Important This article contains information that shows you how to help lower security settings or how to turn off security features on a computer. You can make these changes to work around a specific problem. Before you make these changes, we recommend that you evaluate the risks that are associated with implementing this workaround in your particular environment. If you implement this workaround, take any appropriate additional steps to help protect the computer.
Summary
This security update includes improvements and fixes in the functionality of Windows 10. It also resolves the following vulnerabilities in Windows:
-
3177356 MS16-095: Cumulative security update for Internet Explorer: August 9, 2016
-
3177358 MS16-096: Cumulative security update for Microsoft Edge: August 9, 2016
-
3177393 MS16-097: Security update for Microsoft graphics component: August 9, 2016
-
3178466 MS16-098: Security update for kernel mode drivers: August 9, 2016
-
3178465 MS16-101: Security update for Windows authentication methods: August 9, 2016
-
3182248 MS16-102: Security update for Microsoft Windows PDF library: August 9, 2016
-
3182332 MS16-103: Security update for ActiveSyncProvider: August 9, 2016
Windows 10 updates are cumulative. Therefore, this package contains all previously released fixes.If you have installed earlier updates, only the new fixes that are contained in this package will be downloaded and installed on your computer. If you are installing a Windows 10 update package for the first time, the package for the x86 version is 366 MB and the package for the x64 version is 776 MB.
More Information
Known issues in this security update
-
Known issue 1 The security updates that are provided in MS16-101 and newer updates disable the ability of the Negotiate process to fall back to NTLM when Kerberos authentication fails for password change operations with the STATUS_NO_LOGON_SERVERS (0xc000005e) error code. In this situation, you may receive one of the following error codes.
Hexadecimal
Decimal
Symbolic
Friendly
0xc0000388
1073740920
STATUS_DOWNGRADE_DETECTED
The system detected a possible attempt to compromise security. Please make sure that you can contact the server that authenticated you.
0x4f1
1265
ERROR_DOWNGRADE_DETECTED
The system detected a possible attempt to compromise security. Please make sure that you can contact the server that authenticated you.
Workaround If password changes that previously succeeded fail after the installation of MS16-101, it's likely that password changes were previously relying on NTLM fallback because Kerberos was failing. In order to change passwords successfully by using Kerberos protocols, follow these steps:
-
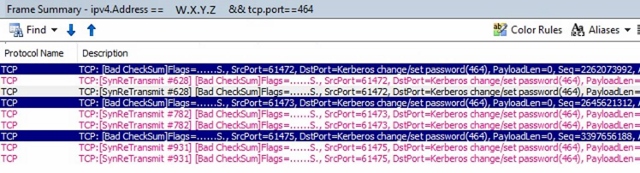
Configure open communication on TCP port 464 between clients that have MS16-101 installed and the domain controller that is servicing password resets. Read-only domain controllers (RODCs) can service self-service password resets if the user is allowed by the RODCs password replication policy. Users who are not allowed by the RODC password policy require network connectivity to a read/write domain controller (RWDC) in the user account domain. Note To check whether TCP port 464 is open, follow these steps:
-
Create an equivalent display filter for your network monitor parser. For example:
-
In the results, look for the "TCP:[SynReTransmit" frame.
-
-
Make sure that the target Kerberos names are valid. (IP addresses are not valid for the Kerberos protocol. Kerberos supports short names and fully qualified domain names.)
-
Make sure that service principal names (SPNs) are registered correctly. For more information, see Kerberos and Self-Service Password Reset.
-
-
Known issue 2 We know about an issue in which programmatic password resets of domain user accounts fail and return the STATUS_DOWNGRADE_DETECTED (0x800704F1) error code if the expected failure is one of the following:
-
ERROR_INVALID_PASSWORD
-
ERROR_PWD_TOO_SHORT (rarely returned)
-
STATUS_WRONG_PASSWORD
-
STATUS_PASSWORD_RESTRICTION
The following table shows the full error mapping.
Hexadecimal
Decimal
Symbolic
Friendly
0x56
86
ERROR_INVALID_PASSWORD
The specified network password is not correct.
0x267
615
ERROR_PWD_TOO_SHORT
The password that was provided is too short to meet the policy of your user account. Please provide a longer password.
0xc000006a
-1073741718
STATUS_WRONG_PASSWORD
When you try to update a password, this return status indicates that the value that was provided as the current password is incorrect.
0xc000006c
-1073741716
STATUS_PASSWORD_RESTRICTION
When you try to update a password, this return status indicates that some password update rule was violated. For example, the password may not meet the length criteria.
0x800704F1
1265
STATUS_DOWNGRADE_DETECTED
The system cannot contact a domain controller to service the authentication request. Please try again later.
0xc0000388
-1073740920
STATUS_DOWNGRADE_DETECTED
The system cannot contact a domain controller to service the authentication request. Please try again later.
ResolutionMS16-101 has been re-released to address this issue. Install the latest version of the updates for this bulletin to resolve this issue.
-
-
Known issue 3 We know about an issue in which programmatic resets of local user account password changes may fail and return the STATUS_DOWNGRADE_DETECTED (0x800704F1) error code. The following table shows the full error mapping.
Hexadecimal
Decimal
Symbolic
Friendly
0x4f1
1265
ERROR_DOWNGRADE_DETECTED
The system cannot contact a domain controller to service the authentication request. Please try again later.
ResolutionMS16-101 has been re-released to address this issue. Install the latest version of the updates for this bulletin to resolve this issue.
-
Known issue 4 Passwords for disabled and locked-out user accounts cannot be changed using the negotiate package. Password changes for disabled and locked-out accounts will still work when using other methods such as when using an LDAP modify operation directly. For example, the PowerShell cmdlet Set-ADAccountPassword uses an "LDAP Modify" operation to change the password and remains unaffected. Workaround These accounts require an administrator to make password resets. This behavior is by design after you install MS16-101 and later fixes.
-
Known issue 5 Applications that use the NetUserChangePassword API and that pass a servername in the domainname parameter will no longer work after MS16-101 and later updates are installed. Microsoft documentation states that providing a remote server name in the domainname parameter of the NetUserChangePassword function is supported. For example, the NetUserChangePassword function MSDN topic states the following:domainname [in]
A pointer to a constant string that specifies the DNS or NetBIOS name of a remote server or domain on which the function is to execute. If this parameter is NULL, the logon domain of the caller is used. However, this guidance has been superseded by MS16-101, unless the password reset is for a local account on the local computer. Post MS16-101, in order for domain user password changes to work, you must pass a valid DNS Domain Name to the NetUserChangePassword API.
-
Known issue 6 After you apply this security update, and then you print multiple documents in succession, the first two documents may print successfully but the third and subsequent documents may not print. To resolve this issue, do either of the following:
-
Install update 3187022. For more information, click the following article number to view the article in the Microsoft Knowledge Base:
3187022 Print functionality is broken after any of the MS16-098 security updates are installed
-
Install update 3186987 from the Microsoft Update Catalog website.
This problem is also resolved in Microsoft Security Bulletin MS16-106.
-
-
Known issue 7 After you install the security updates that are described in MS16-101, remote, programmatic changes of a local user account password, and password changes across untrusted forest fail. This operation fails because the operation relies on NTLM fall-back which is no longer supported for nonlocal accounts after MS16-101 is installed. A registry entry is provided that you can use to disable this change. Warning This workaround may make a computer or a network more vulnerable to attack by malicious users or by malicious software such as viruses. We do not recommend this workaround but are providing this information so that you can implement this workaround at your own discretion. Use this workaround at your own risk. ImportantThis section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756How to back up and restore the registry in Windows To disable this change, set the NegoAllowNtlmPwdChangeFallback DWORD entry to use a value of 1 (one). Important Setting the NegoAllowNtlmPwdChangeFallback registry entry to a value of 1 will disable this security fix:
Registry value
Description
0
Default value. Fallback is prevented.
1
Fallback is always allowed. The security fix is turned off. Customers that are having issues with remote local accounts or untrusted forest scenarios can set the registry to this value.
To add these registry values, follow these steps:
-
Click Start, click Run, type regedit in the Open box, and then click OK.
-
Locate and then click the following subkey in the registry:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa
-
On the Edit menu, point to New, and then click DWORD Value.
-
Type NegoAllowNtlmPwdChangeFallback for the name of the DWORD, and then press ENTER.
-
Right-click NegoAllowNtlmPwdChangeFallback, and then click Modify.
-
In the Value data box, type 1 to disable this change, and then click OK. Note To restore the default value, type 0 (zero), and then click OK.
Status The root cause of this issue is understood. This article will be updated with additional details as they become available.
-
How to get this update
Important If you install a language pack after you install this update, you must reinstall this update. Therefore, we recommend that you install any language packs that you need before you install this update. For more information, see Add language packs to Windows.
Method 1: Windows Update
This update will be downloaded and installed automatically.
Method 2: Microsoft Update Catalog
To get the stand-alone package for this update, go to the Microsoft Update Catalog website.
Prerequisites
There are no prerequisites for installing this update.
Restart information
You must restart the computer after you apply this update.
Update replacement information
This update replaces the previously released update 3163912.
File Information
For a list of the files that are provided in this cumulative update, download the file information for cumulative update 3176492.
References
Learn about the terminology that Microsoft uses to describe software updates.