|
Change date |
Change description |
|
March 20, 2024 |
|
|
March 21, 2024 |
|
|
March 22, 2024 |
|
Introduction
This article is a supplement to the following article which will be updated in April 2024:
-
KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932
This supplement describes the updated step-by-step procedure to deploy new mitigations against the BlackLotus UEFI boot-kit tracked by CVE-2023-24932 and includes testing guidance for your environment.
To help protect against the malicious abuse of vulnerable boot managers, we must deploy a new UEFI Secure Boot signing certificate to the device firmware and to revoke trust in the firmware of the current signing certificate. Doing this will cause all existing, vulnerable boot managers to be untrusted by Secure Boot enabled devices. This guide will help you with that process.
The three mitigation steps outlined in this guide are as follows:
-
Updating DB: A new PCA (PCA2023) certificate will be added to the Secure Boot DB which will enable a device to boot media signed by this certificate.
-
Installation of boot manager: The existing PCA2011-signed boot manager will be replaced by the PCA2023-signed boot manager.Both boot managers are included in the April 2024 security updates.
-
DBX revocation of PCA2011: A deny entry will be added to the Secure Boot DBX preventing boot managers signed with PCA2011 from booting.
Note The Servicing Stack software that applies these three mitigations will not allow for the mitigations to be applied out of order.
Does this apply to me?
This guide applies to any devices with Secure Boot enabled and all existing recovery media for these devices.
If your device is running Windows Server 2012 or Windows Server 2012 R2, be sure to read the “Known Issues” section before continuing.
Before you start
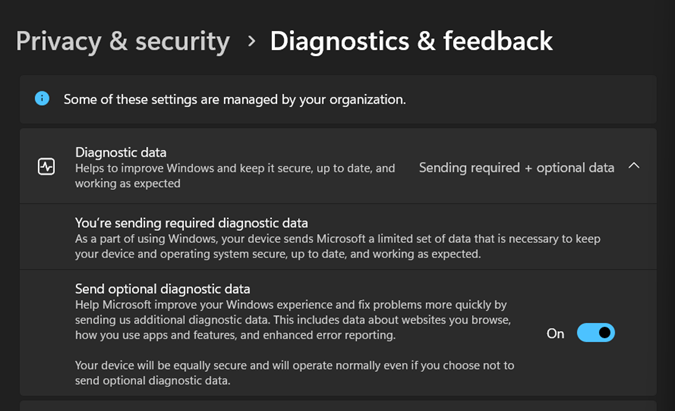
Enable Optional Diagnostic Data
Please turn on the "Send optional diagnostic data" setting by performing the following steps:
-
In Windows 11, go to Start > Settings > Privacy & security > Diagnostics & feedback.
-
Turn on Send optional diagnostic data.
For more information, see Diagnostics, feedback, and privacy in Windows.
NOTE Make sure you have internet connectivity during and for some time after validation.
Do a test pass
After installing the April 2024 Windows updates, and before going through the steps to opt-in, make sure to do a test pass to verify the integrity of your system:
-
VPN: Verify that VPN access to corporate resources and network is functional.
-
Windows Hello: Logon to the Windows device by using your normal procedure (face/fingerprint/PIN).
-
BitLocker: System starts normally on BitLocker-enabled systems without any BitLocker recovery prompt during startup.
-
Device Health Attestation: Verify that devices relying on Device Health Attestation correctly attest their status.
Known Issues
For Windows Server 2012 and Windows Sever 2012 R2 only:
-
TPM 2.0 based systems cannot deploy the mitigations released in the April 2024 security patch because of known compatibility issues with TPM measurements. The April 2024 updates will block mitigations #2 (boot manager) and #3 (DBX update) on affected systems.
-
Microsoft is aware of the issue and an update will be released in the future to unblock TPM 2.0 based systems.
-
To check your TPM version, right-click Start, click Run, and then type tpm.msc. On the bottom-right of the center pane under TPM Manufacturer Information, you should see a value for Specification Version.
Opt-in Validation Steps
The rest of this article discusses the testing for opting-in devices to the mitigations. The mitigations are not enabled by default. If your enterprise plans to enable these mitigations, please run through the following validation steps to verify the device compatibility.
-
Deploy the April 2024 pre-release security update.
-
Open an Administrator command prompt and set the registry key to perform the update to the DB by typing the following command, and then press Enter:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x40 /f
-
Restart the device two times.
-
Verify that DB is successfully updated by making sure the following command returns True. Run the following PowerShell command as an Administrator:
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI db).bytes) -match 'Windows UEFI CA 2023'
-
Open an Administrator command prompt and set the registry key to download and install the PCA2023-signed boot manager:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x100 /f
-
Restart the device two times.
-
As Administrator, mount the EFI partition to get it ready for inspection:
mountvol s: /s
-
Validate that "s:\efi\microsoft\boot\bootmgfw.efi" is signed by PCA2023. To do this, follow these steps:
-
Click Start, type command prompt in the Search box, and then click Command Prompt.
-
In the Command Prompt window, type the following command and then press Enter.
copy S:\EFI\Microsoft\Boot\bootmgfw.efi c:\bootmgfw_2023.efi
-
In File Manager, right-click the file C:\bootmgfw_2023.efi, click Properties, and then select the Digital Signatures tab.
-
In the Signature list, confirm that the certificate chain includes Windows UEFI 2023 CA.
-
CAUTION: This step deploys the DBX revocation to untrust old, vulnerable boot managers signed by using the Windows Production PCA2011. Devices with this revocation applied will no longer boot from existing recovery media and network boot (PXE/HTTP) servers that do not have updated boot manager components.
If your device gets into a non-bootable state, follow the steps in the “Recovery and Restore procedures” section to reset the device to a pre-revocation state.
After applying the DBX, if you want to return the device to its previous Secure Boot state, follow the "Recovery and Restore procedures" section.
Apply the DBX mitigation to untrust the Windows Production PCA2011 certificate in Secure Boot:
-
Open an Administrator command prompt and set the registry key to place the revocation for PCA2011 in DBX:
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Secureboot /v AvailableUpdates /t REG_DWORD /d 0x80 /f
-
Restart your device two times and confirm that it has fully restarted.
-
Verify that the DBX mitigation has been applied successfully. To do this, run the following PowerShell command as an Administrator and make sure the command returns True:
[System.Text.Encoding]::ASCII.GetString((Get-SecureBootUEFI dbx).bytes) -match 'Microsoft Windows Production PCA 2011'
Or, look for the following event in the Event Viewer:
Event log
System
Event source
TPM-WMI
Event ID
1037
Level
Information
Event message text
Secure Boot Dbx update to revoke Microsoft Windows Production PCA 2011 is applied successfully
-
Perform the test pass items from the “Before you start” section and make sure all systems are behaving normally.
Registry key reference
|
Command |
Purpose |
Comments |
|
Installs the DB update to allow the PCA2023-signed boot manager |
|
Command |
Purpose |
Comments |
|
Installs the PCA2023-signed bootmgr |
Value only honored after 0x40 step completed |
|
Command |
Purpose |
Comments |
|
Installs the DBX update which revokes PCA2011 |
Value only honored after both 0x40 & 0x100 steps completed |
Results and Feedback
Send email to suvp@microsoft.com with testing results, questions, and feedback.
Recovery and Restore procedures
When performing recovery procedures, share the following data with Microsoft:
-
Screen shot of the boot failure observed.
-
Steps performed that led to the device becoming not bootable.
-
Details of the device configuration.
When performing a restore procedure, suspend BitLocker before starting the procedure.
If something goes wrong during this process and you are unable to start your device or you need to start from external media (for example, thumb drive or PXE boot), try the following procedures.
-
Turn off Secure Boot This procedure differs between PC manufacturers and models. Enter your PCs UEFI BIOS menu and navigate to the Secure Boot setting and switch it off. Check documentation from your PC manufacturer for specifics on this process. For more information, see Disabling Secure Boot.
-
Clear Secure Boot Keys If the device supports clearing the Secure Boot keys or resetting Secure Boot keys to factory defaults, perform this action now. Your device should start now but note that it is vulnerable to boot-kits malware. Make sure to complete step 5 at the end of this recovery process to re-enable Secure Boot.
-
Try to start Windows from the system disk.
-
If BitLocker is enabled and goes into recovery, enter your BitLocker recovery key.
-
Logon to Windows.
-
Run the following commands from Administrator command prompt to restore the boot files in EFI system boot Partition:
Mountvol s: /s del s:\EFI\Microsoft\*.* /f /s /q bcdboot %systemroot% /s S:
-
Running BCDBoot should return “Boot files successfully created.“
-
If BitLocker is enabled, suspend BitLocker.
-
Restart the device.
-
-
If step 3 does not successfully recover the device, re-install Windows.
-
Start from existing recovery media.
-
Proceed to install Windows using the recovery media.
-
Logon to Windows.
-
Restart to verify device starts successfully to Windows.
-
-
Re-enable Secure Boot and Restart the device. Enter your devicce UEFI menu and navigate to the Secure Boot setting and turn it on. Check documentation from your device manufacturer for specifics on this process. For more information, see Re-enable Secure Boot.
-
If Windows start continues to fail, enter the UEFI BIOS again and turn off Secure Boot.
-
Start Windows.
-
Share contents of DB, DBX with Microsoft.
-
Open PowerShell in Administrator mode.
-
Capture the DB:
Get-SecureBootUEFI -name:db -OutputFilePath DBUpdateFw.bin
-
Capture the DBX:
Get-SecureBootUEFI -name:dbx –OutputFilePath dbxUpdateFw.bin
-
Share the files DBUpdateFw.bin and dbxUpdateFw.bin generated in Steps 8b and 8c.
-