter as much detail as possible regarding the issue.
-
Select Developer Platform as the category and App deployment as the sub-category.
-
Click Submit to finish the log collection and upload process.
Limitations
-
Devices that support multi-user sessions are not supported.