Summary
Brute force attacks are one of the top three ways that Windows computers are attacked today. However, Windows devices currently do not allow built-in local Administrator accounts to be locked out. This creates scenarios in which, without the proper network segmentation or the presence of an intrusion detection service, the built-in local Administrator account can be subjected to unlimited brute force attacks to try to determine the password. This can be done by using Remote Desktop Protocol (RDP) over the network. If the passwords are not long or complex, the time it would take to perform such an attack is becoming trivial by using modern CPUs and GPUs.
In an effort to prevent further brute force attacks, we are implementing account lockouts for Administrator accounts. Beginning in the October 11, 2022, or later Windows cumulative updates, a local policy will be available to enable built-in local Administrator account lockouts. This policy can be found under Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\Account Policies\Account Lockout Policies.
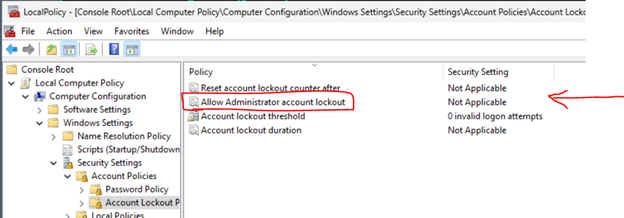
For existing computers, setting this value to Enabled by using a local or domain GPO will provide the ability to lock out the built-in local Administrator account. Such environments should also consider setting the other three policies under Account Lockout Policies. Our baseline recommendation is to set them to 10/10/10. This means that an account would be locked out after 10 failed attempts within 10 minutes and the lockout would last for 10 minutes. After that, the account would be unlocked automatically.
Note The new lockout behavior only affects network logons, such as RDP attempts. Console logons will still be allowed during the lockout period.
For new computers on Windows 11, version 22H2, or any new computers that include the October 11, 2022, Windows cumulative updates before the initial setup, these settings will be set by default at system setup. This occurs when the SAM database is first instantiated on a new computer. So, if a new computer was set up and then had the October updates installed later, it will not be secure by default. It will require the policy settings as described earlier. If you do not want these policies to apply to your new computer, you can set this local policy or create a group policy to apply the Disabled setting for "Allow Administrator account lockout."
Additionally, we are now enforcing password complexity on new computer if a built-in local Administrator account is used. The password must have at least two of the three basic character types (lowercase, uppercase, and numerals). This will help further protect these accounts from being compromised because of a brute force attack. However, if you want to use a less complex password, you can still set the appropriate password policies in Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\Account Policies\Password Policy.
More information
The added changes support the DOMAIN_LOCKOUT_ADMINS and DOMAIN_PASSWORD_COMPLEX flag for the built-in local Administrator account. For more information, see DOMAIN_PASSWORD_INFORMATION (ntsecapi.h).
|
Value |
Meaning |
|
DOMAIN_LOCKOUT_ADMINS 0x00000008L |
Allows the built-in local Administrator account to be locked out from network logons. |
|
DOMAIN_PASSWORD_COMPLEX 0x00000001L |
The password must have a mix of at least two of the following types of characters:
|










