Windows Security provides built-in security options to help protect your device from malicious software attacks.
To access the features described below, tap the Windows Start button, type windows security, select it from the results, and then select Device security.
Notes: What you actually see on the Device security page may vary depending upon what your hardware supports.
-
For more info about Windows Security, see Stay protected with Windows Security.
-
For more info about Microsoft Defender Firewall, see Turn Microsoft Defender Firewall on or off.
-
For help with your password, see Change or reset your Windows password.
Core isolation
Core isolation provides added protection against malware and other attacks by isolating computer processes from your operating system and device. Select Core isolation details to enable, disable, and change the settings for core isolation features.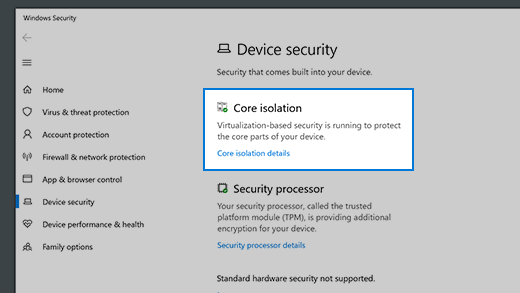
Memory integrity
Memory integrity is a feature of core isolation. By turning on the Memory integrity setting, you can help prevent malicious code from accessing high-security processes in the event of an attack.
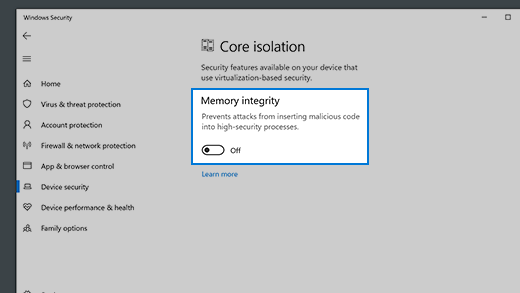
To learn more about Core Isolation and memory integrity see Core isolation.
Security processor
Your security processor provides additional encryption for your device.
Security processor details

This is where you’ll find info about the security processor manufacturer and version numbers, as well as about the security processor’s status. Select Security processor details for additional info and options.
Note: If you don't see a Security processor entry on this screen then it's likely that your device doesn't have the TPM (Trusted Platform Module) hardware necessary for this feature or that it's not enabled in UEFI (Unified Extensible Firmware Interface). Check with your device manufacturer to see if your device supports TPM and, if so, steps to enable it.
If your security processor isn't working properly, you can select the Security processor troubleshooting link to see any error messages and advanced options. For more information see: Security Processor troubleshooting.
Secure boot
Secure boot prevents a sophisticated and dangerous type of malware—a rootkit—from loading when you start your device. Rootkits use the same permissions as the operating system and start before it, which means they can completely hide themselves. Rootkits are often part of an entire suite of malware that can bypass local logins, record passwords and keystrokes, transfer private files, and capture cryptographic data.
You may have to disable secure boot to run some PC graphics cards, hardware, or operating systems such as Linux or earlier versions of Windows. For more info, see How to disable and re-enable secure boot.
Hardware security capability
At the bottom of the Device security screen, one of the following messages appears, indicating the security capability of your device.
Your device meets the requirements for standard hardware security
This means your device supports memory integrity and core isolation and also has:
-
TPM 2.0 (also referred to as your security processor)
-
Secure boot enabled
-
DEP
-
UEFI MAT
Your device meets the requirements for enhanced hardware security
This means that in addition to meeting all the requirements of standard hardware security, your device also has memory integrity turned on.
Your device has all Secured-core PC features enabled
Note: Prior to Windows 20H2 this message said "Your device exceeds the requirements for enhanced hardware security".
This means that in addition to meeting all the requirements of enhanced hardware security, your device also has System Management Mode (SMM) protection turned on.
Standard hardware security not supported
This means that your device does not meet at least one of the requirements of standard hardware security.
Improving hardware security
If the security capability of your device isn't what you'd like it to be, you might need to turn on certain hardware features (such as secure boot, if supported) or change the settings in your system's BIOS. Contact your hardware manufacturer to see what features are supported by your hardware and how to activate them.










